Written by João Cruz
Principal Security Research Scientist
Welcome to 2025, where thousands of internet-connected cameras meant to protect us are actually putting us at risk. In our latest research at Bitsight TRACE, we found over 40,000 exposed cameras streaming live on the internet. No passwords. No protections. Just out there. We first raised the alarm in 2023, and based on this latest study, the situation hasn’t gotten any better.
These cameras—intended for security or convenience—have inadvertently become public windows into sensitive spaces, often without their owners’ knowledge. No matter the reason why one individual or organization needs this kind of device, the fact that anyone can buy one, plug it in, and start streaming with minimal setup is likely why this is still an ongoing threat.
And it doesn’t take elite hacking to access these cameras; in most cases, a regular web browser and a curious mind are all it takes, meaning that 40,000 figure is probably just the tip of the iceberg. For our full findings, methodology, and recommendations, check out the report: “Big Brother Is Watching (And So Is Everyone Else).”
Key takeaways
- Bitsight TRACE has found more than 40,000 security cameras openly accessible on the internet, allowing anyone to view their live footage.
- The United States and Japan rank first and second for camera exposure.
- Most times, all that an attacker needs to spy on homes or even large organizations is just a web browser and the right IP address.
- We detected conversations on the dark web where bad actors were discussing exposed cameras.
Where are all these cameras? Everywhere.
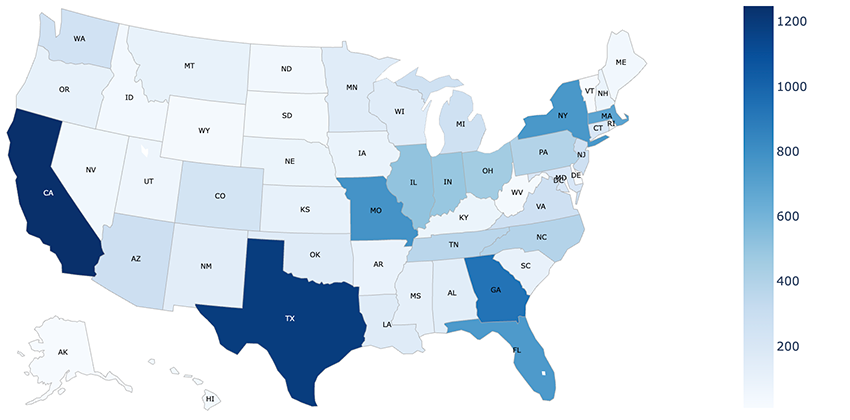
We scanned the entire internet for exposed HTTP-based and RTSP-based cameras. The United States leads the charge with roughly 14,000 exposed online cameras, followed by Japan, Austria, Czechia, and South Korea.

Given the high prevalence of exposed cameras in the United States, we also analyzed their distribution across each state:
From bird feeders to business espionage
Not all online cameras are bad: some people stream beaches or birdhouses on purpose. But here’s where things get problematic:
- Residential cameras watching front doors, backyards, and living rooms
- Office cameras disclosing whiteboards and screens full of confidential information
- Factory cameras showing manufacturing secrets
- Even public transportation cameras streaming passengers

Bad guys are paying attention
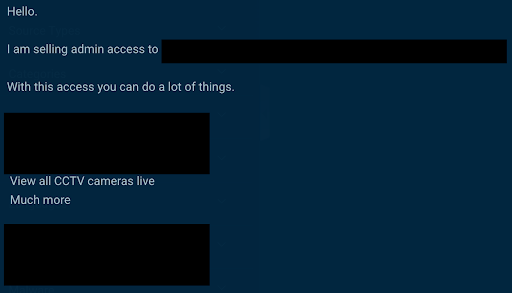
By leveraging the intelligence gathered by our awesome Cyber Threat Intelligence colleagues, we dug into dark web forums where people openly discuss tools and tactics to find and abuse these cameras (some even sell access). This isn’t hypothetical: this is happening right now.
What should I do to protect myself or my company?
If you have a security camera at home or manage surveillance cameras for your company, then taking the right precautions can make the difference between keeping your footage private and unintentionally broadcasting it to the world. Here are some simple but essential guidelines to ensure your cameras are secured:
- Check if your camera is accessible from the internet. Try accessing it from a device outside your home network. If you can reach it remotely without logging in through a secure app or VPN, it might be exposed.
- Change default usernames and passwords. Many cameras come with weak or publicly known default credentials. Set a strong, unique password.
- Disable remote access if you do not need it. If you only use your camera on your home network, there is no reason to allow outside connections.
- Keep firmware up to date. Manufacturers often release security updates that fix vulnerabilities. Regularly check for updates and install them.
Additionally, if you manage security cameras in your organizations:
- Restrict access with firewalls and VPNs. Ensure only authorized personnel can access camera feeds using a VPN or firewall rules that block access from untrusted sources.
- Monitor for unusual activity. Set up alerts for unexpected login attempts.
Read the full report to learn how we found these cameras, what’s being exposed, and why it matters, including jaw-dropping screenshots and the real-world security risks for everyday spaces like homes, offices, factories, and even hospitals.
And if you're concerned about your exposure, Bitsight can help. Bitsight provides intel on this in our portal under the Open Ports risk vector. Still have questions? Talk our team.
.png)