
Earlier this month, a coordinated disruption action targeting the Lumma malware-as-a-service (MaaS) information stealer operation seized thousands of domains and part of its infrastructure backbone worldwide.
This effort involved multiple tech companies and law enforcement authorities, resulting in Microsoft's seizure of approximately 2,300 domains after legal action against the malware on May 13, 2025.
At the same time, the Department of Justice (DOJ) disrupted marketplaces where the malware was rented to cybercriminals by seizing Lumma's control panel, while Europol's European Cybercrime Center (EC3) and Japan's Cybercrime Control Center (JC3) helped to seize Lumma's infrastructure based in Europe and Japan.
"Between March 16, 2025, and May 16, 2025, Microsoft identified over 394,000 Windows computers globally infected by the Lumma malware. Working with law enforcement and industry partners, we have severed communications between the malicious tool and victims," said Steven Masada, Assistant General Counsel of Microsoft's Digital Crimes Unit.
"The Lumma Stealer disruption effort denies the Lumma operators access to their control panel, marketplace of stolen data, and the Internet infrastructure used to facilitate the collection and management of that data. These actions impose operational and financial costs on both the Lumma operators and their customers, forcing them to rebuild their services on alternative infrastructure," Cloudflare added today.
Other companies involved in the joint action against Lumma's infrastructure include ESET, CleanDNS, Bitsight, Lumen, GMO Registry, and global law firm Orrick.
 Domain seizure banner (Microsoft)
Domain seizure banner (Microsoft)Cloudflare says Lumma Stealer abused their services to hide the origin IP addresses of servers threat users to collect stolen credentials and data.
Even after suspending domains used by the operation, the nalware was able to bypass Cloudflare's interstitial warning page, causing the company to take extra steps to block data exfiltration.
"Cloudflare's Trust and Safety team repeatedly flagged domains used by the criminals and suspended their accounts," explains a Cloudflare report.
"In February 2025, Lumma’s malware was observed bypassing Cloudflare’s interstitial warning page, which is one countermeasure that Cloudflare employs to disrupt malicious actors."
"In response, Cloudflare added the Turnstile service to the interstitial warning page, so the malware could not bypass it."
What is Lumma malware?
Lumma (also known as LummaC2) is a malware-as-a-service information stealer targeting Windows and macOS systems that cybercriminals can rent for a subscription between $250 and $1,000.
The malware comes with advanced evasion and data theft capabilities, and it's commonly distributed through various channels, including GitHub comments, deepfake nude generator sites, and malvertising to infect victims.
After compromising a system, Lumma can steal data from web browsers and applications, including cryptocurrency wallets and cookies, credentials, passwords, credit cards, and browsing history from Google Chrome, Microsoft Edge, Mozilla Firefox, and other Chromium browsers.
This stolen data is then collected into an archive and sent back to attacker-controlled servers, who will sell the information on cybercrime marketplaces or use it in other attacks.
The infostealer first became available for purchase on cybercrime forums for the first time in December 2022, and KELA reported that it became popular among cybercriminals just a few months later.
As IBM X-Force's 2025 threat intel report notes, there has been a 12% increase in infostealer credentials for sale on the dark web over the last year, following a massive 84% increase in infostealers delivered via phishing, with Lumma being the most prevalent by a large margin.
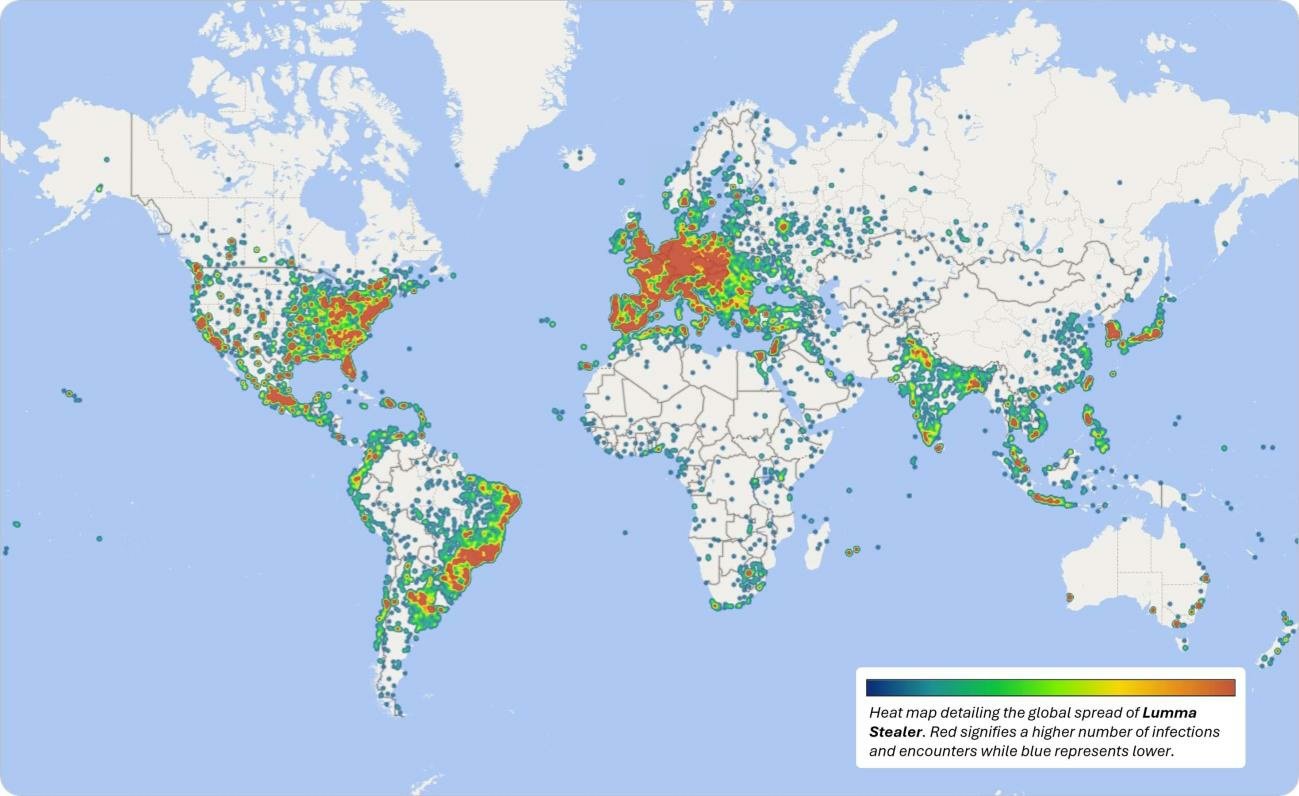 Lumma infections heat map (Microsoft)
Lumma infections heat map (Microsoft)Lumma has been used in massive malvertising campaigns that have impacted hundreds of thousands of PCs and by many notorious threat groups and actors, including the Scattered Spider cybercrime collective.
Most recently, data stolen using information-stealing malware has been behind high-impact breaches at PowerSchool, HotTopic, CircleCI, and Snowflake.
Besides being used to breach corporate networks, credentials stolen by infostealer malware have also been used to cause chaos by corrupting network routing information, as shown by threat actors hijacking Orange Spain RIPE account to misconfigure BGP routing and RPKI configurations.
.png)
 2 days ago
34
2 days ago
34





