
A remote access trojan dubbed SleepyDuck, and disguised as the well-known Solidity extension in the Open VSX open-source registry, uses an Ethereum smart contract to establish a communication channel with the attacker.
Open VSX is a community-driven registry for extensions compatible with VS Code, which are popular with AI-powered integrated development environments (IDEs) like Cursor and Windsurf.
The extension is still present on Open VSX as 'juan-bianco.solidity-vlang', albeit with a warning from the platform, and has been downloaded more than 53,000 times.
When initially submitted on October 31st, the extension was harmless and received malicious capabilities with an update the next day, when the download count had already reached 14,000.
According to a report from extension security platform Secure Annex, a notable feature in SleepyDuck is the use of Ethereum contracts to update its command-and-control (C2) server address and achieve long-term persistence.
Even if the default C2 server at sleepyduck[.]xyz is taken down, the contract on the Ethereum blockchain allows the malware to remain functional.
Since its submission to Open VSX with version 0.0.7 and until version 0.1.3 published on November 2nd, the juan-bianco.solidity-vlang package was downloaded 53,439 times and has only one 5-star rating from its author.
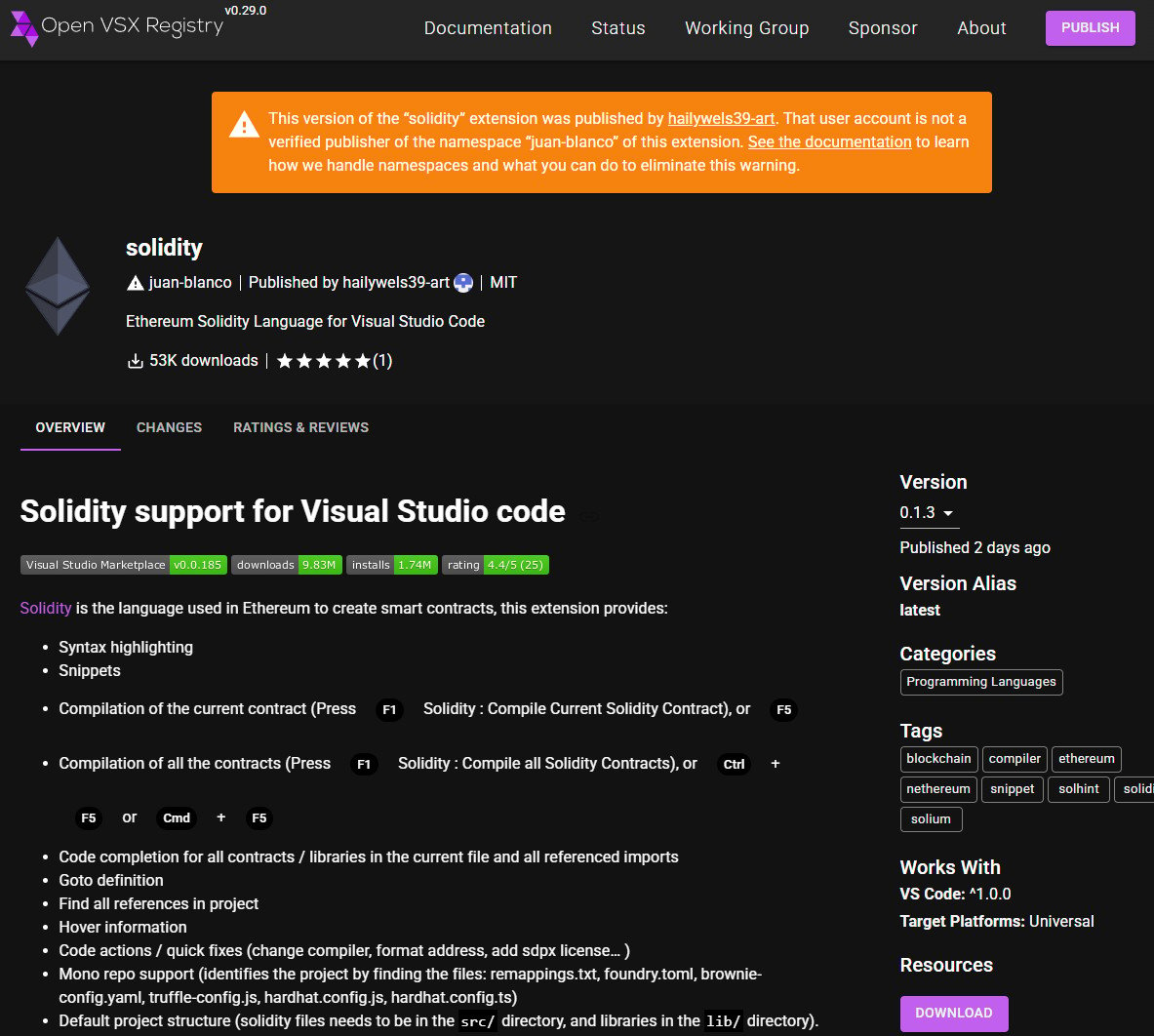 Malicious package on Open VSX
Malicious package on Open VSXSource: BleepingComputer
It should be noted that author of the malic
The malicious code activates on editor startup, when a Solidity file is opened, or when the user runs the Solidity compile command.
Upon activation, it creates a lock file to run once per host and calls a fake ‘webpack.init()’ function from ‘extension.js’ to make it appear legitimate, but in reality, it loads a malicious payload.
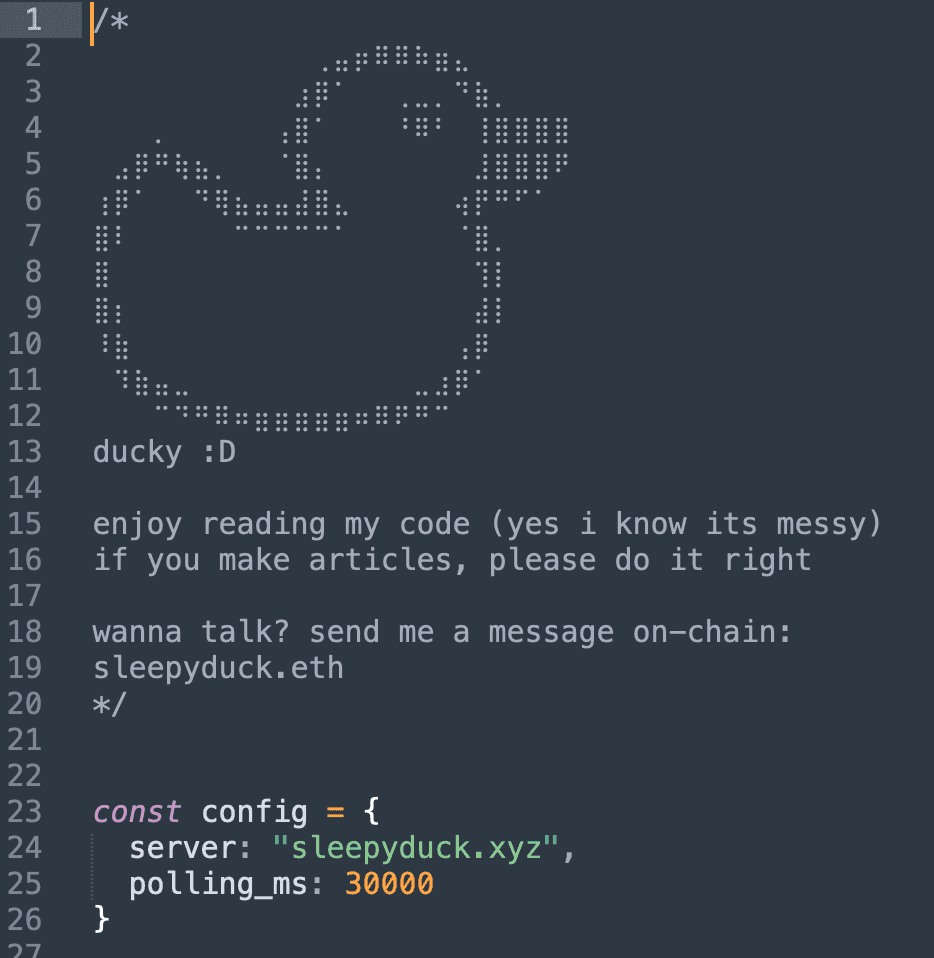 Fake webpack file
Fake webpack fileSource: Secure Annex
According to Secure Annex, the malicious component in SleepyDuck collects system data (hostname, username, MAC address, and timezone) and sets up a command execution sandbox.
The researchers say that when initialized, the malware finds the fastest Ethereum RPC provider to read the smart contract with the C2 information, starts a sleepyduck instance, updates with a current valid configuration, and begins a polling loop.
The Ethereum blockchain is used for C2 redundancy, so if the primary command server goes offline, the malware reads updated instructions directly from the blockchain, including a new C2 server address or modified communication intervals.
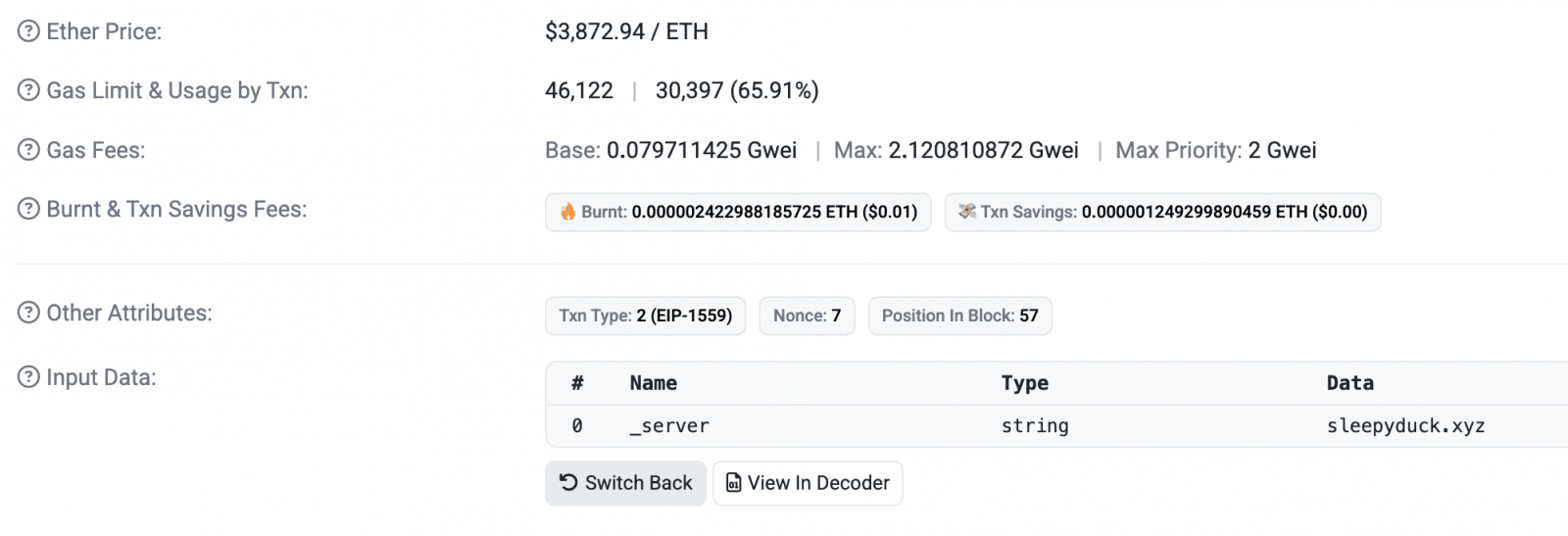 The smart contract used by SleepyDuck
The smart contract used by SleepyDuckSource: Secure Anex
The researchers also say that the polling function will send data about the system in a POST request and look "for a command to execute from the response."
Open VSX’s growing popularity has placed it on the hackers’ radar, receiving multiple malicious submissions targeting unsuspecting developers.
Recently, the platform announced a set of security enhancements to make it safer for its users, including shortening token lifetimes, quickly revoking leaked credentials, automated scans, and sharing key info with VS Code about emerging threats.
Software developers should exercise caution when downloading VS Code extensions, trusting only reputable publishers and their official repositories.
The 2026 CISO Budget Benchmark
It's budget season! Over 300 CISOs and security leaders have shared how they're planning, spending, and prioritizing for the year ahead. This report compiles their insights, allowing readers to benchmark strategies, identify emerging trends, and compare their priorities as they head into 2026.
Learn how top leaders are turning investment into measurable impact.
.png)
 12 hours ago
2
12 hours ago
2






