As vulnerability data bottlenecks grow, the federal government is formally investigating NIST’s handling of the National Vulnerability Database.

The Office of Inspector General (OIG) at the U.S. Department of Commerce has initiated an audit into how the National Institute of Standards and Technology (NIST) manages the National Vulnerability Database (NVD), following months of mounting concern over stagnation and backlog.
NIST Faces Scrutiny Over NVD Breakdown#
In a memorandum dated May 20, 2025, addressed to NIST leadership, the OIG announced it is initiating an audit designed to evaluate the effectiveness of NIST’s "sustainable processes for managing NVD submission volumes," including how well it has executed strategies to reduce the NVD’s data backlog and prevent future delays.
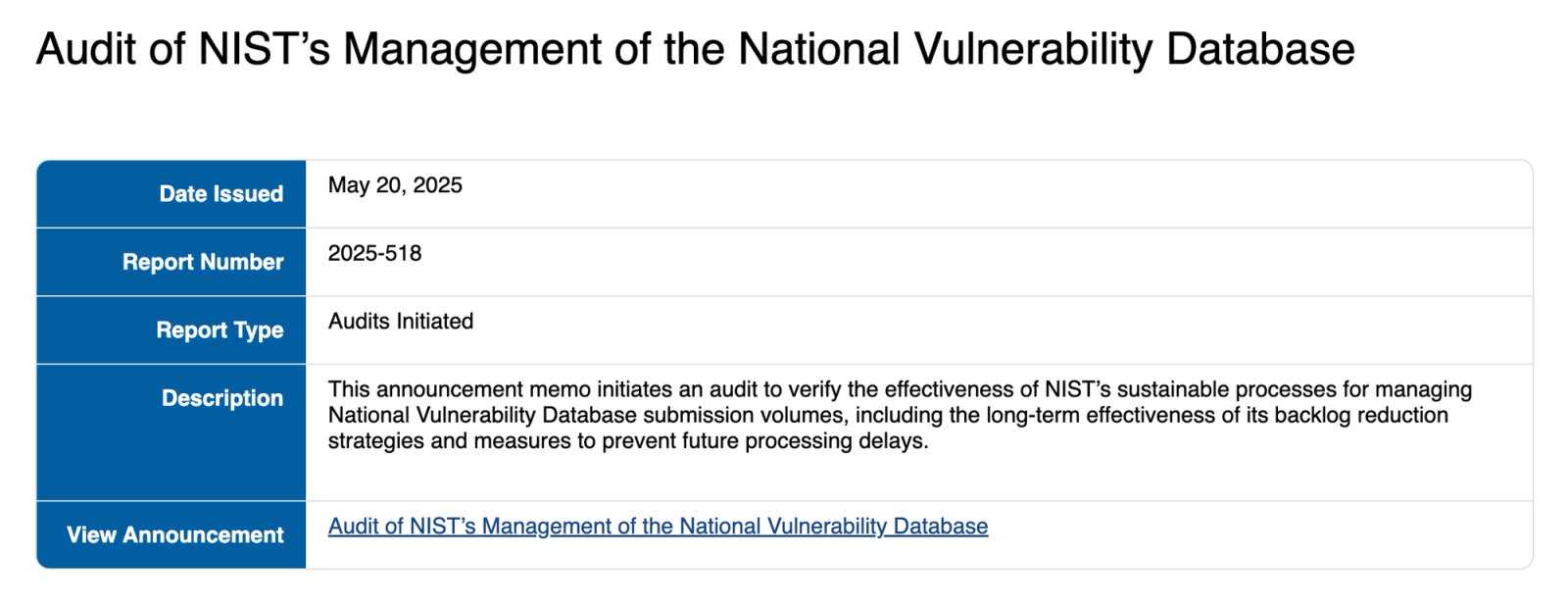
The audit comes at a critical time. Since funding issues hit the NVD in late 2023, its ability to enrich and publish vulnerability data at scale has steadily deteriorated. The number of Common Vulnerabilities and Exposures (CVEs) published without accompanying metadata such as CVSS scores or CPE tags has surged, affecting both private sector tooling and public sector cybersecurity operations that depend on timely, enriched vulnerability data.
CISA Hit by High-Level Departures and Budget Cuts#
While NIST’s NVD is now under federal audit, CISA, one of the primary operational consumers of NVD data and source of critical initiatives like KEV, is undergoing its own unraveling.
CISA has long relied on timely, enriched CVE metadata from the NVD to support alerts, advisories, and the widely referenced Known Exploited Vulnerabilities (KEV) catalog. But with NVD enrichment in freefall, and nearly than 100,000 CVEs now marked as “Deferred," CISA has begun publishing and enriching vulnerability data independently, a sign that it can no longer rely on the NVD as a single source of truth.
According to internal memos reported by The Washington Post, the heads of three of CISA’s six major divisions, along with top officials across finance, strategy, and infrastructure, are departing by the end of May. At the same time, Congressional Republicans are pushing for a 17% budget cut to the agency, which has already disbanded advisory panels like the Cyber Safety Review Board.
Security experts warn the U.S. is entering a more aggressive cybersecurity posture, especially toward China, while hollowing out the agencies that protect its own networks. Former national cyber director Harry Coker said local hospitals and schools are now facing advanced threats “every day” with little federal support. “We are not ready for a systemic cyberattack in our country,” warned retired Rear Adm. Mark Montgomery at RSA earlier this month.
As the CVE ecosystem splinters and alternative platforms like CVE.org attempt to rebuild trust in vulnerability metadata, CISA’s shrinking resources raise serious concerns about the U.S. government’s ability to detect, prioritize, and respond to threats in real time.
NVD’s Crisis Sparks Ecosystem Shifts#
While the U.S. government attempts to get the NVD back on track, alternative solutions are gaining traction. The CVE Foundation recently released a white paper proposing a sweeping roadmap for CVE.org to fill the gaps left by the NVD's decline.
The proposal includes development of a robust API, LLM-powered CNA matching, federated CPE maintenance, VEX support, and tooling improvements for CVE enrichment. One of the key goals: create backward-compatible APIs that allow existing systems relying on NVD data to migrate smoothly to CVE.org.
Vulnerability researcher Andrey Lukashenkov commented on LinkedIn that the CVE Foundation aims to “fill the gap left by the NVD, enable backward compatibility on the API level, [and] integrate its data as a historical backfill.” However, he expressed concerns over the ambiguity in the Foundation’s role and language, calling the current messaging “disappointing” and suggesting such a roadmap would carry more weight coming from the CVE Board itself.
A Turning Point for Vulnerability Infrastructure#
The timing of the audit coincides with broader efforts to modernize the CVE ecosystem and meet emerging regulatory requirements like the EU’s Cyber Resilience Act. The CVE Foundation’s roadmap outlines one possible path forward, but much of the ecosystem continues to rely on NIST’s infrastructure for enriched vulnerability data.
With the NVD facing sustained operational challenges and CISA adapting its own processes to fill the gap, the U.S. government’s approach to vulnerability management is clearly in transition. The outcome of the audit, and how quickly NIST can demonstrate meaningful progress, will likely influence how stakeholders across the industry plan for long-term data reliability.
In the meantime, enrichment gaps persist, and alternative platforms are gaining traction. The results of this audit may help determine whether NIST remains central to the future of vulnerability intelligence or whether that role continues to shift elsewhere.
Subscribe to our newsletter
Get notified when we publish new security blog posts!
Try it nowReady to block malicious and vulnerable dependencies?
.png)




