Detect malware, unsafe data flows, and license issues in GitHub Actions with Socket’s new workflow scanning support.

If you’ve spent any time maintaining CI/CD pipelines, you already know what a mess GitHub Actions security has become. Workflows pull in unpinned dependencies from hundreds of repositories, often running with full access to secrets, tokens, and build artifacts. Tags like v1 get reused and repointed, and no one notices until something breaks—or worse, until a malicious update slips through.
We’ve seen the consequences play out publicly: compromised actions injecting malicious code, leaked secrets from misconfigured workflows, and attackers taking advantage of mutable tags and insecure defaults. For all the attention given to securing dependencies, CI/CD has remained the weakest link in most software supply chains.
Today, we’re doing something about it. Socket now supports scanning GitHub Actions for malware and unsafe behavior. This experimental release brings Socket’s deep package inspection and taint-tracking capabilities to the CI/CD layer, giving teams visibility into risks hidden inside GitHub workflows for the first time.
Scanning Workflows for Malicious and Unsafe Behavior#
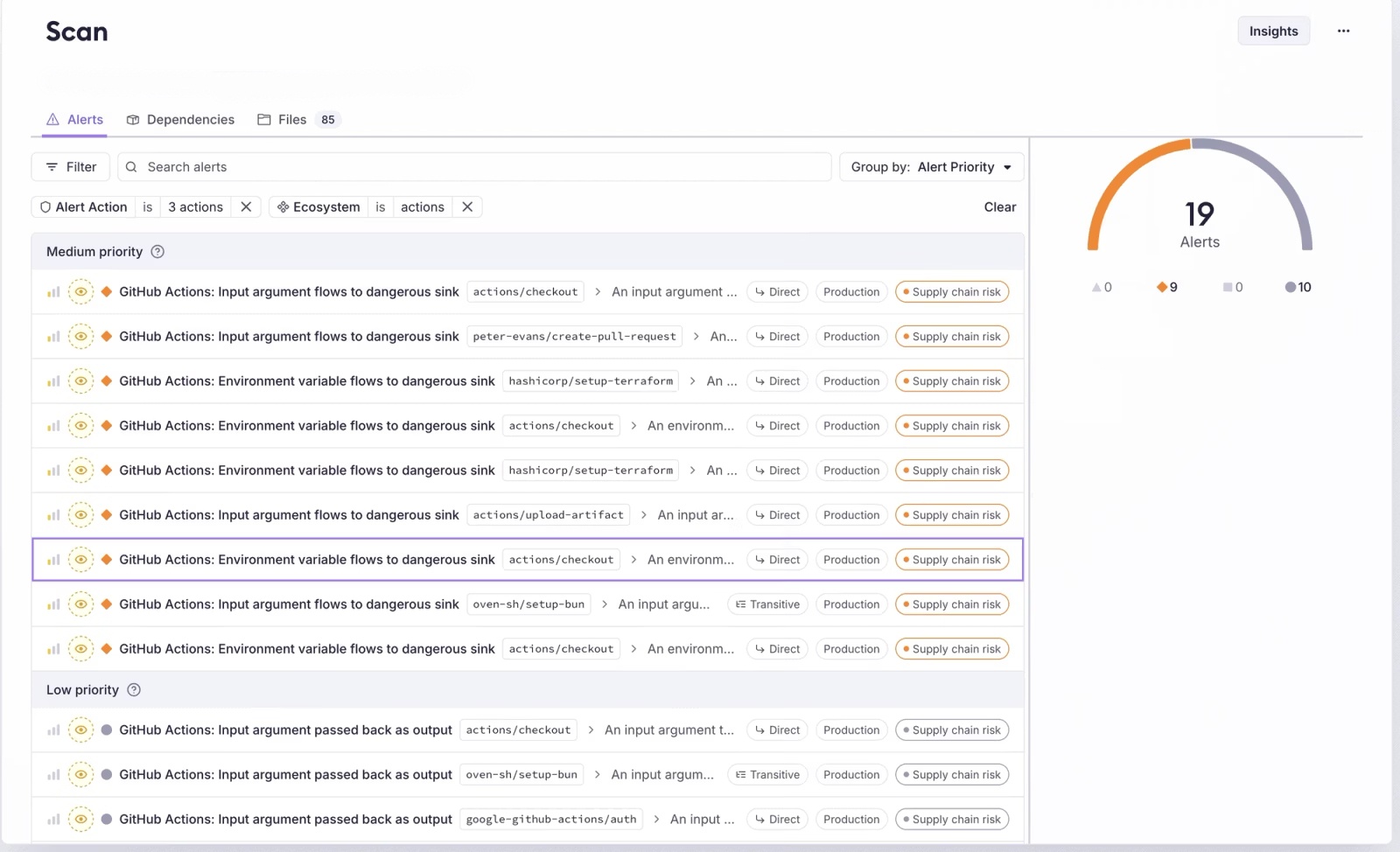
Socket automatically parses action dependencies from workflow files and any transitive dependencies declared in composite actions’ action.yml files. The scanner analyzes both direct and indirect actions referenced in your pipelines, producing the same detailed alerts you already see for npm packages, now applied to your workflows.
Because many GitHub Actions are bundled JavaScript projects, Socket performs a full static analysis of the JavaScript embedded in each action. This enables detection of issues such as:
- Malicious or obfuscated code
- Dangerous command execution patterns
- Potential data exfiltration behavior
Socket’s GitHub Actions scanning currently supports 27 alert types covering supply chain, security, license, and maintenance risks. This includes full coverage for license compliance alerts such as unlicensed or non-permissive code, license policy violations, and ambiguous classifiers.
It also detects supply chain threats like known malware, protestware, telemetry, and obfuscated or network-active code. Socket identifies unsafe code patterns within Actions, including use of eval, shell access, environment or filesystem manipulation, and potential data exfiltration paths. AI-powered analysis extends coverage further with automated detection of malicious, anomalous, or typosquatted code.
Support for CVE and typosquat detection will arrive in the upcoming beta release, bringing GitHub Actions scanning to full parity with Socket’s existing JavaScript and Python ecosystems.
Custom GitHub Actions Alerts#
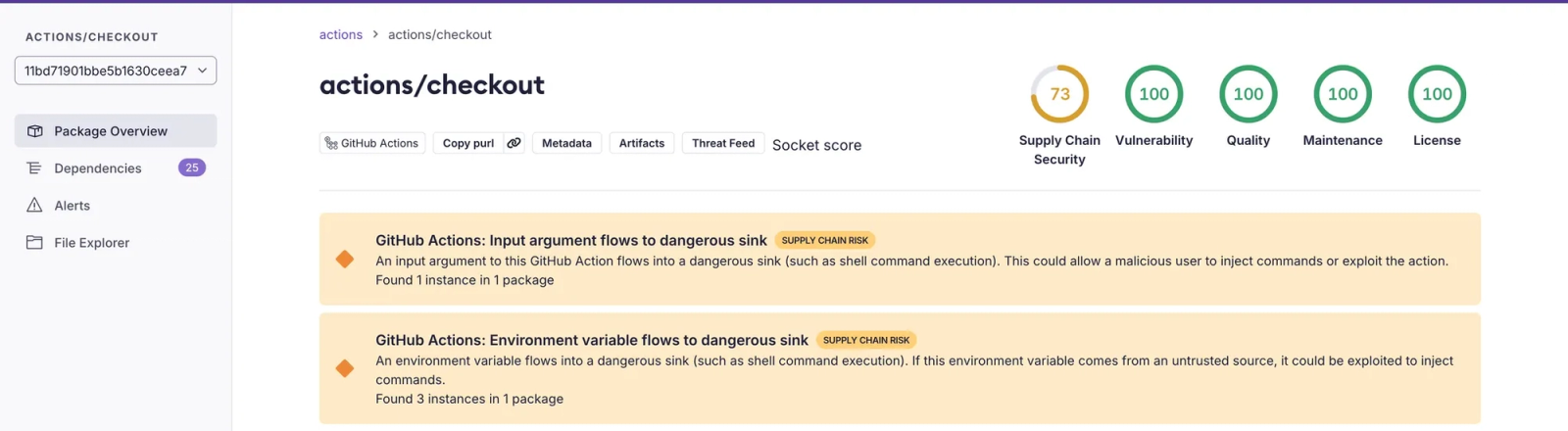
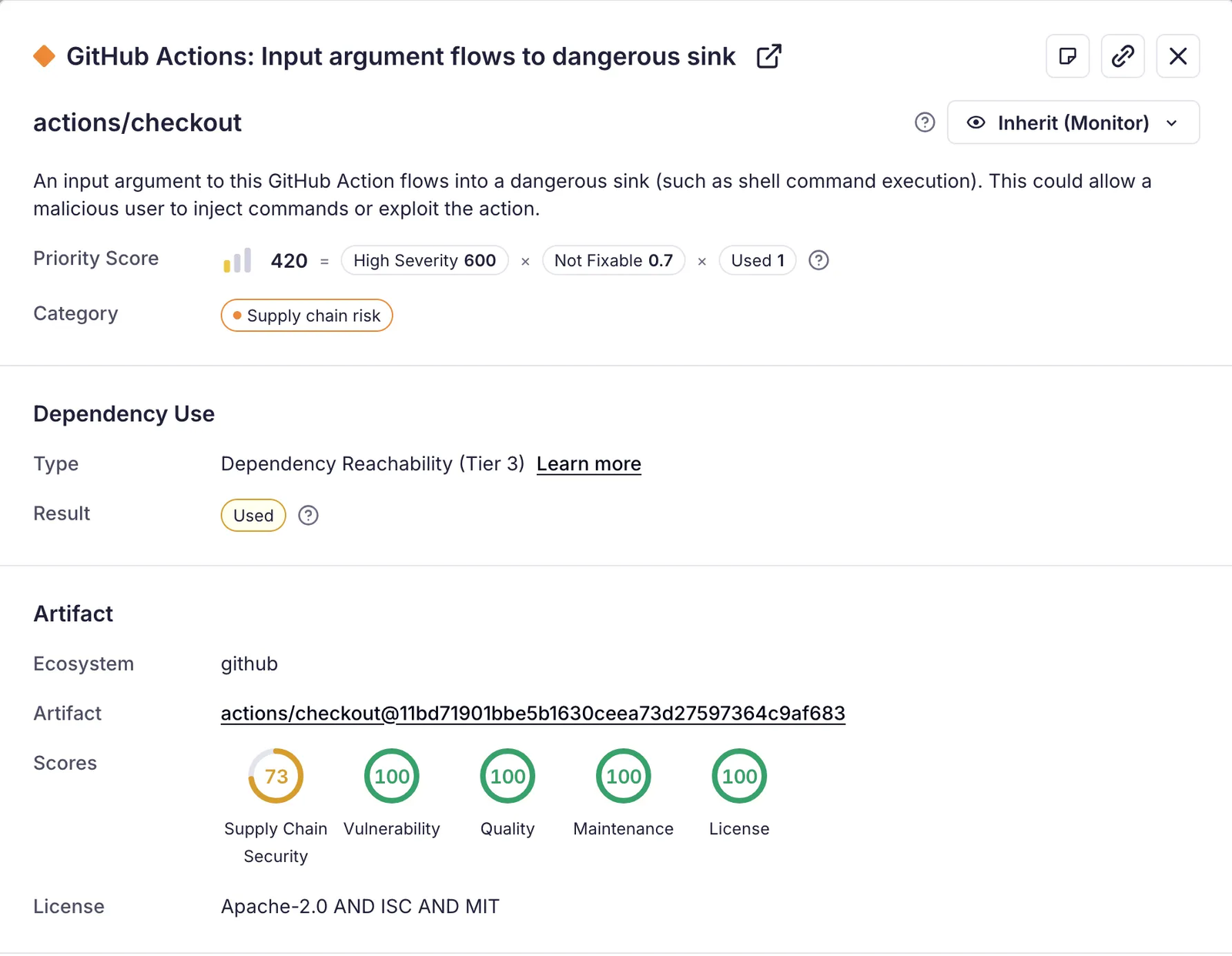
Beyond standard scanning, Socket now surfaces a new class of custom GitHub Actions alerts powered by Argus, an open-source taint-tracking engine, developed by North Carolina State University and Purdue University for detecting unsafe data flows. Socket uses Argus to analyze how data moves through Actions, identifying cases where untrusted inputs, workflow context, or parameters reach sensitive sinks such as environment variables, shell commands, or outputs.
Actions execute in privileged environments with access to secrets, build artifacts, and configuration data. Unsafe data flows can lead to command injection or secret leakage, especially when community-contributed actions handle inputs without proper sanitization.
Custom GitHub Actions alerts include:
- Context to Sink — Detects when workflow context values flow into potentially dangerous command or function calls.
- Arg to Sink — Flags user-supplied action inputs that reach command execution or other sensitive sinks.
- Context to Env — Warns when workflow context data is written to environment variables that may expose secrets.
- Context to Output — Identifies context values that are written to outputs, which could leak data between jobs.
- Arg to Env — Catches action inputs being exported to environment variables without sanitization.
- Arg to Output — Detects user inputs written to outputs, potentially exposing untrusted or sensitive values.
A widespread but risky practice in the GitHub Actions ecosystem is versioning releases using mutable tags like v1. When those tags are later repointed to new commits, any workflows using them automatically change behavior, even if the repository owner never updates their workflow.
Attackers have abused this behavior by mutating existing tags to deliver malicious code, such as the incident involving tj-actions/changed-files.
Socket protects against this by always scanning the specific commit a tag resolves to at scan time. If the tag is later updated to a malicious version, Socket detects the change and flags it on the next scan.
Bringing Supply Chain Security to CI/CD#
GitHub Actions are an essential part of modern development workflows and one of the least protected. By extending Socket’s deep inspection to workflows themselves, we’re closing one of the last major gaps in the software supply chain.
As of today, all Socket users can search for and explore GitHub Actions on Socket’s package pages. GitHub Actions scanning is currently available in experimental release for Business and Enterprise customers. To enable scanning in your organization, get in touch with us to have the feature activated.
This is just the first step. Over the coming months, we’ll expand coverage to include CVE and typosquat detection and continue refining our taint-tracking analysis to make GitHub Actions safer for everyone.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it nowReady to block malicious and vulnerable dependencies?


Product
Unify Your Security Stack with Socket Basics
A single platform for static analysis, secrets detection, container scanning, and CVE checks—built on trusted open source tools, ready to run out of the box.
By Douglas Coburn, Eli Insua - Oct 21, 2025

.png)




