
Hackers are hijacking expired or deleted Discord invite links to redirect users to malicious sites that deliver remote access trojans and information-stealing malware.
The campaign relies on a flaw in the Discord invitation system to leverage multi-stage infections that evade multiple antivirus engines.
"Reviving" expired Discord invites
Discord invite links are URLs that allow someone to join a specific Discord server. They contain an invite code, which is a unique identifier that grants access to a server and can be temporary, permanent, or custom - vanity links available to 'level 3' servers paying for special perks.
As part of the perks for level 3 Discord servers, administrators can create a personalized invite code. For regular servers, Discord generates random invite links automatically and the chance of one repeating itself is very low.
However, hackers noticed that when a level 3 server loses its boost status, the custom invite code becomes available and can be reclaimed by another server.
Researchers at cybersecurity company Check Point say that this is also true in the case of expired temporary invites or deleted permanent invitation links.
They say that "the mechanism for creating custom invite links surprisingly lets you reuse expired temporary invite codes, and, in some cases, deleted permanent invite codes."
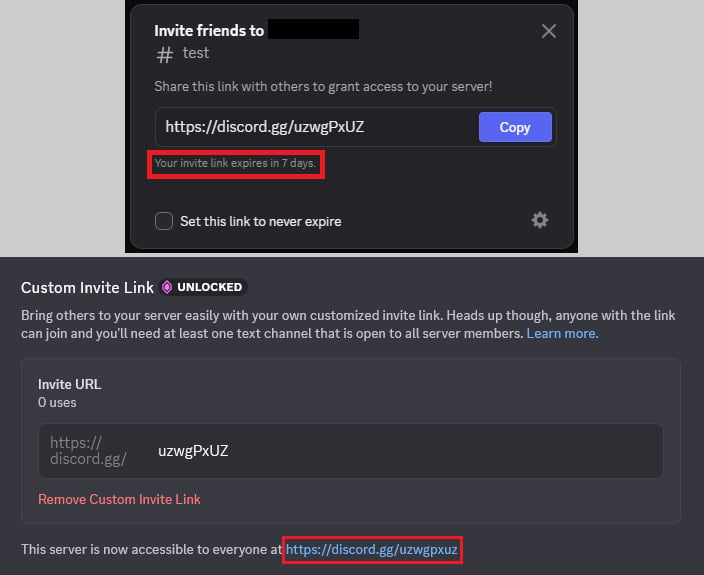 Hijacking a temporary invite code (top) and reusing it in a vanity link (bottom)
Hijacking a temporary invite code (top) and reusing it in a vanity link (bottom)Source: Check Point
Additionally, the researchers say that Discord's faulty mechanism does not modify the expiration time of an already generated temporary invitation code when reusing it as a permanent invitation link.
"Users often mistakenly believe that by simply checking this box, they have made the existing invite permanent (and it was this misunderstanding that was exploited in the attack we observed)" - Check Point
An invite code with lowercase letters and digits cannot be registered as long as it is active. However, if the code has uppercase letters, it can be reused in vanity links with lowercase, even if the original is still valid.
Check Point researchers explain that this is possible because Discord stores and compares vanity links in lowercase. As a result, the same code with lower and uppercase letters is valid for two separate servers at the same time.
Redirecting to malicious servers
Attackers are monitoring deleted or expired Discord invitations and use them in a campaign that has impacted 1,300 users in the US, UK, France, the Netherlands, and Germany, based on Check Point's download count of the malicious payloads.
The researchers say that cybercriminals are hijacking Discord invite links from legitimate communities, and share them on social media or official comunity websites. To add credibility to the deceit, hackers design the malicious servers to look authentic.
The malicious Discord servers only show a single channel to the visitor, #verify, and a bot prompts the user to go through a verification process.
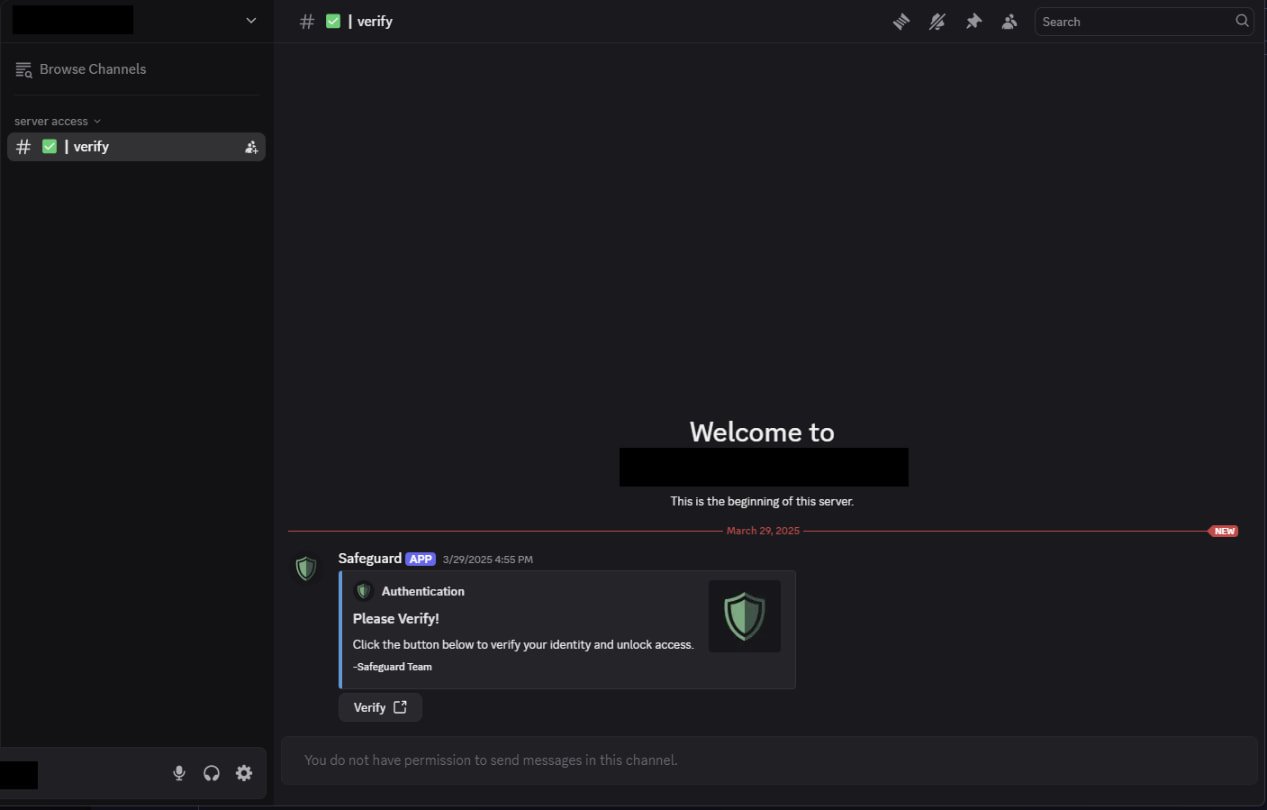 Attacker's Discord channel
Attacker's Discord channelSource: Check Point
Attempting to do so launches a typical 'ClickFix' attack where the user is redirected to a website that mimics the Discord UI and pretends that the CAPTCHA failed to load.
The users are tricked into manually opening the Windows Run dialog and pasting a PowerShell command, which they had already copied to the clipboard for execution.
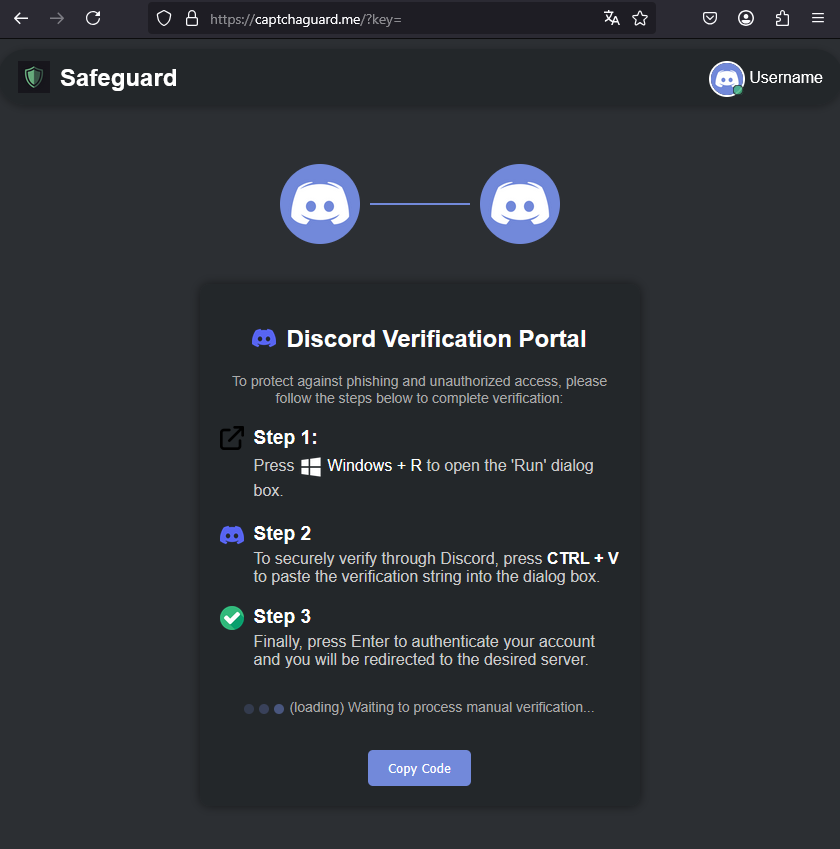 The ClickFix page
The ClickFix pageSource: Check Point
Doing so triggers a multi-stage infection involving PowerShell downloaders, obfuscated C++ loaders, and VBScript files.
The final payloads are downloaded from the legitimate Bitbucket software collaboration and file hosting service, and include:
- AsyncRAT: Delivered as 'AClient.exe,' this is version 0.5.8 of the malware that uses Pastebin to fetch its C2 address dynamically. Its capabilities include file operations, keylogging, and webcam/microphone access
- Skuld Stealer: Delivered as 'skul.exe,' this is an info-stealer that targets browser credentials, cookies, Discord tokens, and cryptocurrency wallet data (injects JS to steal mnemonic phrases and passwords using Discord webhooks)
- ChromeKatz: A custom version of the the open-source tool, delivered as 'cks.exe', that can steal cookies and passwords
A scheduled task is also added on the host to re-run the malware loader every five minutes, the researchers discovered.
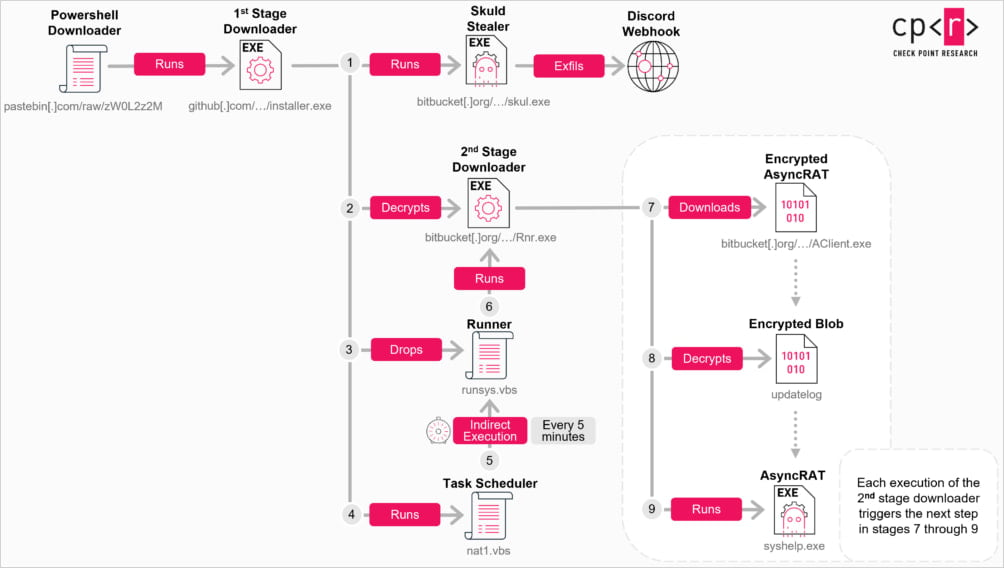 Infection chain from ClickFix to malware
Infection chain from ClickFix to malwareSource: Check Point
To defend against this threat, it is recommended that Discord users avoid trusting old invite links, especially those from months-old posts, treat "verification" requests with extra caution, and never run copied PowerShell commands that you don't fully understand.
Additionally, Discord server administrators are recommended to use permanent invites, which are more difficult to hijack.
Why IT teams are ditching manual patch management
Patching used to mean complex scripts, long hours, and endless fire drills. Not anymore.
In this new guide, Tines breaks down how modern IT orgs are leveling up with automation. Patch faster, reduce overhead, and focus on strategic work -- no complex scripts required.
.png)
 4 months ago
48
4 months ago
48





