
A threat actor tracked as 'Hazy Hawk' is hijacking forgotten DNS CNAME records pointing to abandoned cloud services, taking over trusted subdomains of governments, universities, and Fortune 500 companies to distribute scams, fake apps, and malicious ads.
According to Infoblox researchers, Hazy Hawk first scans for domains with CNAME records pointing to abandoned cloud endpoints, which they determine via passive DNS data validation.
Next, they register a new cloud resource with the same name as the one in the abandoned CNAME, causing the original domain's subdomain to resolve to the threat actor's new cloud-hosted site.
Using this technique, the threat actors hijacked multiple domains to cloak malicious activities, host scam content, or use them as redirection hubs for scam operations.
Some notable examples of the hijacked domains include:
- cdc.gov – U.S. Centers for Disease Control and Prevention
- honeywell.com – Multinational conglomerate
- berkeley.edu – University of California, Berkeley
- michelin.co.uk – Michelin Tires UK
- ey.com, pwc.com, deloitte.com – Global "Big Four" consulting firms
- ted.com – Famous nonprofit media organization (TED Talks)
- health.gov.au – Australian Department of Health
- unicef.org – United Nations Children's Fund
- nyu.edu – New York University
- unilever.com – Global Consumer Goods Company
- ca.gov – California State Government
The complete list of compromised domains can be found in the Infoblox report.
Once the threat actor gains control of a subdomain, they generate hundreds of malicious URLs under it, which appear legitimate in search engines due to the parent domain's high trust score.
Victims clicking on the URLs are redirected through layers of domains and TDS infrastructure that profile them based on their device type, IP address, VPN use, etc., to qualify victims.
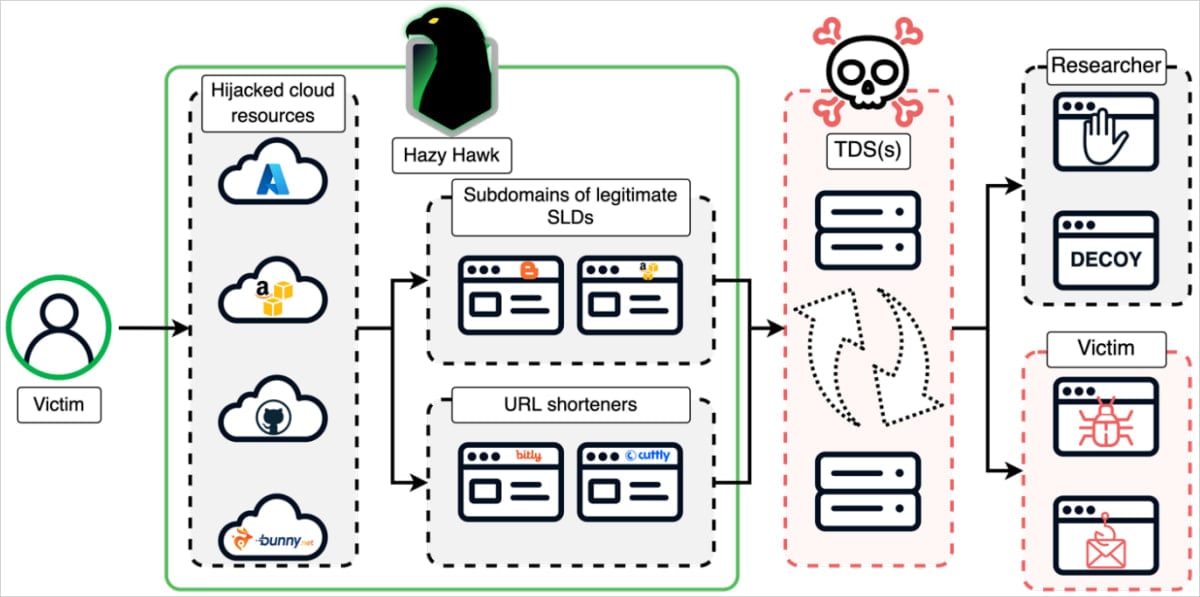 Overview of the Hazy Hawk attack
Overview of the Hazy Hawk attackSource: Infoblox
Infoblox's report says the sites are used for tech support scams, bogus antivirus alerts, fake streaming/porn sites, and phishing pages.
Users tricked into allowing browser push notifications get persistent alerts even after they leave the scam sites, which can generate significant revenue for Hazy Hawk.
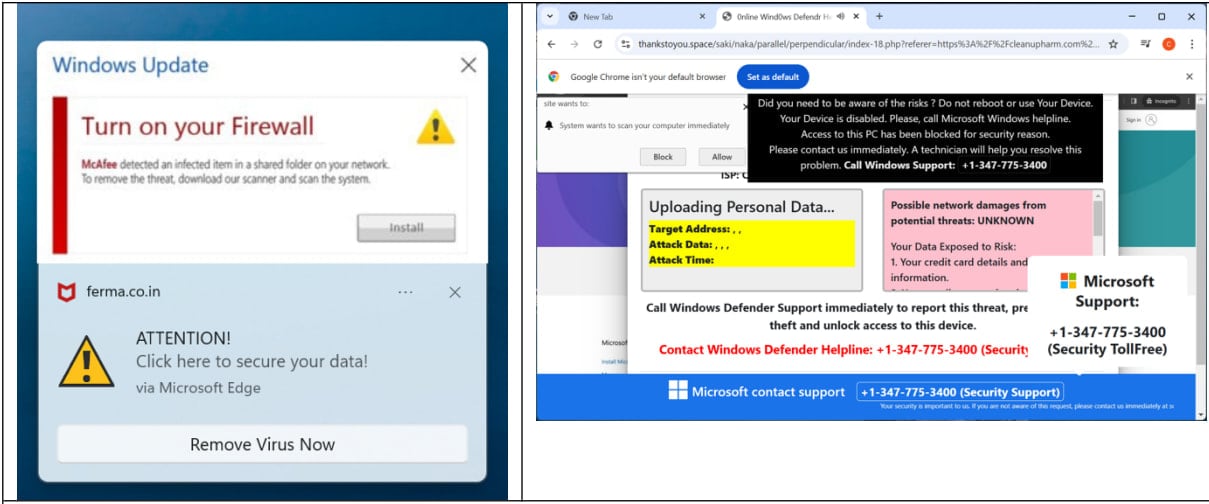 Push notification examples from the campaign
Push notification examples from the campaignSource: Infoblox
The same researchers reported previously about another threat actor, 'Savvy Seahorse,' who also abused CNAME records to build an atypical TDS that redirected users to fake investment platforms.
It's easy to overlook CNAME records, so they are prone to stealthy abuse, and it appears that an increasing number of threat actors realize this and attempt to take advantage.
In the case of Hazy Hawk, the operation's success also relies on organizations failing to delete DNS records after cloud services are decommissioned, which permits attackers to replicate the original resource name without authentication.
.png)
 3 days ago
29
3 days ago
29





