
Two critical vulnerabilities affecting the open-source forum software vBulletin have been discovered, with one confirmed to be actively exploited in the wild.
The flaws, tracked under CVE-2025-48827 and CVE-2025-48828, and rated critical (CVSS v3 score: 10.0 and 9.0 respectively), are an API method invocation and a remote code execution (RCE) via template engine abuse flaws.
They impact vBulletin versions 5.0.0 through 5.7.5 and 6.0.0 through 6.0.3 when the platform runs on PHP 8.1 or later.
The vulnerabilities were likely patched quietly last year with the release of Patch Level 1 for all versions of the 6.* release branch, and version 5.7.5 Patch Level 3, but many sites remained exposed due to not upgrading.
Public PoC and active exploitation
The two issues were discovered on May 23, 2025, by security researcher Egidio Romano (EgiX), who explained how to exploit it via a detailed technical post on his blog.
The researcher showed that the flaw lies in vBulletin's misuse of PHP's Reflection API, which, due to behavioral changes introduced in PHP 8.1, allows protected methods to be invoked without explicit accessibility adjustments.
The vulnerability chain lies in the ability to invoke protected methods via crafted URLs and the misuse of template conditionals inside vBulletin's template engine.
By injecting crafted template code using the vulnerable 'replaceAdTemplate' method, attackers bypass "unsafe function" filters using tricks like PHP variable function calls.
This results in fully remote, unauthenticated code execution on the underlying server — effectively granting attackers shell access as the web server user (www-data on Linux, for example).
On May 26, security researcher Ryan Dewhurst reported seeing exploitation attempts on honeypot logs showing requests to the vulnerable 'ajax/api/ad/replaceAdTemplate' endpoint.
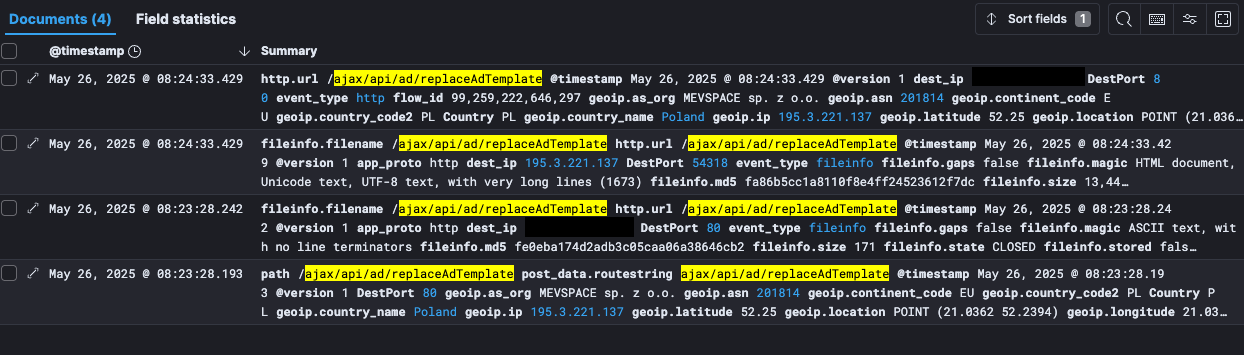 Logs showing exploitation attempts
Logs showing exploitation attemptsSource: blog.kevintel.com
Dewhurst traced one of the attackers to Poland, seeing attempts to deploy PHP backdoors to execute system commands.
The researcher noted that the attacks appear to be leveraging the exploit published earlier by Romano, though there have been Nuclei templates available for the flaw since May 24, 2025.
It is important to clarify that Dewhurst only observed exploitation attempts for CVE-2025-48827, but no evidence exists yet that attackers have successfully chained it to the full RCE, although this is highly likely.
vBulletin troubles
vBulletin is one of the most widely used commercial PHP/MySQL-based forum platforms, powering thousands of online communities globally.
Its modular design, including mobile APIs and AJAX interfaces, makes it a complex and flexible platform. However, it also exposes a broad attack surface.
In the past, hackers have leveraged severe flaws in the platform to breach popular forums and steal the sensitive data of large numbers of users.
Forum administrators are recommended to apply the security updates for their vBulletin installation or move to the latest release, version 6.1.1, which is not affected by the said flaws.
.png)
 4 months ago
78
4 months ago
78





