The Gootloader malware loader operation has returned after a 7-month absence and is once again performing SEO poisoning to promote fake websites that distribute the malware.
Gootloader is a JavaScript-based malware loader spread through compromised or attacker-controlled websites, used to trick users into downloading malicious documents.
The websites are promoted in search engines either via ads or through search engine optimization (SEO) poisoning, which ranks a website higher in the results for a particular keyword, like legal documents and agreements.
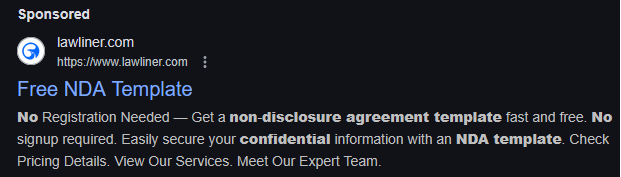 Malicious ad for an NDA template
Malicious ad for an NDA templateSource: Gootloader researcher
In the past, these websites would display fake message boards that pretended to discuss users' query, with some posts recommending (malicious) document templates that could be downloaded. The SEO campaigns later switched to using websites that pretend to offer free templates for various legal documents.
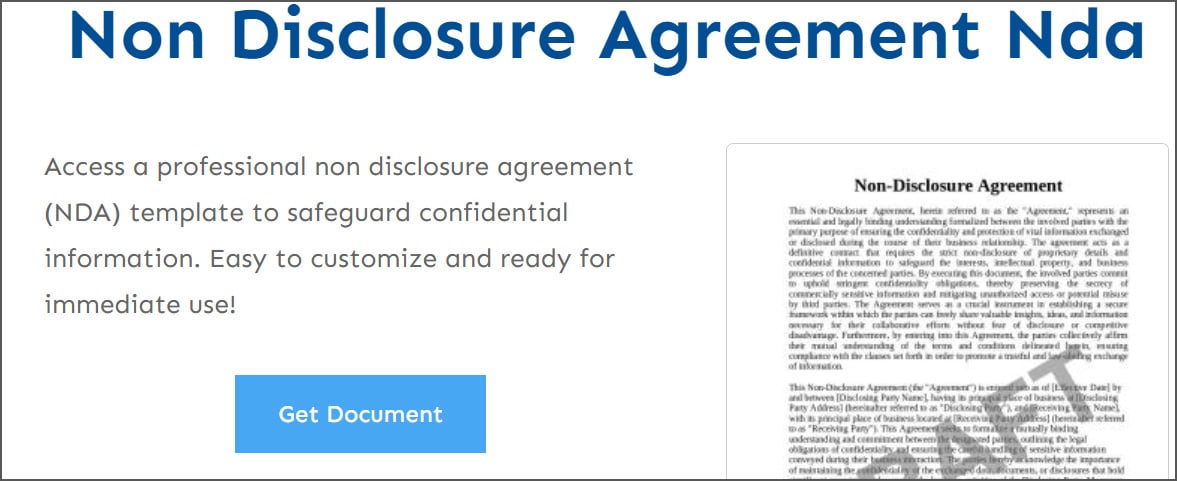 Fake agreement and legal document template site
Fake agreement and legal document template siteSource: Gootloader researcher
When a visitor clicked the "Get Document" button, the site checked if they were a legitimate user and, if so, downloaded an archive containing a malicious document with a .js extension. For example, the archive could include a file named mutual_non_disclosure_agreement.js.
Gootloader would execute when launching the document and downloaded additional malware payloads onto the device, including Cobalt Strike, backdoors, and bots that provided initial access to corporate networks. Other threat actors then used this access to deploy ransomware or conduct other attacks.
Gootloader returns
A cybersecurity researcher operating under the pseudonym "Gootloader" has been tracking and actively disrupting the malware operation for years by filing abuse reports with ISPs and hosting platforms to take down attacker-controlled infrastructure.
The researcher told BleepingComputer that his activities led to the Gootloader operation suddenly ceasing on March 31st, 2025.
The researcher and Anna Pham of Huntress Labs now report that Gootloader has returned in a new campaign that once again impersonates legal documents.
"In this latest campaign, we've observed thousands of unique keywords spread over 100 websites," reads a new blog post by the Gootloader researcher. "The ultimate goal remains the same: convince victims to download a malicious ZIP archive containing a JScript (.JS) file that establishes initial access for follow-on activity — usually leading to ransomware deployment."
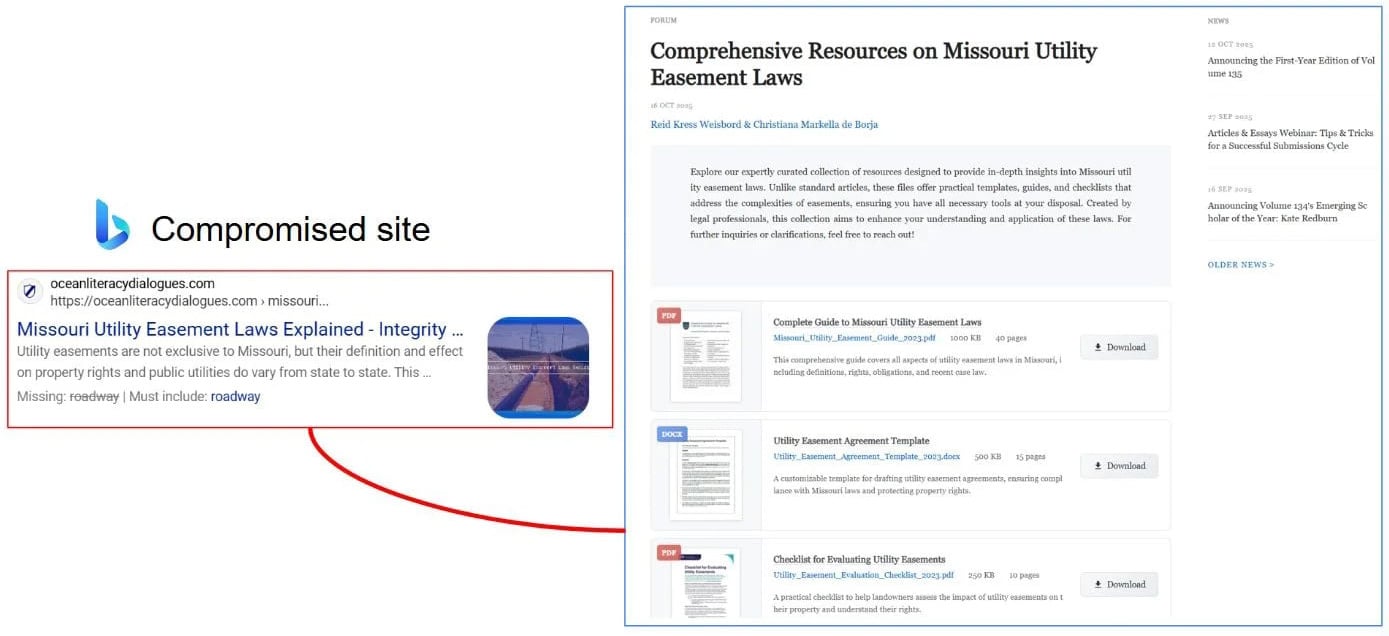 Current attack flow of Gootloader campaign
Current attack flow of Gootloader campaignSource: Huntress Labs
However, the researchers say this new variant uses a few techniques to evade automated analysis tools and security researchers.
Huntress found that the JavaScript added to malicious websites hides the real filenames by using a special web font that replaces letters with look-alike symbols.
In the HTML source, you see nonsense text, but when the page is rendered, the font's swapped glyph shapes display normal words, making it harder for security software and researchers to find keywords like "invoice" or "contract" in the source code.
"Rather than using OpenType substitution features or character mapping tables, the loader swaps what each glyph actually displays. The font's metadata appears completely legitimate—the character "O" maps to a glyph named "O", the character "a" maps to a glyph named "a", and so forth," explains Huntress.
"However, the actual vector paths that define these glyphs have been swapped. When the browser requests the shape for glyph "O", the font provides the vector coordinates that draw the letter "F" instead. Similarly, "a" draws "l", "9" draws "o", and special Unicode characters like "±" draw "i". The gibberish string Oa9Z±h• in the source code renders as "Florida" on screen."
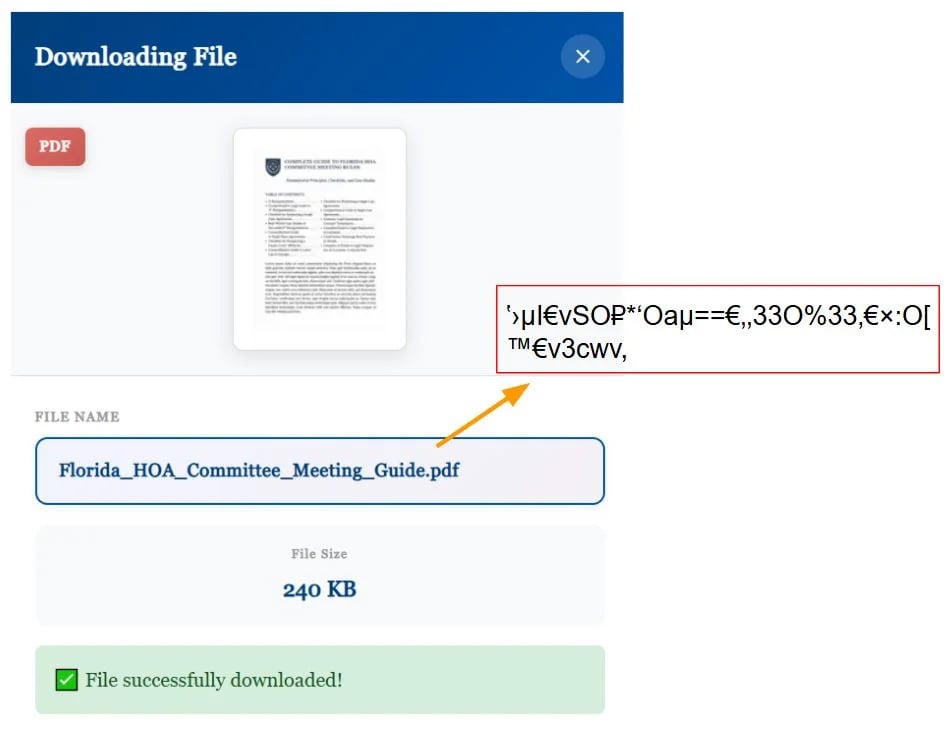 Using a character mapping table to display readable text to visitors
Using a character mapping table to display readable text to visitorsSource: Huntress Labs
Researchers from the DFIR Report also discovered that Gootloader is using malformed Zip archives to distribute Gootloader scripts from attacker-controlled websites.
These archives are crafted so that when the downloaded ZIP file is extracted with Windows Explorer, the malicious JavaScript file, Review_Hearings_Manual_2025.js, is extracted.
However, that same archive, when extracted within VirusTotal, Python's zip utilities, or 7-Zip, will unpack a harmless text file named Review_Hearings_Manual_202.txt.
As you can see in the image below of 010 Editor, the archive contains both files but is malformed, causing it to be extracted differently depending on the tool used.
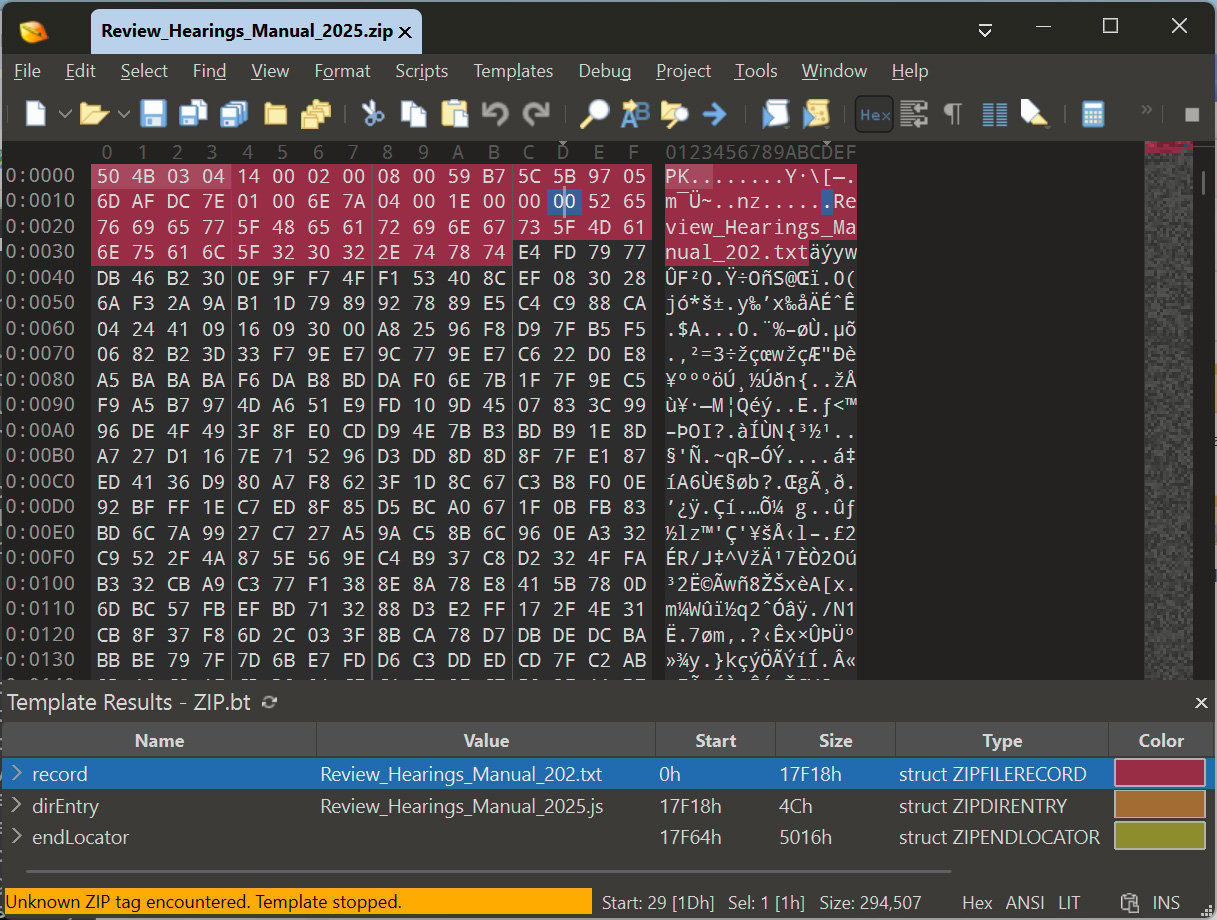 Gootloader archive using a malformed archive
Gootloader archive using a malformed archiveSource: BleepingComputer
It's unclear whether this is the same concatenation trick described in 2024 or if they are using a new technique to get Windows to extract the JS file.
Finally, the campaign is dropping the Supper SOCKS5 backdoor on devices, which is used to gain remote access to the network.
The Supper backdoor is malware that provides remote access to infected devices and is known to be used by a ransomware affiliate tracked as Vanilla Tempest.
This threat actor has a long history of conducting ransomware attacks and is believed to have been an affiliate of Inc, BlackCat, Quantum Locker, Zeppelin, and Rhysida.
In the attacks observed by Huntress, the threat actor moved fast once a device was infected, performing reconnaissance within 20 minutes and ultimately compromising the Domain Controller within 17 hours.
With Gootloader now back in operation, consumers and corporate users need to be careful about searching for and downloading legal agreements and templates from the web.
Unless the website is known for offering these types of templates, it should be treated with suspicion and avoided.
Secrets Security Cheat Sheet: From Sprawl to Control
Whether you're cleaning up old keys or setting guardrails for AI-generated code, this guide helps your team build securely from the start.
Get the cheat sheet and take the guesswork out of secrets management.
.png)
 11 hours ago
3
11 hours ago
3






