When it comes to Single Sign-On (SSO), two protocols dominate the landscape: SAML (Security Assertion Markup Language) and OIDC (OpenID Connect). Both serve the purpose of federated identity, letting users sign in once and access multiple applications. However, they approach the problem in very different ways.
Suppose you’re building or scaling a SaaS product or integrating with enterprise identity systems. In that case, this post breaks down how SAML and OIDC differ in architecture, token structure, developer experience, and real-world usability. For a deeper dive into the fundamentals of SSO protocols, you might find our guide on Understanding Key SSO Protocols and Their Use Cases helpful.
Table of Contents
- What Is SAML?
- What Is OIDC?
- Key Differences at a Glance (Comparison Table)
- Token Format: XML vs JSON
- Developer Experience: Implementation, Tooling, Community
- Security Models and Vulnerabilities
- Mobile & SPA Compatibility
- Migration: Moving from SAML to OIDC
- Regulatory Compliance Mapping
- When to Use Each
- Conclusion
What Is SAML?
SAML is an older protocol, dating back to 2002, designed primarily for enterprise SSO use cases. If you’re interested in a more detailed exploration of SAML, our article A Deep Dive into SAML provides a comprehensive overview.
SAML uses XML-based assertions and communicates over browser redirects. SAML is heavily adopted in enterprise environments like Okta, Ping Identity, and ADFS.
- Token format: XML Assertion
- Transport: Browser redirect via HTTP POST
- Primary use: Enterprise web SSO
What Is OIDC?
OIDC, released in 2014, is an authentication layer built on top of OAuth 2.0. New to these protocols or trying to understand where OIDC fits in? This guide to SAML, OAuth, and other auth protocols walks through it simply.
OIDC uses JSON Web Tokens (JWTs) and supports both browser and API-based flows. It’s a better fit for modern applications, SPAs, and mobile apps. To learn more about how OIDC enhances OAuth 2.0 for identity management, check out our article Is OIDC the Same as OAuth2? Do You Need OIDC for Login?.
- Token format: JWT
- Transport: HTTPS via REST APIs
- Primary use: Web/mobile login, modern SaaS, APIs
SAML Vs OIDC: Key Diffrences
| Feature | SAML | OIDC |
| Release Year | 2002 | 2014 |
| Token Format | XML Assertion | JWT (JSON Web Token) |
| Protocol Base | Customer SAML Protocol | Built in OAuth 2.0 |
| Transport | HTTP Redirect | HTTPS Rest |
| Mobile/SPAs | Poor Fit | Excellent Fit |
| Developr Tooling | Limited | Extensive |
| Token Revocation | No Natively Supported | Supported with Refresh Tokens |
| Compliance Visibility | Manual | Easier via JWT Claims |
| Common Usage | Enterprise Login | Saas apps, APIs, Mobile |
Token Format: XML vs JSON
Let’s talk about the actual format of the tokens, because this is where things get real for developers.
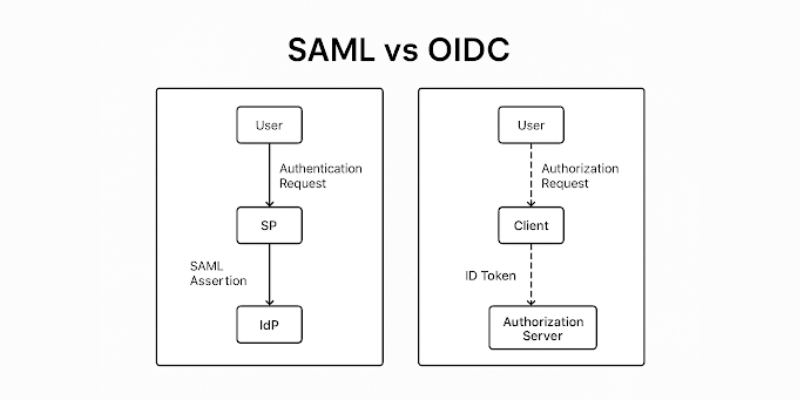
SAML hands you a token wrapped in an XML assertion. It’s bulky, signed with an X.509 certificate, and usually POSTed via browser redirects. If you’ve ever had to dig into a deeply nested XML doc just to figure out why a login failed, you know the pain. Parsing requires dedicated XML libraries, and even then, validating the signature or debugging edge cases can be frustrating and opaque.
On the other hand, OIDC uses JSON Web Tokens (JWTs)—lightweight, Base64-encoded strings that are easy to read, debug, and validate. A JWT is made up of three simple parts: a header, a payload (claims), and a signature. And yes, you can copy-paste one into jwt.io to instantly decode it. That’s a developer superpower during integration and troubleshooting.
But there’s more: JWTs can include custom claims—user roles, permissions, org IDs, whatever your app needs. This reduces the need for repeated API calls to fetch user details, which means faster auth and cleaner code.
In short:
- XML (SAML): Verbose, clunky, needs heavy tooling
- JSON (OIDC): Clean, compact, dev-friendly
Developer Experience: Implementation, Tooling, Community
OIDC is developer-first by design. It uses familiar tools: REST APIs, HTTPS, and JSON. That means you can debug flows using curl, automate tests in Postman, and work comfortably in nearly every modern language—Python, Go, Node.js, Java, etc. Frameworks like NextAuth.js, Spring Security, and Firebase Auth offer drop-in support. It’s fast to build and faster to troubleshoot.
SAML, on the other hand, feels dated. You’ll often deal with XML configs, SAML toolkits that haven’t been updated in years, and cryptic browser POSTs that are difficult to log and debug. Error messages can be vague. Vendor-specific SAML quirks (e.g., Azure vs Okta vs ADFS) further complicate setup. If you’re stuck implementing SAML, our SAML implementation in PHP guide might help.
Key developer frustrations with SAML:
- Harder to trace login failures
- Poor browser debugging tools
- Config errors often result in generic 500s or silent redirects
Why this matters: In fast-moving teams, dev velocity matters. OIDC lets your developers ship features without becoming identity experts.
Security Models and Vulnerabilities
Both protocols can be secure, but the risk surface, strengths, weaknesses, and implementation complexity differ.
SAML Strengths:
- Mature and battle-tested in enterprise settings
- Widely supported in legacy identity platforms (ADFS, Shibboleth, etc.)
- Supports signed and encrypted assertions
- Better suited for complex enterprise federation use cases
SAML Vulnerabilities:
- XML signature wrapping attacks
- Assertion spoofing
- Replay attacks when assertions lack a tight expiration
- Reliance on XML canonicalization—subtle errors break verification
SAML Security Best Practices:
- Always use short-lived assertions with timestamps
- Enable audience restriction and recipient checks
- Use XML canonicalization libraries vetted for security
- Validate signatures at the service provider (SP) end
OIDC Strengths:
- Short-lived, signed ID tokens (JWT)
- Refresh tokens with rotation support
- Uses nonce and state to prevent CSRF and replay attacks
- Native support for asymmetric signing (e.g., RS256)
- Better suited for APIs, SPAs, mobile, and modern cloud environments
OIDC Vulnerabilities:
- Potential token leakage if stored improperly (e.g., localStorage in SPAs)
- Misconfiguration of redirect URIs can lead to authorization code interception
- If nonce/state are not validated, CSRF attacks become possible
OIDC Security Best Practices:
- Always validate iss, aud, exp, and sub in the ID token
- Enforce HTTPS for all token flows
- Rotate signing keys periodically
- Implement refresh token revocation logic and storage protection
SAML is powerful but unforgiving—secure implementations require great care. OIDC, benefiting from modern protocol lessons, is easier to use securely by default, but still requires careful handling. OIDC often pairs well with SCIM for user provisioning—here’s how SCIM works for modern identity provisioning.
Mobile & SPA Compatibility
SAML was never designed for mobile or SPA-based architectures. Its dependence on full-page redirects and form POSTs makes it a pain to embed into modern frontend stacks. Native mobile apps have no concept of a browser redirect, and SAML flows often require custom browser control hacks or workarounds that break user experience.
OIDC, however, is built for distributed, app-centric environments. It supports the Authorization Code Flow with PKCE, which works securely in SPAs and mobile contexts.
Real-world use cases:
- React/Vue SPA: Auth code flow with PKCE + short-lived tokens
- iOS/Android: System browser + OIDC SDK (AppAuth, Firebase, etc.)
- Electron/Desktop: Secure embedded browser + native token storage
If you’re targeting anything beyond traditional web apps, OIDC will save your team hours of duct tape integration
Migration: Moving from SAML to OIDC
You don’t have to pick one. Hybrid setups are common and often necessary in enterprise-grade SaaS.
1. Typical Enterprise Scenario
- Legacy customers mandate SAML for compliance
- Newer services (mobile apps, APIs) are designed for OIDC
2. Migration Strategy
- Continue SAML for existing enterprise contracts
- Introduce OIDC endpoints in parallel for newer apps
- Use a reverse proxy or token gateway to convert SAML assertions into OIDC JWTs
3. Real-World Scenario
Imagine you’re building a multi-tenant SaaS platform:
- Your enterprise clients (Fortune 500, government orgs) mandate SAML because it’s already embedded in their infrastructure.
- Your internal tools, mobile app, and public API all benefit from OIDC’s flexibility, JWT format, and modern SDK support.
So what do you do?
Best Practices for Incremental Migration
- Support both protocols in parallel: Let the identity provider (IdP) or tenant dictate the protocol. Offer SAML for legacy clients, and OIDC for new ones.
- Introduce OIDC in new services: Start by using OIDC in newer parts of your platform: mobile apps, APIs, and admin dashboards. It’s easier to build and maintain.
- Use an identity gateway or broker: Tools like Auth0, Keycloak, or custom-built proxies can accept SAML assertions and internally issue OIDC JWTs for downstream services.
- Token Exchange Pattern: Upon successful SAML authentication, generate a JWT token to be consumed by OIDC-aware microservices.
Example:- A user logs in via SAML (Okta)
- Your backend receives the XML assertion
- It generates a signed JWT with equivalent claims
- Your frontend or downstream services consume the JWT
- Log and trace both: During the transition period, add logging and correlation IDs to both flows. Helps with debugging and resolving user identity mismatches.
For hands-on steps and architecture examples, check our enterprise SSO implementation for B2B SaaS.
Developer Tip: Use feature flags to toggle between SAML and OIDC per tenant or environment. This allows a gradual rollout without regression risks.
Regulatory Compliance Mapping
In enterprise environments, regulatory compliance isn’t optional—it’s expected. You need to prove that identities are verified, data is protected, and access is logged. Here’s how SAML and OIDC stack up:
SAML Challenges:
- Token structures (XML assertions) often lack structured, queryable metadata.
- Role/group attributes are included, but often in vendor-specific formats, which complicates reporting.
- Tracking consent, scopes, and session context often requires external systems.
OIDC Advantages:
- JWTs can carry custom claims—like role, scope, location, MFA—in a format that’s easily inspectable and loggable.
- Claims align directly with compliance fields in standards like GDPR, HIPAA, SOC 2, and ISO 27001.
- Built-in token expiration and consent mechanisms match security best practices and privacy mandates.
Practical Example: If your SaaS app needs to demonstrate that a user was logged in with MFA from a specific geo-location, and gave consent to access billing data, JWT claims like:
{
“mfa”: true,
“geo”: “IN”,
“scope”: “billing.read”,
“consent”: true
}
…can be extracted and logged.
This drastically reduces the effort required for audit trails, internal access reviews, and regulatory reporting.
When to Use Each
Use SAML when:
- You need to integrate with legacy enterprise IdPs (ADFS, Shibboleth)
- Your customers demand SAML for contractual or procurement reasons
- You’re deploying into large organizations that mandate SAML due to vendor lock-in
Use OIDC when:
- You’re building a new SaaS product, mobile app, or SPA
- You need API access control along with login (OAuth + Identity)
- You want a cleaner, faster developer experience with modern SDKs
Conclusion
There’s no one-size-fits-all answer to “Which is better: SAML or OIDC?”
It depends on:
- Your user base (legacy enterprise vs modern API clients)
- Your application type (web, mobile, API, B2B portal)
- Your technical resources and roadmap
SAML is great for enterprise SSO compatibility. OIDC is a better fit for modern SaaS, APIs, and developer-first environments. Supporting both is increasingly common. Still wondering about SAML’s longevity? Here’s a detailed take on is SAML still relevant in 2025.
Think of them not as competitors, but as tools. The key is knowing which one to pick for the job at hand.
FAQs
1. Is OIDC replacing SAML?
Not entirely. OIDC is quickly becoming the default for modern apps, but SAML still dominates in traditional enterprise stacks.
2. Can you support both SAML and OIDC in one app?
Yes. Many SaaS platforms offer both. Some allow customers to choose based on their internal systems.
3. Is OIDC more secure than SAML?
OIDC is easier to implement securely by default, but both can be secure if implemented correctly. The devil’s in the details.
4. Do I need OAuth if I’m using OIDC?
OIDC is built on top of OAuth 2.0. You’re using both—OIDC simply adds identity features (like who the user is) to OAuth’s authorization model.
5. Which is better, OIDC or SAML?
It depends. OIDC is better for modern web/mobile apps and APIs. SAML is more widely adopted in legacy enterprise environments. The better one is the one that fits your architecture, customer base, and compliance needs. If you’re also evaluating OAuth for API-level access, our SAML vs OAuth 2.0 comparison for developers breaks it down with real-world use cases and technical clarity.
6. Is SAML a JSON or XML?
SAML uses XML for its assertions. All identity and authentication data is wrapped in digitally signed XML documents.
7. Does OIDC use JSON?
Yes. OIDC uses JWTs (JSON Web Tokens), which are JSON-based and easily parsed in any modern language.
8. Can OIDC be used for SSO?
Absolutely. OIDC is specifically designed to support Single Sign-On in modern applications—especially SPAs, mobile apps, and APIs.
9. Why is XML preferred over JSON?
In older enterprise systems, XML was preferred for its strict schemas, namespace support, and signature specs. But JSON is now more popular due to its simplicity, readability, and ease of integration in modern tech stacks.
.png)



