A malicious npm typosquat uses remote commands to silently delete entire project directories after a single mistyped install.
Socket’s Threat Research Team discovered an npm supply chain attack involving typosquatting and remote code execution. The malicious package xlsx-to-json-lh typosquats the legitimate Excel-to-JSON converter xlsx-to-json-lc, differing by just one letter.
Published in February 2019, this package contains a hidden payload that establishes a persistent connection to a command and control (C2) server. When triggered, it can delete entire project directories without warning or recovery options. The package remained undetected on npm for six years before discovery. As of this writing, it remains live on the registry. We have formally petitioned for its removal. Notably, our research found that other packages published by the maintainer leonhard appear to be legitimate, non-malicious packages, suggesting this was a targeted attack rather than a broader campaign.
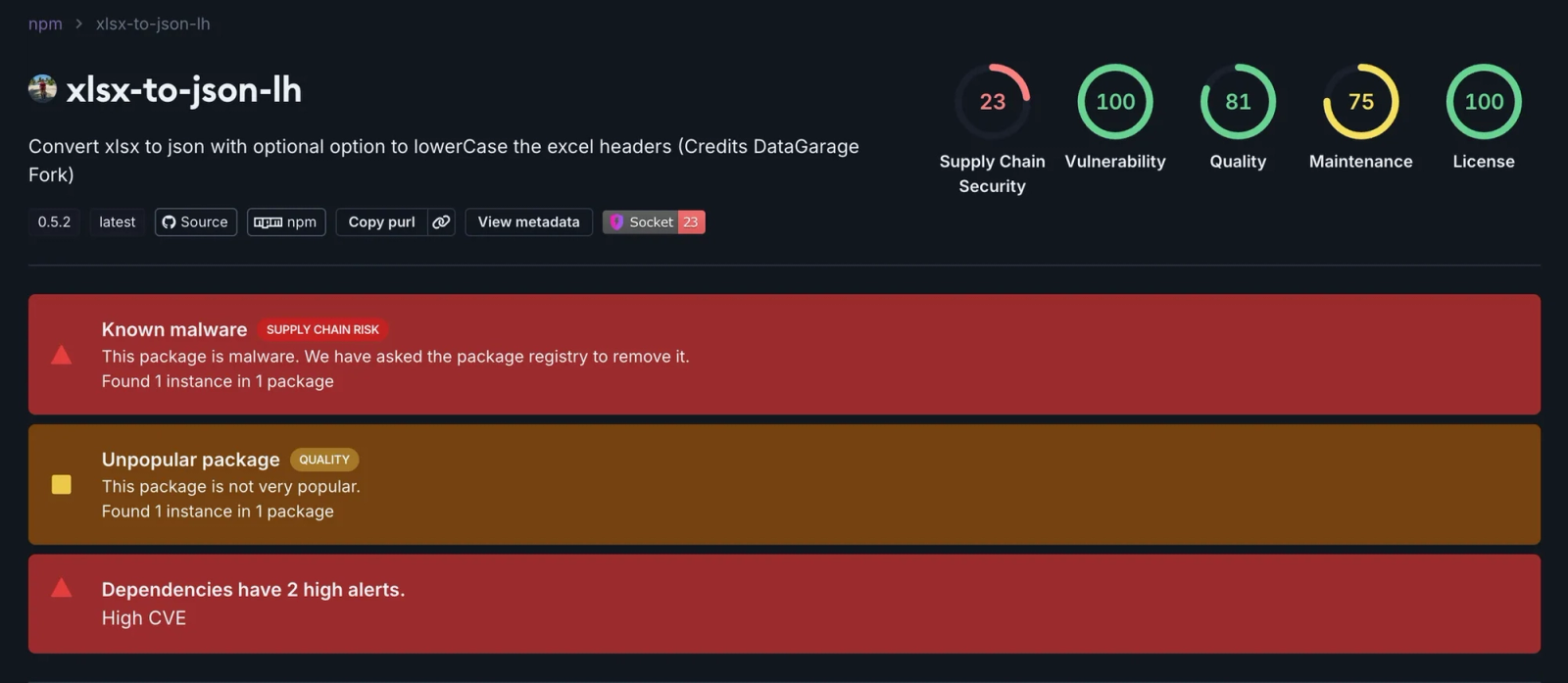 Socket's AI Scanner flagging the malicious package xlsx-to-json-lh as "Known malware"
Socket's AI Scanner flagging the malicious package xlsx-to-json-lh as "Known malware"Exploiting Simple Typing Mistakes#
The legitimate package xlsx-to-json-lc [~500k downloads] has served developers reliably since 2016, for converting Excel spreadsheets into JSON format. The attacker exploited this popularity by creating xlsx-to-json-lh, where the "lc" to "lh" substitution targets a single letter typing mistake.
Legitimate Package: xlsx-to-json-lc (Author: rahil471)
Malicious Package: xlsx-to-json-lh (Impersonates rahil471, under the npm alias leonhard )
The malicious package leverages trust by retaining the original author's metadata while adding a new maintainer:
"_npmUser": { "email": "hofferouandi@yahoo[.]fr", "name": "leonhard" }, "_npmVersion": "3.5.2", "_phantomChildren": {}, "_requested": { "name": "xlsx-to-json-lh", "raw": "xlsx-to-json-lh@^0.5.2", "rawSpec": "^0.5.2", "scope": null, "spec": ">=0.5.2 <0.6.0", "type": "range" }, "_requiredBy": [ "/" ], "_shrinkwrap": null, "_spec": "xlsx-to-json-lh@^0.5.2", "_where": "/projects/Deploy/syscohada-v3/server", "author": { "email": "rahilsk47@gmail[.]com", "name": "rahil471", "url": "http://ciphertrick[.]com/" }Malicious package xlsx-to-json-lh package.json fileThis creates a facade of legitimacy, developers see the trusted author name and assume safety.
The French Connection#
Several indicators point to a French-speaking threat actor:
- Maintainer email: hofferouandi@yahoo[.]fr (French domain)
- Trigger command: "remise à zéro" (French phrase meaning “reset to zero”)
Unlike crude malware that immediately breaks functionality, xlsx-to-json-lh uses a trojan horse approach. The package includes working Excel conversion code, allowing it to pass basic functionality tests while hiding its true purpose.
File Structure and Execution Flow#
xlsx-to-json-lh/ ├── index.js // Wrapper file ├── libs/ │ ├── index.js // Loads malware + provides Excel functionality │ └── support/ │ └── index.js // THE MALWARE (socket.io client) └── package.json // Contains legitimate author info to build trustHow the Payload Executes#
When a developer imports the package:
- The main index.js requires ./libs/index.js
- libs/index.js immediately loads the malicious payload:
- The malicious libs/support/index.js establishes a persistent WebSocket connection and waits for commands:
No additional user interaction required, the malware activates immediately upon import and maintains a persistent connection, waiting silently for the destruction command.
Consequences of Payload Execution#
Once triggered with the French command "remise à zéro" (reset), the payload calculates your project root and recursively deletes everything:
- Source code files
- Version control data (.git directory)
- Configuration files
- node_modules (including itself)
- All project assets
Recovery is virtually impossible without external backups.
Impact and Scope#
The attack's true danger lies in its scalability. Consider a typical development environment:
/home/dev/projects/ ├── client-website/ [infected with xlsx-to-json-lh] ├── internal-api/ [infected with xlsx-to-json-lh] ├── data-processor/ [infected with xlsx-to-json-lh] └── mobile-backend/ [clean]With one command from the attacker, three projects vanish simultaneously. For organizations with multiple developers, the impact multiplies 20 developers with 2-3 infected projects each means 40-60 codebases destroyed instantly.
Outlook and Recommendations#
The xlsx-to-json-lh attack demonstrates how typosquatting combined with trojan functionality creates devastating supply chain compromises. One mistyped character during package installation leads to complete project loss a solid reminder that in modern development, security is only as strong as your weakest dependency.
This attack illustrates severe consequences of supply chain vulnerabilities:
- Instant Damage: Projects deleted with no warning or recovery
- Difficult Detection: Legitimate functionality masks malicious behavior
- Trust Exploitation: Uses real author's reputation for credibility
- Multiplier Effect: One package can destroy countless projects
This incident suggests concerning patterns that will likely shape future attacks:
- Expect attackers to implement longer dormancy periods, potentially waiting months before activation to maximize infection spread, with future variants using time-based triggers or waiting for specific version updates before revealing malicious behavior.
- Attackers have started moving beyond single Heroku instances to distributed command networks, using legitimate services like GitHub Gists, Pastebin, or even blockchain-based messaging to issue commands, making takedowns significantly more difficult.
- Rather than wholesale deletion, advanced variants could selectively destroy or exfiltrate specific file types such as .env files, private keys, or source code while leaving the rest intact to avoid immediate detection.
- The French command "remise à zéro" suggests regional targeting, and future attacks might use geolocation or system language settings to activate only in specific regions, evading researchers in other locations.
- As package names become more complex, attackers will likely use AI to generate convincing typosquats that account for keyboard layouts, common developer typos, and phonetic similarities across languages.
Socket's security tools can help protect against these threats by analyzing package behaviors in real-time to detect dangerous patterns like those seen in this campaign. Our free GitHub app flags risks directly in pull requests, the CLI alerts during package installations, and our browser extension provides security insights on npm package pages helping developers identify potential supply chain threats before they enter your codebase.
Indicators of Compromise (IOCs)#
- Malicious Package: xlsx-to-json-lh
- Threat Actor Identifiers
- npm alias: leonhard
- npm Registration email: hofferouandi@yahoo[.]fr
- C2 Server: informer-server[.]herokuapp[.]com
MITRE ATT&CK#
- T1195.002 — Supply Chain Compromise: Compromise Software Supply Chain
- T1059.007 — Command and Scripting Interpreter: JavaScript
- T1485 — Data Destruction
- T1036.005 — Masquerading, Match legitimate name or location
- T1071.001 — Application Layer Protocol: Web Protocols
- T1102 — Web Service: Bidirectional Communication
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it nowReady to block malicious and vulnerable dependencies?

Product
Secure Your AI-Generated Code with Socket MCP
Socket MCP brings real-time security checks to AI-generated code, helping developers catch risky dependencies before they enter the codebase.
By Alexandros Kapravelos - May 28, 2025
.png)




