Data breaches aren't all the uncommon. We've already reported on three within the year, including Coinbase in May, Grubhub in February, and DeepSeek in late January.
Although those leaks, or rather, all leaks, are serious in nature, none compare to what security researchers have just uncovered.

Related
Take back control: A quick guide to data breach prevention
It's always a good idea to be aware of the latest data breaches
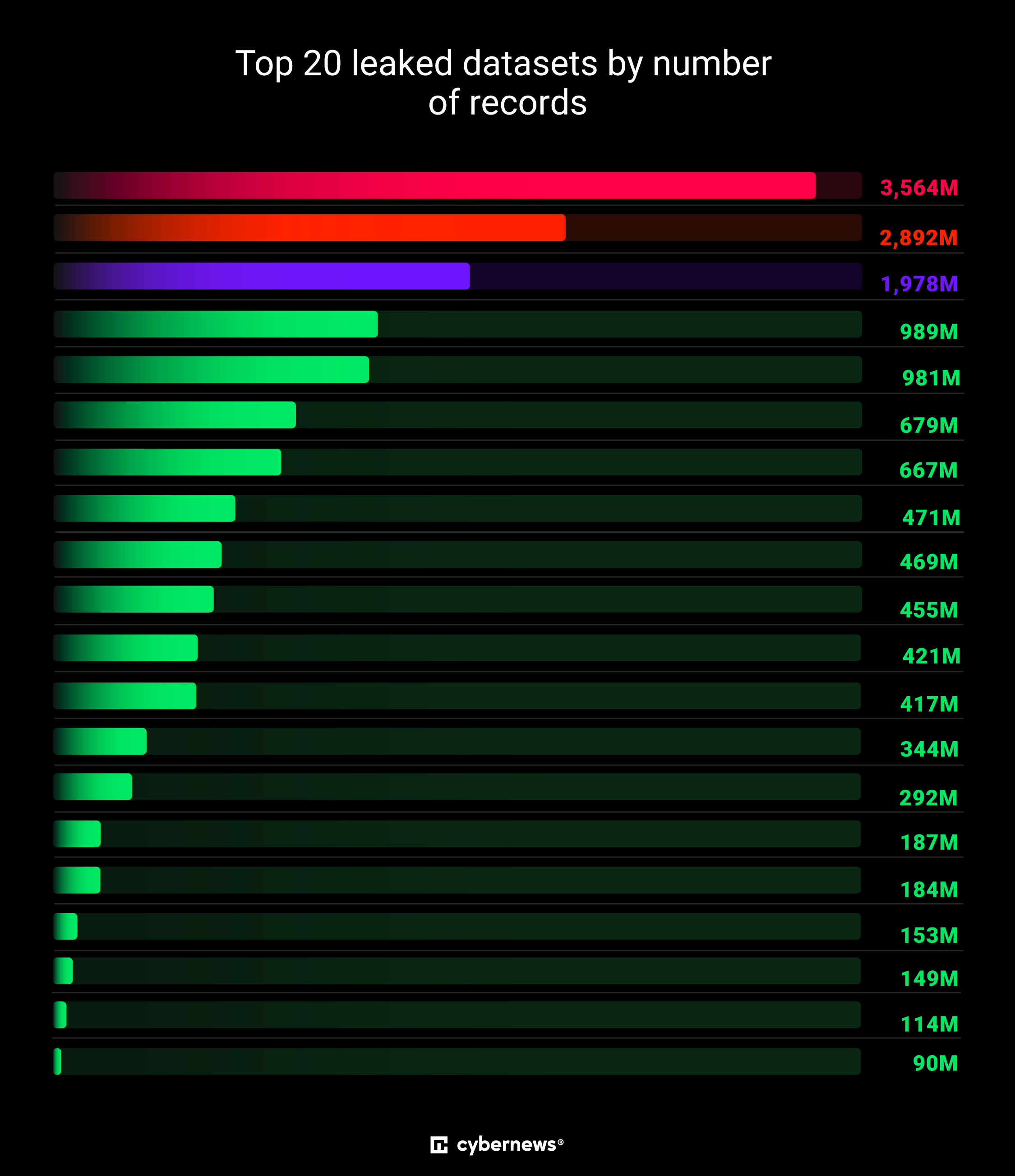
According to a new report from CyberNews, it has discovered a staggering collection of 30 exposed databases containing anywhere between tens of millions to over 3.5 billion records each. These were left exposed on the internet.
In total, those 30 exposed databases contain roughly "16 billion records," reads the report. Said records include accounts from major platforms like Google, Apple, Telegram, and more.
The report adds that only one of the exposed sets had been reported publicly in the past, and that included 184 million records. That, however, "barely scratches" the top 20 of what CyberNews uncovered.
For what it's worth, as of February 2025, there were over 5.56 billion internet users worldwide. Considering the compiled leak contains 16 billion records, it's safe to say that many internet users likely have multiple exposed accounts. That is also precisely why the actual scope and count of potentially impacted accounts remains unclear.
Source: CyberNews
This is not just a leak – it’s a blueprint for mass exploitation. With over 16 billion login records exposed, cybercriminals now have unprecedented access to personal credentials that can be used for account takeover, identity theft, and highly targeted phishing.
Most of the exposed datasets are a compilation of information from stealer malware, credential-stuffing sets, and repackaged leaks — this isn't a singular leak from one compromised source.
Additionally, most of the datasets list the exposed data in a clear format: a URL, login details, and a password. This is precisely how modern 'infostealers' collect data. Access to such data serves as prime fuel for not just phishing campaigns, but also account takeovers, ransomware intrusions, and business email compromise (BEC) attacks.
The report adds that ownership of the leaked data remains unclear. Some of it may belong to security researchers compiling data for monitoring, while some might be owned by threat actors and cybercriminals.
For users, the most suitable action in such situations is to ensure that they immediately change their password. Additionally, it is prudent to use 2FA authentication wherever possible to add an additional layer of security, or employ newer measures like passkeys in favor of traditional passwords.

Related
World Password Week 2025: AP's expert tips to stay safe online
The words we trust — and the risks we forget — in our online lives
.png)


