This newsletter is brought to you by Zero Networks. You can subscribe to an audio version of this newsletter as a podcast by searching for "Risky Business" in your podcatcher or subscribing via this RSS feed.
More than 12 years after the issue was first reported, the Association of American Railroads is replacing an insecure railroad protocol that can be abused to engage brakes and bring trains to sudden stops anywhere across North America.
The issue impacts a radio protocol that links locomotives (Head-of-Train) to devices mounted on the last wagon, a flashing red light known in the industry as an End-of-Train device or a FRED (Flashing Red End Device).
This device is primarily used to collect telemetry from the back of trains. It is useful especially for long freight trains that can often go over one or two miles in length and which cannot be easily inspected.
Besides telemetry, the devices can also accept commands from conductors, and the most important of these is the ability to break the train from the back, instead of the front.
Back in 2012, a hardware security researcher named Neil Smith discovered that the radio protocol used to send commands from locomotives to EoT devices used a weak form of authentication—a simple BCH checksum.
Smith says that an attacker with hardware as cheap as $500 and a software-defined radio (SDR) could create packets and issue commands to the EoT device to suddenly engage the brakes.
"Distance is a function of gain and radio line of sight," Smith told Risky Business. "The EOT/HOT as designed, really only works over a couple of miles, as it is not uncommon to have a train that is 3 miles long in some cases. If you were in a plane, you don't need a lot of power to be heard at 457Mhz over 150 miles."
Exploiting this would have catastrophic effects. Sudden braking can cause passenger injuries, derailments, and transportation disruptions.
Smith first reported the weak authentication to ICS-CERT in 2012, which then contacted the protocol's owner, the American Association of Railways (AAR).
The AAR played down the issue for years as only a theoretical threat. Smith offered to prove it in practice, but the AAR just didn't want to hear about it.
"The AAR would never authorize the test track facility in Pueblo, CO, for us to try this on a real train. Which is ironic because it is a facility owned by the FRA (Federal Railroad Administration)," Smith told us.
"The lack of real-world testing was also why the AAR would not acknowledge it as a 'real' issue."
Since the AAR refused to patch the protocol, Smith disclosed the issue publicly in a Boston Review article, only to have it immediately refuted a week later by the AAR in a Fortune piece.
In a Twitter thread on Friday, Smith says he kind of gave up on the bug after the Fortune article, seeing the AAR's stubbornness in even recognizing it had a problem.
Obviously, this didn't die out that easy, and another security researcher, Eric Reuter, also stumbled upon the same thing two years later, and even presented at DEFCON.
Nothing moved again, but Smith says he decided to try again one more time.
"I pushed them to reopen the case in summer 2024," Smith tells us. "With Eric Reuter independently also finding the same issue, it strengthened the push this time that I was not just making it all up."
This time, the needle moved. The issue received a CVE identifier (CVE-2025-1727) and, last week, CISA published an advisory, 12 years after the initial discovery.
Yikes. Turns out you can send a plaintext radio signal to cause any train in the USA to do an emergency break. The original 'security' was just a checksum, no encryption or authentication. Reporting this took them 12 years (!) because the vendor dismissed it initially www.cisa.gov/news-events/...
— Mathy Vanhoef (@vanhoefm.bsky.social) 2025-07-12T12:14:19.766ZThe advisory comes two months after the AAR itself announced plans to replace the old HoT/EoT protocol with IEEE 802.16t Direct Peer-to-Peer (DPP), a protocol that supports both security and lower latency.
This involves a massive job of physically replacing over 75,000 EoT devices on trains across the US, Canada, and Mexico.
"It will come down to the speed at which they can replace roughly 75,000 devices in North America. They hope to start rolling out new devices in 2026, but I expect this will take roughly 5-7 years to fully mitigate," Smith told Risky Business over the weekend.
"I also estimate that this will cost between $7-10 billion to remediate."
At that price tag, this explains why the AAR kept playing down the issue and delaying the protocol's deprecation.
But now with the finer-grained details out in the open, this also opens the door for abuse. So far, Smith says he has not learned of any attacks exploiting his bug.
Detecting if the bug is abused should be easy, he says.
"As long as the hardware is recoverable after an accident, there is sufficient logging in place to tell if a HoT emitted a command that was received by the EoT and vice versa. There would be a log on an EOT receiving a command that was not logged as being generated by the HoT."As for the chances this gets abused? They are pretty high.
Almost two years ago, in August 2023, unknown individuals used a similar technique to disrupt train traffic around the city of Szczecin. They used a different technique, since train signaling protocols are different in Europe, but the result was the same—trains stopped dead in their tracks, bringing local rail traffic to a halt.
According to WIRED, the saboteurs issued three acoustic tones to trigger emergency brakes, and also interspersed the commands with the Russian national anthem and parts of a speech by Russian president Vladimir Putin. The hack took place as Poland became a central hub for the delivery of war supplies to Ukraine after Russia's invasion of Ukraine.
With the US still being involved in supplying Ukraine, and also dipping its toes in attacks on Iran this summer, this is a godsend for lazy saboteurs.
Mitigations for this are almost nonexistent. As Smith said earlier, this will come down to the speed at which the devices can be replaced.
Risky Business Podcasts
The main Risky Business podcast is now on YouTube with video versions of our recent episodes. Below is our latest weekly show with Pat and Adam at the helm!
Breaches, hacks, and security incidents
Researchers stop Lazarus crypto backdoor attack: A team of security researchers has foiled a supply chain attack against the cryptocurrency community last week. A backdoor in thousands of smart contracts could have allowed hackers to steal over $10 million worth of assets. Researchers worked with crypto companies to move the funds before the attackers could exploit the issue. The team believes North Korean hackers were behind the backdoor. [Additional coverage in CoinTelegraph/Twitter thread]
MoonPay BEC scam: The MoonPay cryptocurrency exchange has fallen victim to a BEC scam. The exchange sent $250,000 to scammers impersonating the Donald Trump inaugural committee and seeking a donation. The FBI recovered 16% of the scammed funds. [Additional coverage in NOTUS]
Hacker steals and returns Texture funds: A hacker has stolen $2.2 million worth of crypto-assets from the Texture DeFi platform. Texture says it was able to negotiate with the hacker and recover 90% of the funds a day after the hack. The hacker was allowed to keep the rest as a "bug bounty" reward.
GMX hacker returns most funds: A hacker has returned assets they stole from the GMX cryptocurrency platform. GMX allowed the hacker to keep $5 million worth of assets in the form of a bug bounty reward. The company offered the reward last week after losing $42 million following a smart contract exploit. GMX promised not to pursue charges if the hacker returned 90% of the stolen assets. [Additional coverage in Yahoo Finance]
Chinese hackers breach DC law firm: Suspected Chinese hackers have breached the email servers of a powerful Washington, DC, law firm. Wiley Rein notified customers of the breach in a memo sent out last week. The company attributed the intrusion to hackers affiliated with the Chinese government. Wiley Rein is known for representing customers in regulatory and transnational cases, with lawyers often ending up serving in the US government. [Additional coverage in CNN]
Law firm settles hacking lawsuits: US law firm Dechert has settled two lawsuits that accused it of using hacker-for-hire services to collect data for past lawsuits. The company settled the lawsuits without any admission of liability. [Additional coverage in Reuters]
General tech and privacy
Microsoft rolls out JScript9Legacy: Microsoft has replaced JScript in Windows 11 with a new scripting engine. The new JScript9Legacy is now the default scripting engine in Windows 11, for version 24H2 and later. Microsoft says the new engine uses more modern web standards and comes with many security features. The old JScript engine has been the default JavaScript engine in Windows since the mid-90s.
Atlassian EU alternatives: The XWiki and the OpenProject plan to build EU "digital soverign" versions of Atlassian's JIRA and Confluence products.
France to investigate Twitter over algorithm manipulation: The French government launched a criminal investigation into Twitter over alleged manipulation of its algorithms. A complaint accused Twitter of changing its algorithm to spread "an enormous amount" of hateful and racist content designed to skew democratic debate in France. Authorities say the manipulation is considered foreign interference. [Additional coverage in Politico Europe/French government complaint PDF]
Coincidentally, today is the anniversary of the EU Commission’s preliminary findings that X is in breach of the Digital Services Act - which it has conspicuously failed to follow up on. Did this apparent attempt to appease Trump really work?
— Steve Peers (@stevepeers.bsky.social) 2025-07-12T14:06:00.018ZGovernment, politics, and policy
UN cybersecurity mechanism: The United Nations Open-Ended Working Group on Cybersecurity (UNcyberOEWG) has created a permanent mechanism for dealing with cybersecurity issues at the UN. [UN document PDF]
United Nations Open-Ended Working Group on Cybersecurity (#UNcyberOEWG) adopts final report, establishing - for the first time - a permanent mechanism on cybersecurity at the United Nations. The content of the report and the modalities of the permanent mechanism are far from perfect, /1
— Alexandra Paulus (@alexandrapaulus.bsky.social) 2025-07-11T15:12:25.338ZEU AI Code of Practice: The European Commission has published its long-awaited AI Code of Practice, a set of voluntary rules to help AI companies comply with the EU's AI Act.
EU drops digital tax on tech giants: The EU has allegedly dropped a proposed digital tax on major tech giants, most of which are American, as part of a plan to appease Trump's tariff craziness. [Additional coverage in Politico Europe]
Life beyond Cyber Command: Congress wants the DOD to look at alternatives to using cyber on the battlefield without constant involvement of Cyber Command in each operation. [Additional coverage in DefenseScoop]
US GEC shutdown investigation: An investigation from The Telegraph claims that the State Department staffer behind the move to dismantle the agency's anti-disinformation office, the Global Engagement Center, is a staunch Putin fanboy, married to a Russian woman, and has ties to several Russian oligarchs.
Trump's DOJ comes to the help of conspiracy theories: The US DOJ has filed a statement in support of a lawsuit against major news outlets that deplatformed stupid COVID-19 conspiracy theories. Oh, I'm sorry. That's "suppress competition from independent perspectives that rival mainstream media," yadda yadda yadda!
Czechia declares DeepSeek a national security threat: Czechia's intelligence service has classified China's DeepSeek LLM as a national security threat.
Spain taps Huawei for wiretaps: The Spanish government has awarded Huawei a contract to manage its phone wiretapping infrastructure. The government awarded the contract despite US and EU concerns about the Chinese government's control over the company. Several EU countries have previously excluded the company from their 5G infrastructure on the grounds of possible espionage and national security. [Additional coverage in The Record]

In this Risky Business sponsored interview, Zero Networks Field CTO, Chris Boehm discusses the everyone-gets-an-AI future with Casey Ellis. Zero Networks makes network microsegmentation achievable without simply handing an AI control of the network. Will generative artificial intelligence ever be trusted to make hard access control decisions?
Arrests, cybercrime, and threat intel
Indonesia extradites Russian leaker: Indonesian authorities have extradited a Russian national back to Moscow to face charges in a cybercrime case. Alexander Zverev allegedly sold the data of Russian citizens on Telegram for years before fleeing the country in March 2022. Russian officials claim Zverev sourced the information from official government and telco databases. [Additional coverage in RIA/English coverage in The Record]
Major prison sentences for Thai scam center gang: A Thai court has sentenced 71 defendants to prison for their involvement in a major cyber scam operation. The suspects, 52 Chinese and 19 Thais, were detained in March of last year. They were described as the country's biggest cyber scam gang. The biggest sentences were handed out to the gang's leaders, with each receiving 24 years in prison. [Additional coverage in the Bangkok Post]
Scam call center raided in India: Indian authorities have raided a cyber scam call center in the city of Noida. Two individuals have also been arrested. According to the UK National Crime Agency, the call center engaged in tech support scams that mimicked Microsoft services.
Crypto scammer gets an additional 12 years: A US court has sentenced a crypto scammer to an additional 12 years in prison after he failed to pay back one of his victims. Nicholas Truglia was initially sentenced to 18 months in prison in December 2022. He used a SIM swapping attack to steal more than $20 million worth of crypto assets from one victim. US officials say that despite owning over $53 million in assets, Truglia avoided restitution efforts and continued spending on himself. [Additional coverage in Bloomberg/Court documents here]
FBI seizes video game piracy sites: The FBI has seized seven sites offering pirated video games and other content. [Additional coverage in Kotaku]
New npm malware: One hundred ninety-one malicious npm packages were discovered and taken down last week. Check out the GitHub security advisory portal for more details.
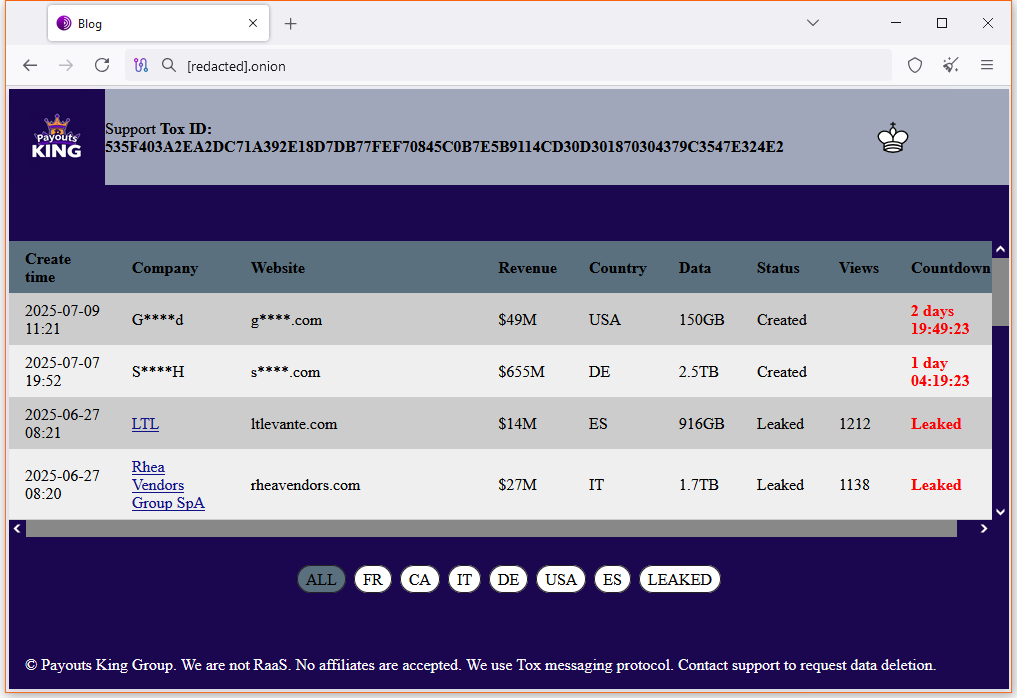
Payouts King leak portal: A threat actor named Payouts King has launched a data leak portal last week. The group claims it's not a RaaS.
NFC fraud schemes spread to the Philippines: Chinese mobile malware groups that rely on NFC relay attacks have now spread to the Philippines, per new Resecurity research.
Mastodon scam campaign: Mastodon users are getting targeted with a "verify your account" scam that asks them to click on malicious links and verify accounts.
Post by @[email protected]
View on Mastodon
Malware technical reports
BlackSuit ransomware: Cybereason has published a technical analysis of the BlackSuit ransomware.
SLOW#TEMPEST malware obfuscation: PAN Unit42 has published an analysis of new obfuscation techniques used by the SLOW#TEMPEST group in its malware. This new technique uses dynamic jumps and obfuscated function calls to avoid detection. The SLOW#TEMPEST group was first spotted last year targeting Chinese-speaking users with Cobalt Strike and Mimikatz payloads.
NordDragonScan: Fortinet's security team has spotted a new infostealer operation named NordDragonScan.
Zero Networks is offering a comprehensive guide that highlights the growing importance of advanced microsegmentation in a security landscape.

APTs, cyber-espionage, and info-ops
Suspected Belarusian APT targets Poland: Security researcher dmpdump has spotted a suspected Belarusian espionage campaign targeting Polish organizations.
"These CHM files are very likely associated with a threat actor tracked as FrostyNeighbor and UNC1151, historically attributed to Belarus. Previous targeting documented in reports such as the following suggest an interest in Ukraine, Lithuania, Latvia, Poland, and Germany, which is consistent with the upload geography for these malicious CHM files."Storm-1516 disinfo campaign: Per the Gnada Project, a notorious Russian disinformation group known as Storm-1516 is using the identities of known journalists to plant fake stories online that target and discredit Armenian, French, and Moldovan authorities. [Additional coverage in The Insider]
Vulnerabilities, security research, and bug bounty
NVD drama: MIT Technology Review has published a look at NIST's efforts to address the NVD's humongous and ever-growing backlog.
Grok-4 jailbreak: NeuralTrust has jailbroken the new xAI Grok-4 assistant two days after its release. The company says it combined two previous attacks, known as Echo Chamber and Crescendo, to break Grok-4.
GPUHammer attack: A team of academics has adapted the Rowhammer attack to work on GPU memory for the first time. Rowhammer previously only worked with random access memory, also known as RAM. The new GPUHammer attack allows a malicious GPU user to trigger bit flips in the GPU memory and tamper with another user's data in shared GPU environments. The attack was successfully tested against GPUs used for AI workloads, where it sabotaged an AI model and reduced its accuracy from 80% to almost zero.
New AMD side-channel attacks: AMD has released firmware updates to patch four new side-channel attacks in its processors. The vulnerabilities were discovered last year by Microsoft during testing. The company developed a tool that would test microarchitectural isolation between virtual machines, the kernel, and OS processes. Affected AMD CPUs include its EPYC, Ryzen, and Athlon series.
Gigabyte firmware vulnerabilities: Motherboard manufacturer Gigabyte has failed to patch four vulnerabilities in its UEFI firmware. The vulnerabilities can allow attackers to take over the System Management Mode (SMM), a highly privileged section of the CPU. According to the Carnegie Mellon University CERT, Gigabyte failed to implement AMI upstream patches that would have addressed the issues. The initial vulnerabilities were discovered by firmware security firm Binarly [1, 2, 3, 4].
Laravel APP_KEY vulnerability: Synacktiv and GitGuardian researchers have discovered a vulnerability in the Laravel PHP framework that can be used to automatically deserialize decrypted data and enable RCE attacks on Laravel sites. The attack works only if an attacker has access to a Laravel site's secret APP_KEY encryption/decryption key. An internet scan found over 260,000 leaked APP_KEYs, which goes against the concept of a "secret encryption key." Nice job, devs!
Fortinet PoC for pre-auth SQLi is out: Security researchers have published proof-of-concept code for a major vulnerability in Fortinet FortiWeb firewalls. Tracked as CVE-2025-25257, the bug is a pre-authentication SQL injection in the device's web interface. It allows attackers to inject malicious code into the database and then have it executed and take over the firewall appliance. Fortinet released security updates last week.
Kaseya RapidFire vulnerabilities: The Kaseya RapidFire network scanner stores credentials for the networks and devices it needs to scan in an insecure manner. Security firm Galactic Advisors says credentials are stored in cleartext inside temporary files or using a weak and reversible form of encryption. This allows attackers with access to a compromise system to extract the credentials and move laterally across a network. Kaseya has released security updates for both issues.
ServiceNow write-up: The Varonis team has published a write-up on a ServiceNow bug they found and got patched last week. Tracked as CVE-2025-3648, the vulnerability allows threat actors to infer data from the Now Platform without authentication.
Windows kernel write-up: StarLabs has published a technical analysis of CVE-2024-30088, an EoP in the Windows kernel code.
Node.js security updates: The Node.js team will release important security updates this Tuesday, on July 15.
CISA tells agencies to patch CitrixBleed 2 within a day: CISA says hackers are exploiting the CitrixBleed 2 vulnerability to take over Citrix ADC and NetScaler appliances. CISA gave federal agencies one day to patch the vulnerability. Federal agencies had until the end of the day Friday to patch their systems. This is a departure from standard CISA procedures, as the agency typically gives a three-week deadline for most patches.
Post by @[email protected]
View on Mastodon
Infosec industry
Threat/trend reports: Binarly, Check Point, Cisco Talos, Curator, CyFirma, Lookout, and the Singapore CSA have recently published reports and summaries covering various infosec trends and industry threats.
New tool—pqcscan: Security firm Anvil Secure has released pqcscan, a new tool to scan SSH and TLS servers for their support of Post-Quantum Cryptography algorithms.
New tool—KubeForenSys: Security firm Invictus IR has open-sourced KubeForenSys, a tool for collecting Kubernetes cluster data and ingesting it to Azure Log Analytics workspaces for analysis post-compromise.
RuhrSec 2025 videos: Talks from the RuhrSec 2025 security conference, which took place in February, are available on YouTube.
Risky Business podcasts
In this edition of Seriously Risky Business, Tom Uren and Amberleigh Jack talk about our developing understanding of the group that people call Scattered Spider. Independent security firms agree that there are a small number of key people who are driving the group's outrageous success.
In this edition of Between Two Nerds, Tom Uren and The Grugq talk about how there is an opportunity for the US to expand its zero-day and talent acquisition pool to Asia. They revisit a paper comparing the Chinese and American zero-day acquisition strategies and have some quibbles.
.png)



