Today, I’m happy to announce that external-secrets-operator will have an MFA / TOTP token generator once this PR is merged and released. This opens up some exciting new features.
For example, imagine having an AWS session that requires MFA, or you have an Azure flow that requires a TOTP token. Now, you can achieve that using automation and an MFA generated in a secret.
Just define a generator:
Where the secret is something like this:
And then add an ExternalSecrets object:
Here are some images that set up this MFA device on an AWS account:
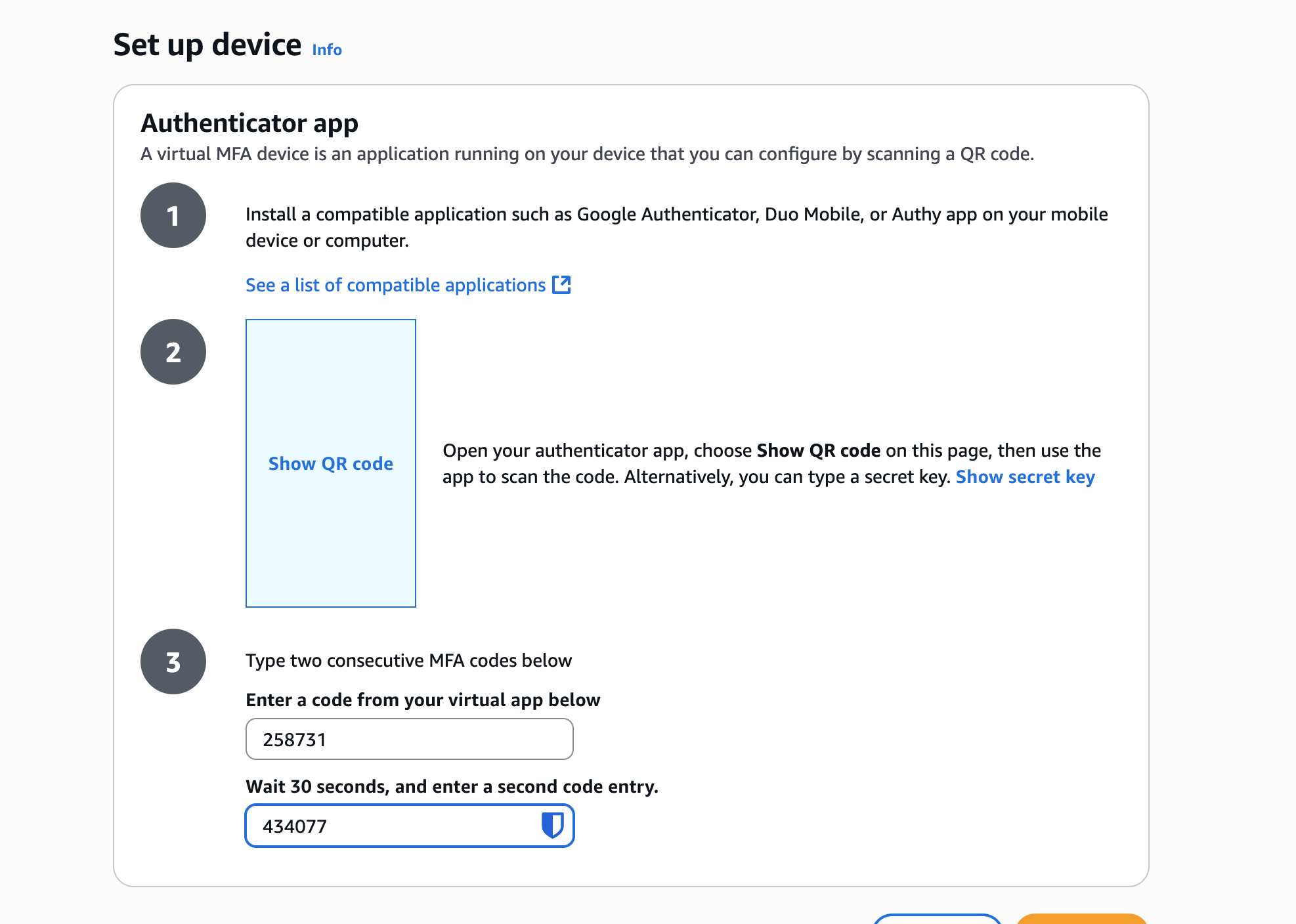
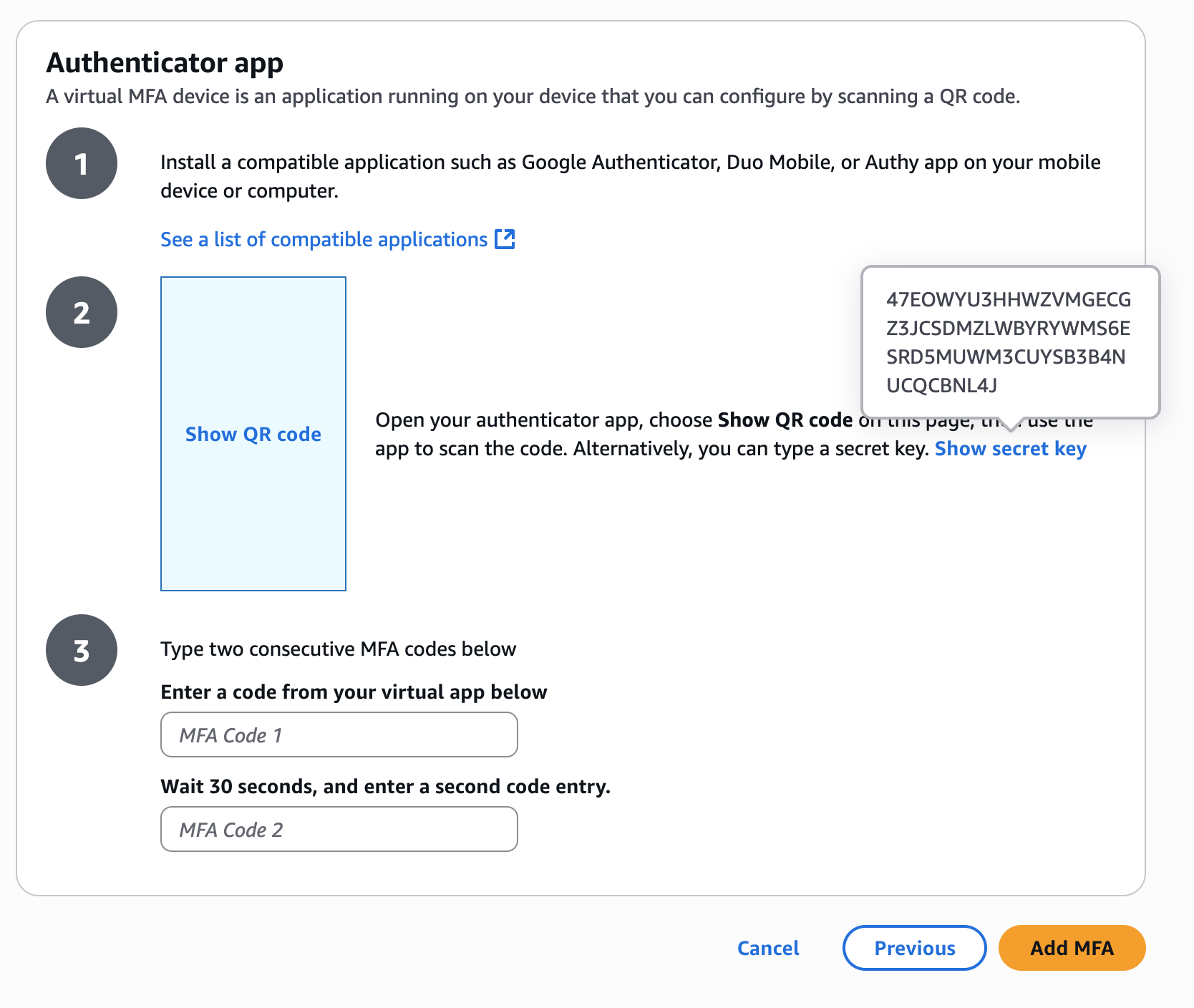
To show the secret that needs to be provided to the MFA generator, simply click on Show secret key.
 .
.
Sometimes a provider will require some additional configs. For example, a longer token ( longer than 6 digits ) or a longer time ( default is 30 seconds ) or a different encoding scheme ( default from the RFC is SHA1 ).
These all can be configured with the following fields:
| length | 6 | Digit length of the generated code. Some providers allow larger tokens. |
| timePeriod | 30 | Number of seconds the code can be valid. This is provider specific, usually it’s 30 seconds |
| secret | empty | This is a secret ref pointing to the seed secret |
| algorithm | sha1 | Algorithm for encoding. The RFC defines SHA1, though a provider will set it to SHA256 or SHA512 sometimes |
Have fun!
.png)



