Sophos thinks a single person or group called "ischhfd83" is behind more than a hundred backdoored malware variants targeting novice cybercriminals and video game cheaters looking to get their hands on malicious code.
Researchers linked the hundreds of GitHub repositories to a single Russian email address (ischhfd83[at]rambler[.]ru) after a Sophos customer inquired about a remote access trojan (RAT) featured in tech journalism and social media posts in April.
Sakura RAT supposedly had sophisticated evasion mechanisms built in, leading the customer to ask whether they were protected from it – a relatively common type of interaction, the researchers said.
However, looking deeper, they found that Sakura RAT didn't do much beyond installing infostealers and other RATs on the machine used by the would-be attacker. Dastardly stuff.
In fact, much of the code was copied from AsyncRAT, a widely used malware in cybercriminal circles, just with many of the forms left empty, meaning it wouldn't function as the attacker intended.
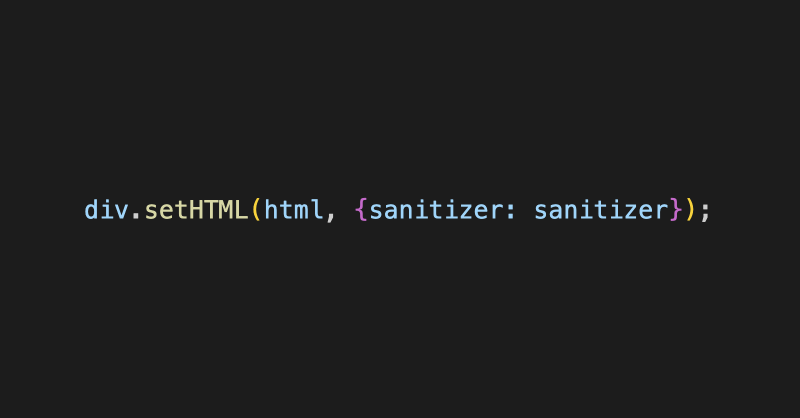
Sakura RAT also contained a PreBuild event in its Visual Basic project file containing commands that silently downloaded malware onto the user's device.
With their interest piqued, Sophos researchers looked into ischhfd83's other repositories, finding 141, 133 of which were backdoored in some way or another. 111 of these were backdoored using the same PreBuild event as Sakura RAT.
Fifty-eight percent were marketed as video game cheats. However, 24 percent were also listed under the guise of malware projects, exploits, or attack tools, Sophos said.
Ischhfd83's activity mainly spanned 2024-2025, and included projects targeting vulnerabilities disclosed as recently as April, but researchers think the campaign may have started as far back as 2022.
Aside from game cheats and malware, other projects related to bots (7 percent), cryptocurrency tools (5 percent), and other miscellaneous tools (6 percent).
Sophos noted that ischhfd83 "appears to be going to some lengths to make their backdoored repositories seem legitimate."
Looking at the YAML files in their repositories, the researchers found that the individual or individuals behind this campaign used a GitHub Actions workflow to automate commits to repos, with some registering nearly 60,000 in just a few months.
At a glance, it gives the impression of a regularly updated, trustworthy repository to a disinterested onlooker. However, those with keener eyes for detail would notice peculiarities.
Most repos had a small number of contributors, almost none of whom had repos of their own. Many had very similar usernames, some with just a few characters changed, and the small number of repo owners would only ever contribute to projects authored by others in that group. Also, these owners almost always had the same email address linked to Ischhfd83.
Sophos is not the first security firm to examine such campaigns. Checkmarx has been particularly hot on it since 2022, and Sophos has linked much of its work, either loosely or strongly, to Ischhfd83.
Campaigns investigated by Trend Micro, Kaspersky, Check Point, and others also share overlapping qualities, Sophos noted.
- Crims stole 40,000 people's data from our network, admits publisher Lee Enterprises
- 'Deliberate attack' deletes shopping app's AWS and GitHub resources
- You say Cozy Bear, I say Midnight Blizzard, Voodoo Bear, APT29 …
- Crooks fleece The North Face accounts with recycled logins
Ischhfd83's repos were characterized as an extension of the other vendors' work into what's known as a distribution-as-a-service operation.
While the distribution model for Ischhfd83's campaigns isn't clear, previous work has identified Discord and YouTube as primary means of spreading the links to malicious GitHub projects around to infect would-be cybercrooks.
Sophos said it's rare to see cybercriminals targeting their own, despite activity dating back years. However, just last month, it published its findings from a separate investigation, which found that DragonForce, a ransomware crew recently linked to major attacks on UK retailers, was defacing rivals' websites in a play for market dominance.
Sophos swiftly reported the backdoored Sakura RAT project to GitHub when it realized what was going on, and the platform took it down fairly swiftly, although the news reports and social media posts espousing its capabilities are still searchable.
The irony behind the attacker-on-attacker dynamic here might come as a refreshing breath of air to onlookers, but it could also have unintended consequences.
Most security pros would have the good sense to run projects like these in virtual environments, just in case of sneaky backdoors such as those used by Ischhfd83. But, for new open source enthusiasts exploring GitHub for the first time, they could easily be duped by the automated commits into thinking one of these projects was safe, Sophos warned.
"It remains unclear if this campaign is directly linked to some or all of the previous campaigns reported on, but the approach does seem to be popular and effective, and is likely to continue in one form or another.
"In the future, it's possible that the focus may change, and threat actors may target other groups besides inexperienced cybercriminals and gamers who use cheats." ®
.png)


![ChatGPT made me delusional [video]](https://www.youtube.com/img/desktop/supported_browsers/firefox.png)
