
The Bumblebee malware SEO poisoning campaign uncovered earlier this week aimpersonating RVTools is using more typosquatting domainsi mimicking other popular open-source projects to infect devices used by IT staff.
BleepingComputer was able to find two cases leveraging the notoriety of Zenmap, the GUI for the Nmap network scanning tool, and the WinMTR tracerout utility.
Both of these tools are commonly used by IT staff to diagnose or analyze network traffic, requiring administrative privileges for some of the features to work This makes users of these tools prime targets for threat actors looking to breach corporate networks and spread laterally to other devices.
The Bumblebee malware loader has been pushed through at least two domains - zenmap[.]pro and winmtr[.]org. While the latter is currently offline, the former is still online and shows a fake blog page about Zenmap when visited directly.
When users are redirected to zenmap[.]pro from from search results, though, it shows a clone of the legitimate website for the nmap (Network Mapper) utility:
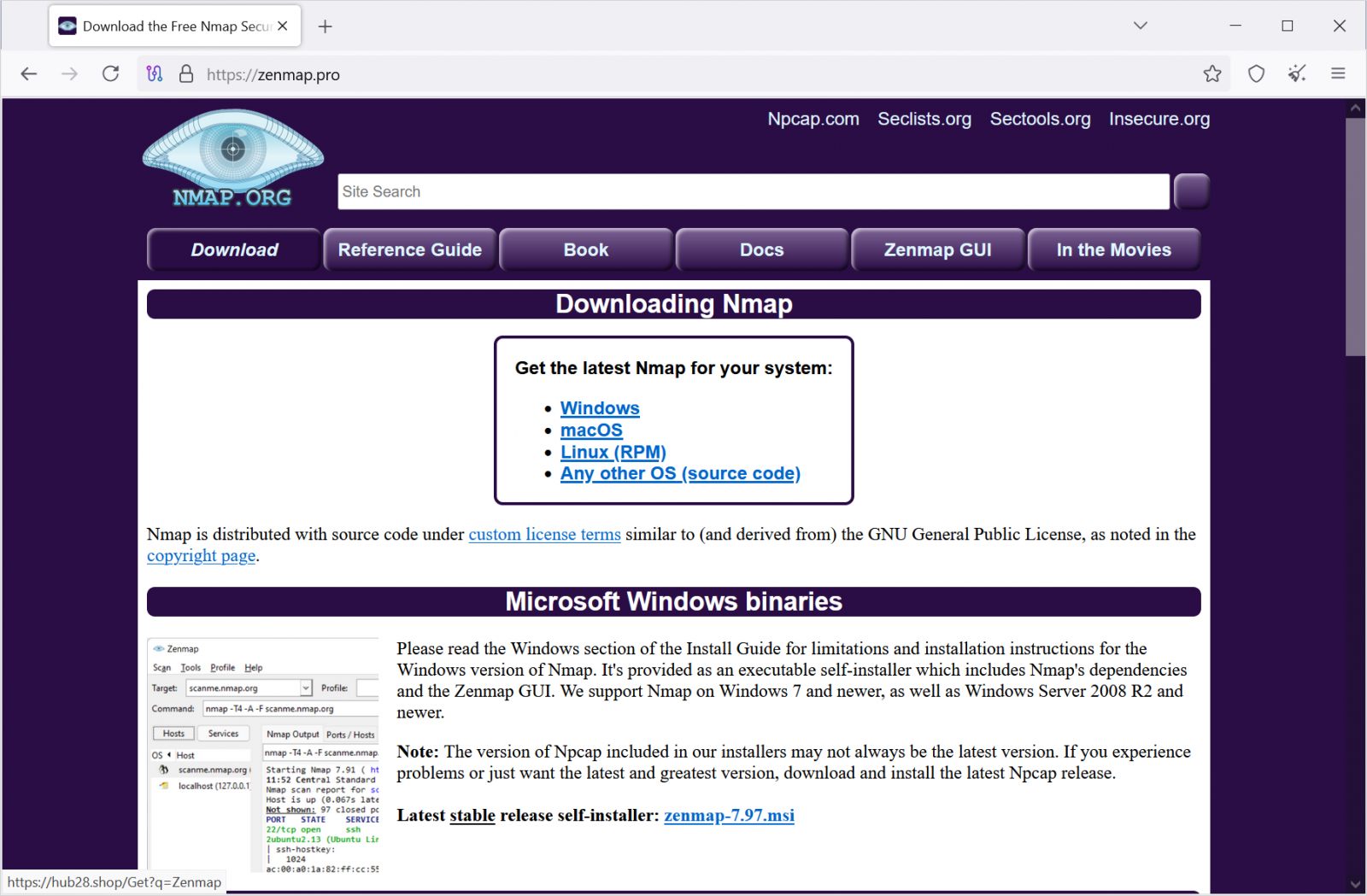 Fake nmap website delivering Bumblebee-infested installers
Fake nmap website delivering Bumblebee-infested installersSource: BleepingComputer
The two sites received traffic through SEO poisoning and rank high in Google and Bing search results for the associated terms.
.jpg) Google Search results
Google Search resultsSource: BleepingComputer
Bleepingcolputer's tests show that if you visit the fake Zenmap site directly, it shows several AI-generated articles instead, as seen in the image below:
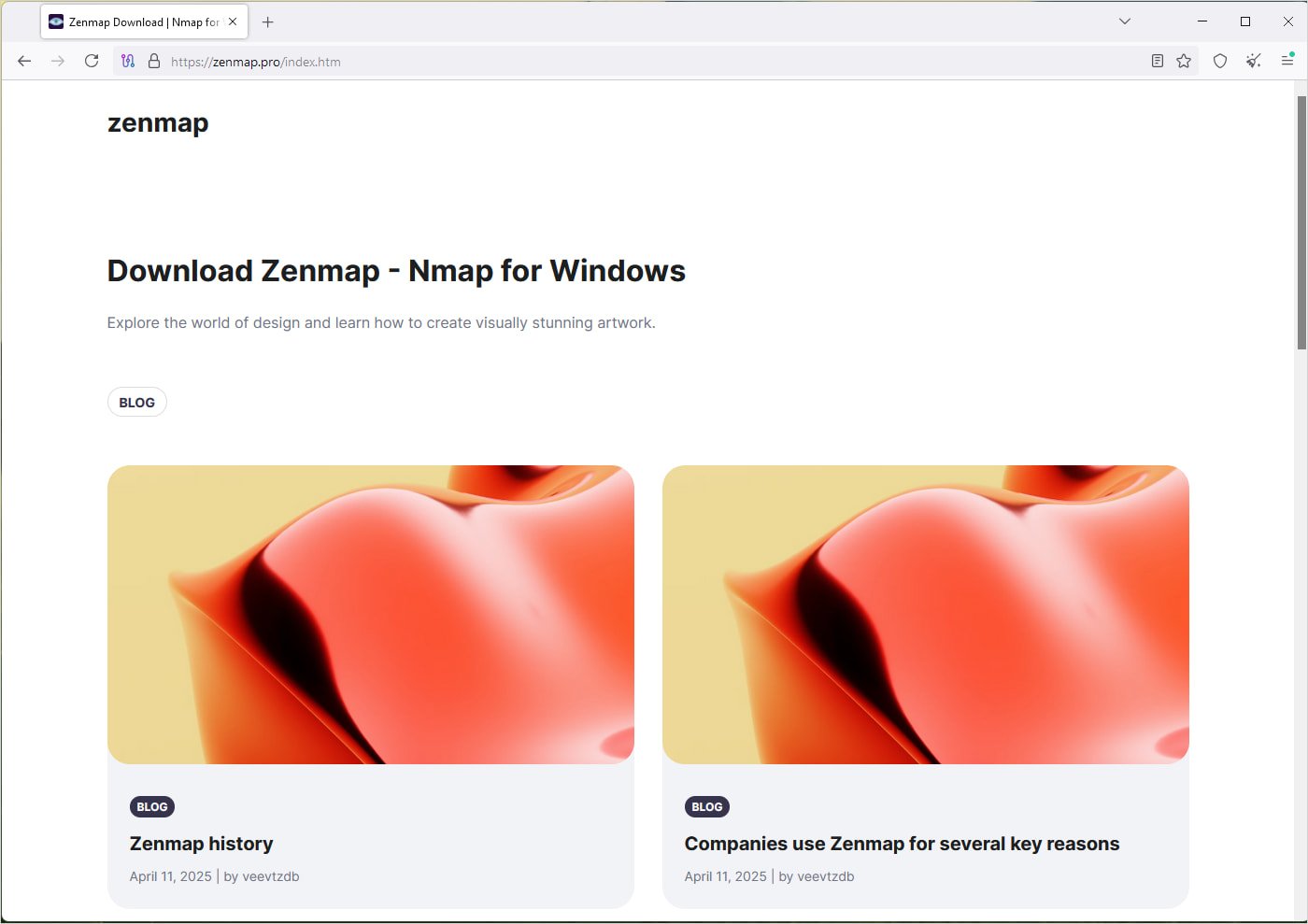 Innocuous blog loading on direct hits
Innocuous blog loading on direct hitsSource: BleepingComputer
The payloads delivered through the download section ‘zenmap-7.97.msi’ and ‘WinMTR.msi, and they both evade detection from most antivirus engines on VirusTotal [1, 2].
The installers deliver the promised application along with a malicious DLL, as in the case of RVTools, which drops a Bumblebee loader on users' devices.
From there, the backdoor can be used to profile the victim and introduce additional payloads, which may include infostealers, ransomware, and other types of malware.
Apart from the open-source tools mentioned above, BleepingComputer has also seen the same campaign targeting users looking for Hanwha security camera management software WisenetViewer.
Cyjax’s researcher Joe Wrieden also spotted a trojanized version of the video management software Milestone XProtect being part of the same campaign, the malicious installers being delivered ‘milestonesys[.]org’ (online).
Official RVTools still offline
Both official RVTools domains - Robware.net and RVTools.com - are currently showing a warning for users not to download the software from unofficial sites but don't make available the download link themselves.
Following allegations that the official RVTools site pushed a malware-laced installer, Dell Technologies denied the accusation saying that its sites did not distribute a trojanized variant of the product.
Dell stated that the official RVTools sites were taken offline because they were being the targets of distributed denial-of-service (DDoS) attacks.
One explanation for the attacks would be that the threat actor behind Bumblebee decided to take down the official download portals to drive to the malicious sites users searching for alternative sources for the tool.
To mitigate the risk of installing trojanized versions of legitimate software, the best recommendation is to make sure to get it from official sources and package managers.
It is also worth checking the downloaded installer's hash with a known, clean version before running it.
.png)
 4 months ago
58
4 months ago
58





