Source: Alina Vytiuk via Alamy Stock Photo
The most widespread, customized, sophisticated FileFix campaign to date has recently emerged in the wild.
Fewer than three months have passed since a red team researcher conceived of the FileFix social engineering technique, and attackers seem to be taking to it like ducks to water. Over the past couple of weeks, for instance, researchers from Acronis have observed the most mature FileFix campaign to date, combining convincing phishing, tough code obfuscation, robust steganography, and more.
Judging by VirusTotal uploads, the campaign has reached most corners of the planet: from the US to the Philippines, Bangladesh, Tunisia, the Dominican Republic, Germany, China, Peru, Nepal, and Serbia. The phishing site at its heart has been translated into at least 16 different languages, indicating targeting in Russia, India, Japan, Poland, Spain, France, Malaysia, Pakistan, and probably many more countries too.
A Quick Primer on FileFix
In mid-2022, a security researcher going by the pseudonym "mr. d0x" published an idea for a new type of social engineering attack. Dubbed "ClickFix," it involved tricking a victim into copying and pasting malicious commands into the Windows Run dialog, under the guise of fixing a fake technical issue, like a broken CAPTCHA test. It was relatively unsung until late in 2024, when attackers started to realize its potential. Then in March 2025, it exploded in popularity.
Related:Cyberattack on Kazakhstan's Largest Oil Company Was 'Simulation'
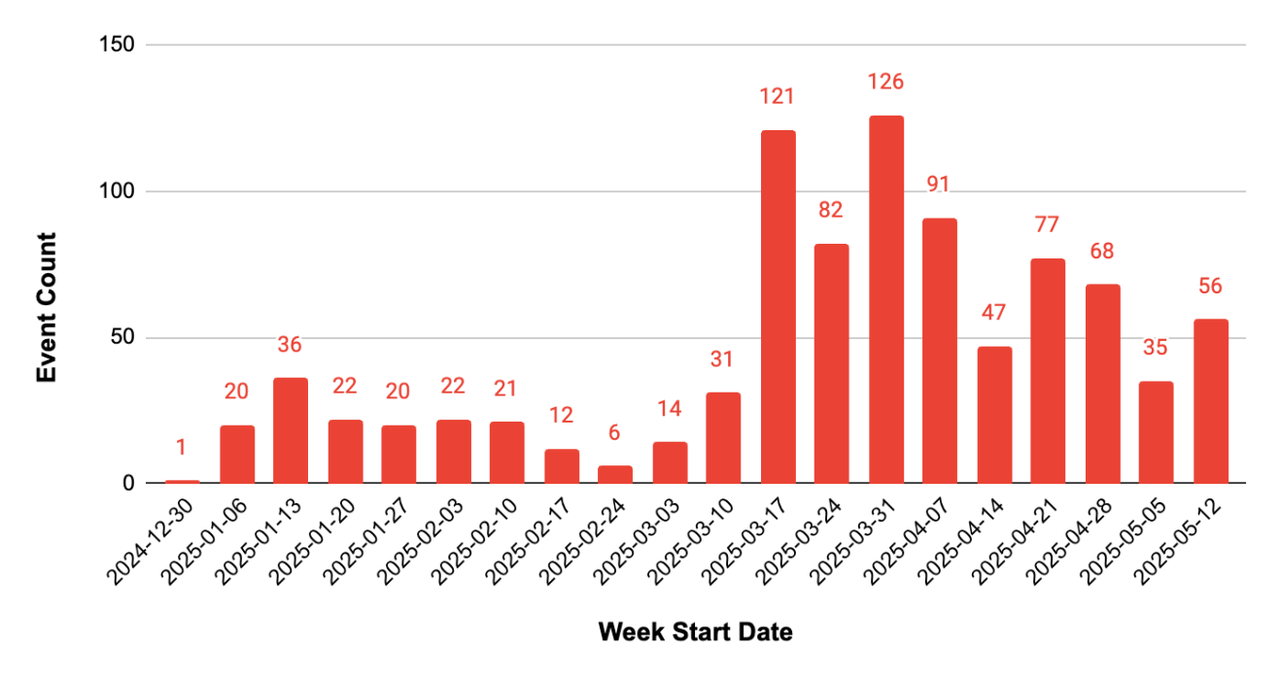
Source: Palo Alto Networks
In turn, mr. d0x created a follow-up to ClickFix. They named it "FileFix," and published a proof of concept (PoC) in June. The difference here was that instead of the Run dialog — a rather foreign program for most users — the new technique leaned on the more familiar File Explorer.
It was as simple as ClickFix. An attacker creates a phishing site that asks users to upload a file. When the user clicks to upload, the site copies Powershell code to their clipboard and launches an Explorer window. The user is instructed to copy a supposed file path — the code — to Explorer's address bar, and when they hit Enter it executes.
With ClickFix having proved its merit, attackers were seemingly more interested in mr. d0x's work this time around. They incorporated FileFix into some cheaply assembled malicious attacks mere days after its release. And now one group is using it as the foundation for a meaningful, globe-spanning phishing operation.
Case Study: a FileFix Attack Chain
In this case, the initial phishing lure is designed to impersonate Facebook security. It's likely delivered through phishing emails, warning users that their accounts are about to close, and that they need to take action by visiting a linked website. The site informs them that their account was reported, that it will be suspended in one week's time, and that it will be fully deactivated in 180 days if they don't take action. Lucky for the victim, they can appeal the ruling just by clicking a fat, blue button on the page.
Related:Iran MOIS Phishes 50+ Embassies, Ministries, Int'l Orgs
The ruse is well designed to play to victims' fears. After clicking "Appeal," they're informed that instructions for how to amend the Meta team's ruling are outlined in a PDF file, but that they have to paste the file's path into their Explorer window. After unwittingly executing malicious Powershell code, victims are presented with generic error messages on loop.
Meanwhile, the code downloads a JPG file depicting some kind of serene, natural image. Adding to the strangeness of the exercise, Acronis researchers believe that the images were generated using artificial intelligence (AI).

Source: Acronis
Through the power of steganography, the images carry with them a second Powershell script, designed to run yet another payload concealed inside of the same JPG. That final bit, StealC, is a popular commercial infostealer that scoops up passwords and other sensitive information from a variety of Web browsers, cryptocurrency wallets, cloud services, and other high-value apps like virtual private networks (VPNs), messaging platforms, and database applications.
Related:China Hijacks Captive Portals to Spy on Asian Diplomats
Will FileFix Eclipse ClickFix?
Conventional wisdom holds that phishing works best when it disguises itself most neatly into a victim's existing online patterns — impersonating brands they know and asking them to do things they're used to, like following links or opening attachments in work emails. It's a marvel, then, that FileFix or ClickFix work at all, let alone as well as they seem to.
"My guess is [it works because] it just comes out of left field," says Acronis senior security researcher Eliad Kimhy. "Not many people know you can execute commands from the address bar of an upload window. Most Windows users have probably never interacted with the terminal in any way. This creates a situation where the average user is likely caught off guard and not fully aware of the risk."
The novelty and brevity of these tricks also help. "This isn't covered by most phishing awareness campaigns yet. And it also takes just a couple of button presses, so by the time you've run the command, you might not have had enough time to question what you're doing," Kimhy says.
Between the two, FileFix comes off a bit more elegant than ClickFix, for using File Explorer instead of the dialog box. But it really separates itself in one particular respect. Many organizations with managed IT services block employees and users from accessing the Run dialog, for security reasons, so FileFix offers attackers a far broader range of higher-value targets to pick from.
"On paper, it does seem like FileFix offers an advantage, as it's a bit more familiar and less suspicious to put a file path into File Explorer than it is to open the terminal. But then again, attackers don't always go for what's better 'on paper,'" Kimhy points out.
He concludes that "a lot will depend on how security practitioners respond, and attackers will likely continue to use both. Regardless, my guess is that we're going to see more FileFix attacks in the near future."
.png)
 1 month ago
10
1 month ago
10




