We’re super excited to finally launch Psylo, a new kind of private web browser for iOS and iPadOS. In Psylo, each tab is its own silo with isolated storage, cookies, and even its own IP address. Psylo introduces advanced anti-tracking and anti-fingerprinting features that go beyond what a VPN can offer, thanks to the deep integration between Psylo and our own Mysk Private Proxy Network. Psylo is backed by years of insights from our privacy research at Mysk. Psylo is available today on the App Store as a monthly or annual subscription with a free 3-day trial.
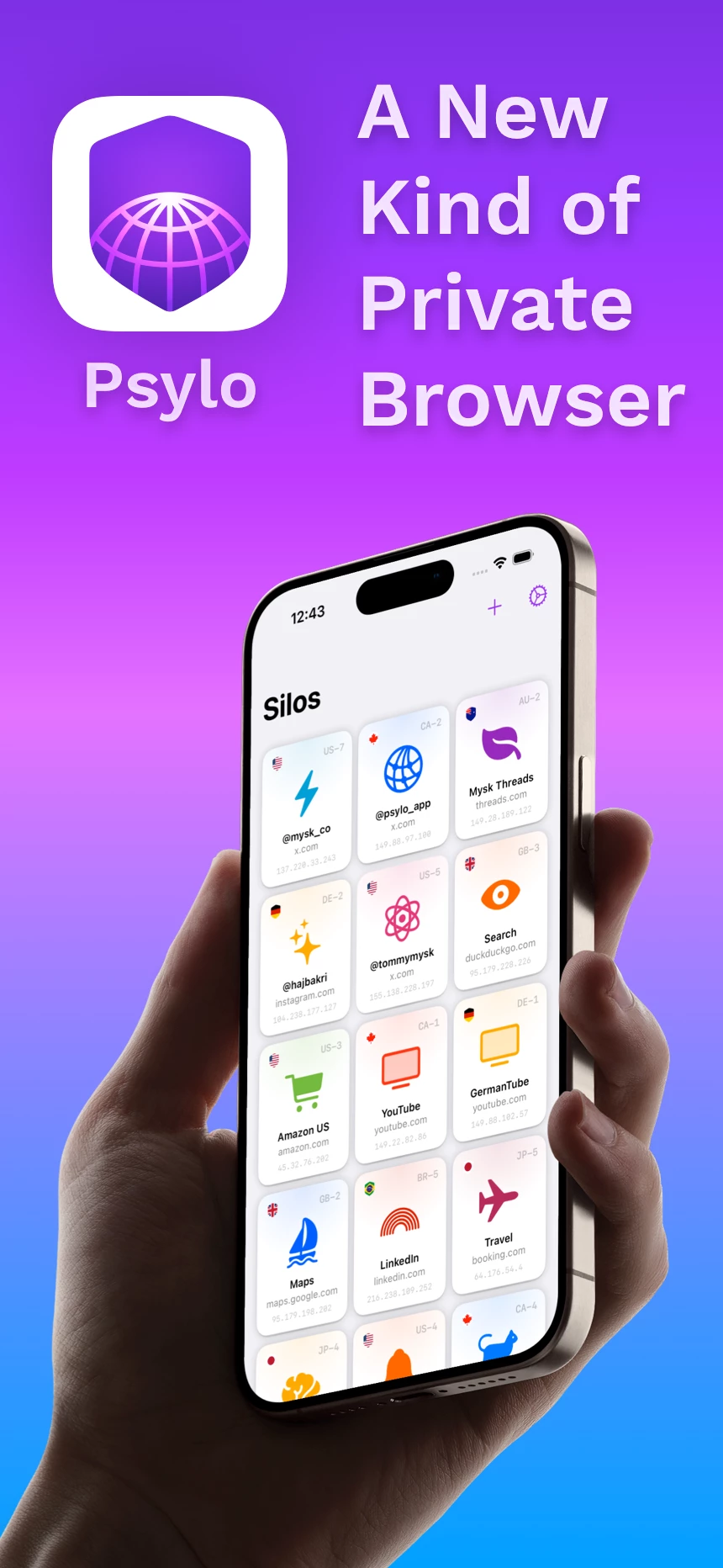 Psylo — A New Kind of Private Browser
Psylo — A New Kind of Private Browser
Why a Web Browser?#
Funny enough, we didn’t initially set out to build a whole web browser.
As occasional privacy researchers, we and many others have noted how native apps utilize extensive tracking SDKs. These SDKs collect all kinds of data to “fingerprint” users, aiming to track them across different apps and even across devices, primarily for targeted advertising. This is not limited to the usual suspects, like free mobile games and social media apps, but also business apps like Microsoft Outlook, which include various advertising and tracking SDKs.
To their credit, Apple has consistently improved privacy measures, notably introducing App Tracking Transparency in iOS 14, App Store Privacy Nutrition Labels, and Privacy Manifests. Their latest efforts even restrict app developers from certain APIs that can potentially be misused for tracking without disclosure. However, despite Apple’s best efforts, companies continue to discover new methods to circumvent these protections, as we previously discussed here.
One common practice to avoid the invasive tracking of native apps is to use web-based versions offered by apps such as X, Instagram, LinkedIn, and others. Web apps inherently have fewer permissions and significantly reduced fingerprinting capabilities compared to their native app counterparts. iOS and iPadOS also conveniently support adding Progressive Web Apps (PWAs) directly to the Home Screen, making them as easy to open as regular native apps.
However, as we will discuss, web browsers themselves aren’t immune to more advanced fingerprinting techniques, even when used alongside VPNs. This is where we saw an opportunity for something new.
Web Silos, or Isolated Web Sessions#
Last October, we started building an app simply focused on creating fully isolated web sessions, tailored specifically for PWAs. Each isolated session (what we call a silo) gets its own dedicated storage, cookies, and cache, fully separate from other silos. On top of that, we built our own proxy network, initially with just 5 servers.
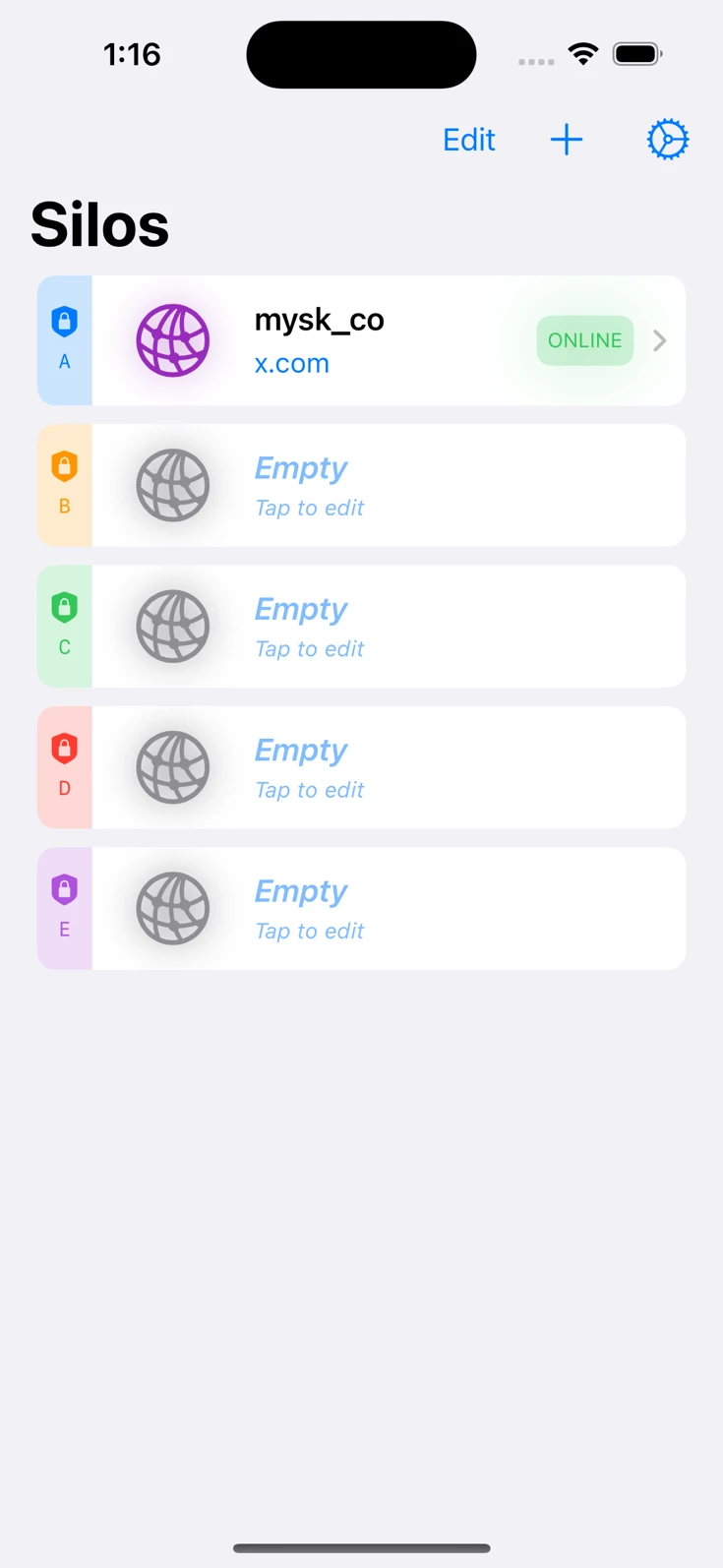 An early version of Psylo
An early version of Psylo
This early app proved quite promising. For instance, you could have a silo for your personal X account through a proxy in Germany, another silo for Instagram via a US proxy, and a separate silo for another account through Canada. These silos are fully isolated, each with separate data storage and even distinct IP addresses, significantly reducing cross-site and cross-session tracking.
That said, we already knew our work was far from over, and addressing fingerprinting required more than simply masking IP addresses.
Fingerprinting: Languages, Timezones, Canvas, and Lots More#
But first, what is fingerprinting?#
Fingerprinting is a technique that attempts to track a user across different apps and websites, without the need have a unique user ID that could be shared across those apps. It works by gathering subtle signals and characteristics about the user’s device, such as phone model, system language, timezone, IP address, and even graphics rendering quirks (known as canvas fingerprinting). More advanced techniques even consider factors like average scroll speed and mouse movement patterns.
As a simple example, consider this basic set of characteristics collected by Website A from an unknown user:
- Phone Model: iPhone 14 Pro Max
- Operating System Version: iOS 18.4.1
- System Locale: English (Canada)
- System Timezone: Europe/Madrid
- IP Address: 79.127.215.215
- IP Address Country: Paris, France (through a VPN)
- Browser Window Size: 405x865
Here we have a user who uses an iPhone 14 Pro Max, running iOS 18.4.1, from Canada, currently in Spain, their IP address is in Paris, and their browser window has a size of 405x865 pixels. That exact combination of characteristics would constitute a fingerprint, and Website A can share it with Website B. Later, when a user who happens to have those same fingerprint characteristics (i.e. iPhone 14 Pro Max, from Canada, in Spain, etc.) visits Website B, it can make a good guess that it’s the same user who visited Website A earlier.
Now let’s say that same user switched to a different VPN server in Denmark. With all other factors remaining unchanged, it would still be a fairly good guess that it’s the same user. The likelihood of another user sharing those exact same combination of characteristics (i.e. same phone model, OS, language, timezone, browser window size, etc) is low.
As this is a simple fingerprinting example with only 7 factors, the resulting fingerprint is “fuzzy” and guesses about the user’s identity may not be reliable. Actual fingerprinting techniques include dozens of factors, with each added factor making the fingerprint “sharper,” thus more likely to reliably identify a user.
The goal of any anti-fingerprinting system is to make the user’s fingerprint as fuzzy as possible, making it more difficult to accurately track them.
Now for a real example#
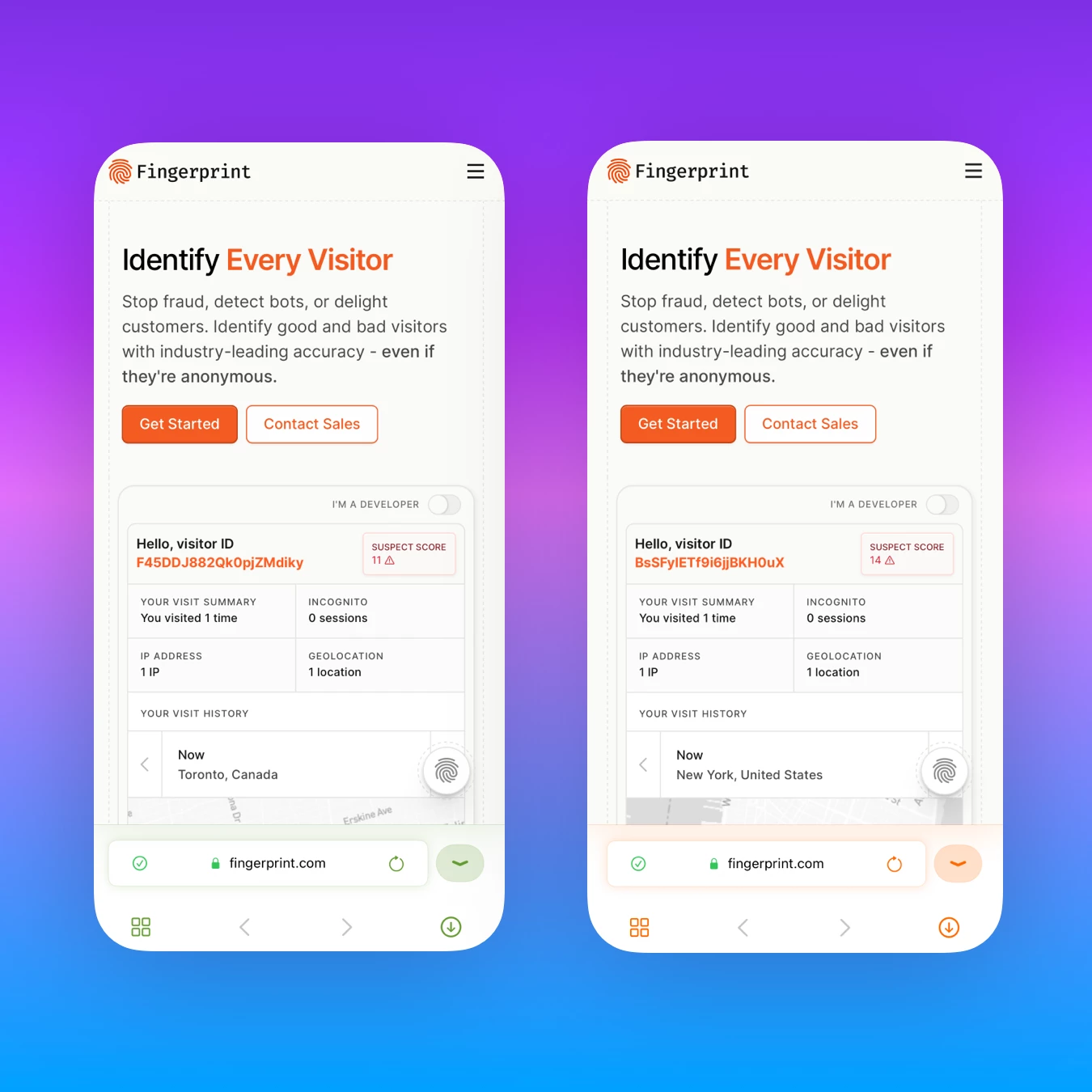
For a real example of fingerprinting, let’s look at Fingerprint, which offers fingerprinting as a service to other websites and apps, with the stated goal to “Identify Every Visitor” to “Stop fraud, detect bots, or delight customers.”
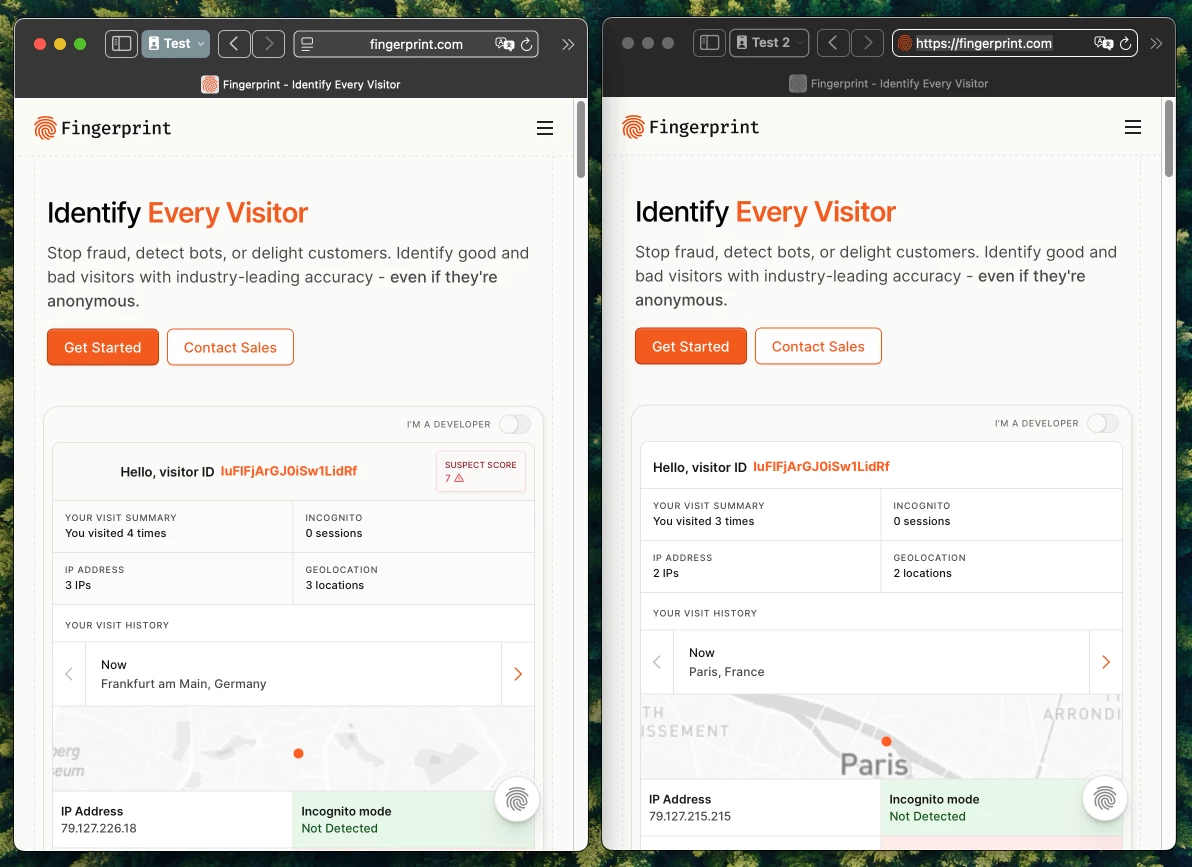 Fingerprint successfully generated the same visitor ID for 2 distinct Safari 18.4 profiles
Fingerprint successfully generated the same visitor ID for 2 distinct Safari 18.4 profiles
We tested out their service by simply visiting their homepage, which displays our unique fingerprint, using Safari 18.4 for Mac. For this test, we created 2 new browsing profiles ensuring they don’t share any cookies or data and visited https://fingerprint.com from 2 separate IPs via VPN. Despite our attempt to cover our tracks, Fingerprint successfully generated the same visitor ID for both windows.
Beyond a VPN#
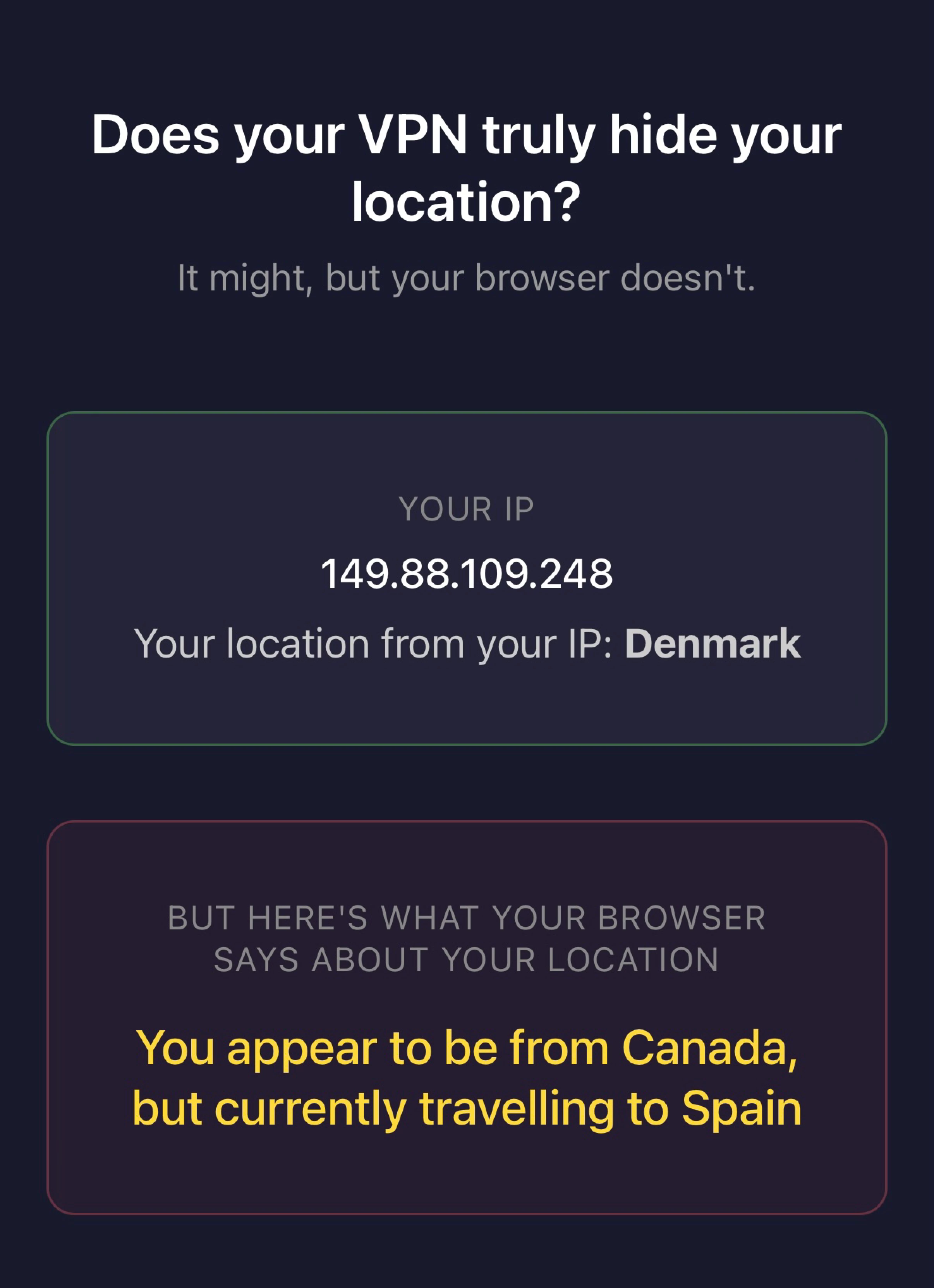 Despite using a VPN through Denmark, a website can still infer your country and where you might be traveling based on timezone
Despite using a VPN through Denmark, a website can still infer your country and where you might be traveling based on timezone
VPNs alone can’t quite counteract fingerprinting, since all they can do is mask your IP and potentially block known tracking scripts and domains. To see this for yourself, we made this proof-of-concept web page that relies on simple JavaScript calls to infer your country, potentially revealing if you’re traveling to another country via your system’s timezone settings, even if connected via VPN.
This is one place where Psylo really shines. Not only does every silo get a unique IP address through our proxy network, but it also matches the locale and timezone of its associated proxy server. For example, if a silo connects through a German proxy, it automatically adjusts the browser’s language and timezone accordingly, making those fingerprint factors similar to actual users from Germany, thus making your fingerprint fuzzier.
Psylo also includes more common anti-fingerprinting measures, such as canvas randomization, typically only found in desktop versions of privacy-focused browsers such as Brave, but not on iOS. This is due to Apple limiting apps to use the system-provided WKWebView. We were able to achieve this through a client-side JavaScript solution, which powers many of our anti-fingerprinting measures.
 Pyslo can successfully evade the advanced fingerprinting techniques used by Fingerprint. (Test performed on the same iPhone using Psylo 1.0.0 in June 2025)
Pyslo can successfully evade the advanced fingerprinting techniques used by Fingerprint. (Test performed on the same iPhone using Psylo 1.0.0 in June 2025)
Early Beta, and Realizing We’re Building a Browser#
We seeded the first beta of Psylo in February. That version of Psylo was far more limited compared to the version we’re releasing today: Only 5 generic proxies (which didn’t specify a country), a rudimentary browser user interface (it wasn’t supposed to be a browser, after all), and most importantly it was missing the Default Browser Entitlement that Apple selectively grants to developers of browser apps. Despite its name, this entitlement not only grants browser apps the ability to become the user’s default browser of choice. It also provides all-important browser features, such as password manager integration, passkeys, Service Workers, and even better performance.
Even then, the initial reaction we got to Psylo was encouraging, but we struggled to convey what we thought Psylo should be: It wasn’t a browser, it was intended for using PWAs through our private proxy network. As silly and obvious as it sounds now, we were actually building a browser but didn’t quite want to admit it yet…
So now that we’ve committed to building a browser, the first step was to apply to Apple for Default Browser Entitlement. Not knowing what to expect, we filled this form and sent it off to Apple. Luckily, 3 weeks later we got this email from Apple granting us the Default Browser Entitlement.
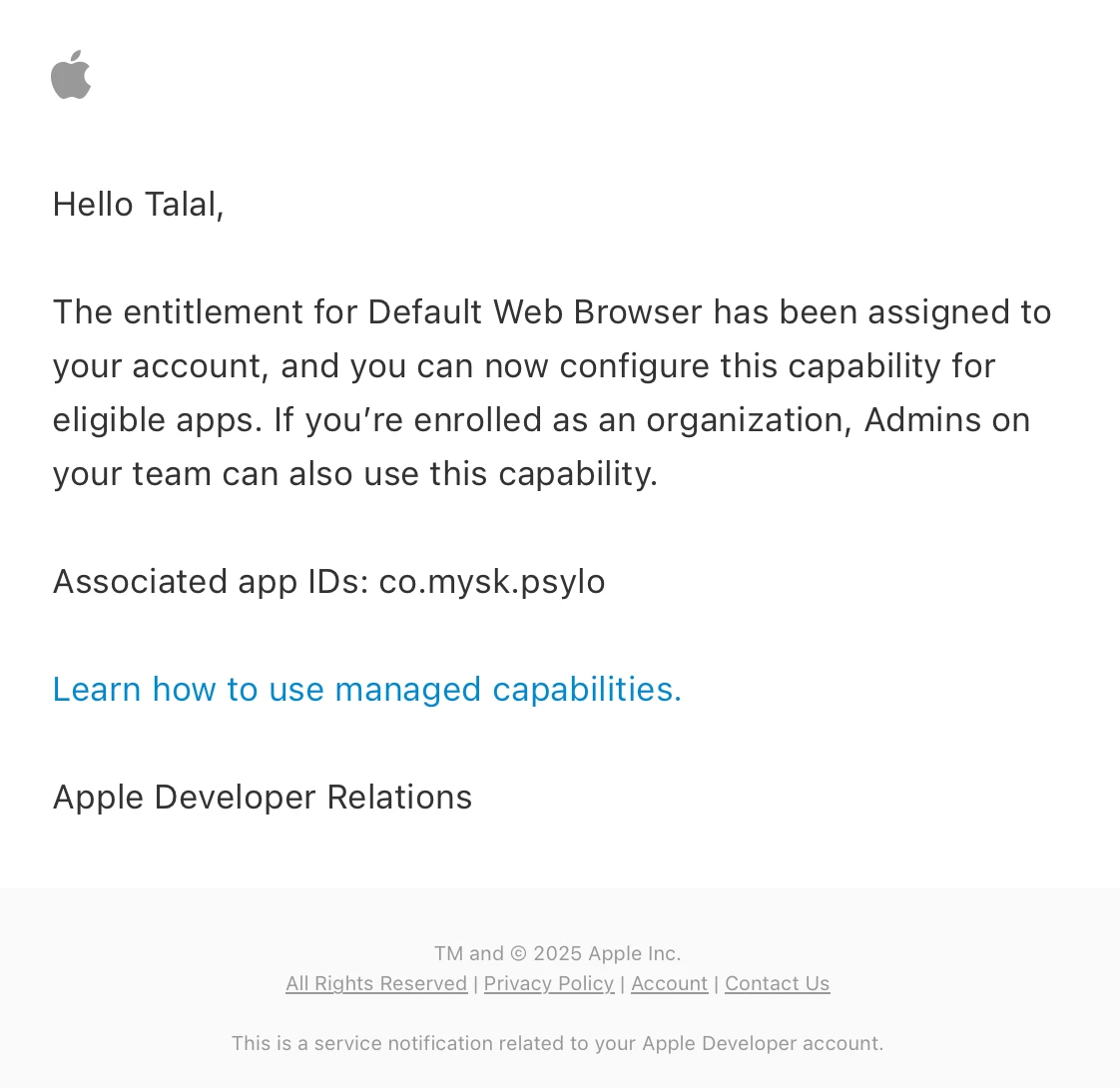 We're a browser vendor now!
We're a browser vendor now!
Mysk Private Proxy Network#
We’ve gotten this far into the post without discussing a major component of Psylo: our scalable global network of no-log proxy servers, which we call the Mysk Private Proxy Network. Currently consisting of 40+ proxy servers worldwide, it’s designed to scale as we grow our service. Psylo seamlessly integrates with Mysk Private Proxy Network, allowing per-silo proxy connections.
From the outset, we established the following primary design requirements for our proxy network:
-
Our Software: The system must operate exclusively on software that we either developed ourselves or maintain complete control over. This requirement is essential not only to meet the other criteria listed below but also to ensure we’re fully aware of any limitations within our system.
-
No Logs: The system must never log or otherwise store any personally identifiable information or browsing data, including but not limited to IP addresses, DNS requests, and any other data that could potentially identify a user.
-
No User Accounts: The system must be accessible without requiring users to create an account—in fact, the system must have no notion of user accounts whatsoever. The only information the system should recognize is whether a connection to the proxy network is associated with an active subscription. Subscription tracking must rely exclusively on randomized identifiers.
-
Bandwidth Tracking and Abuse Prevention: The system must track bandwidth usage for each subscription to prevent abuse and maintain quality of service for all subscribers. It must also have the capability to block subscriptions deemed abusive from accessing the network.
We believe we’ve successfully implemented all of the above requirements in the initial rollout of the Mysk Private Proxy Network, with the most challenging being requirements (3) and (4).
We absolutely did not want to force users to create and manage accounts with us (unlike some other browsers, which may no longer exist), nor did we even want user accounts as an option. Our primary concern is simply verifying whether an anonymous user accessing the proxy network holds an active subscription.
Since Psylo is an iOS and iPadOS app, the default method for offering subscriptions is through In-App Subscriptions. Again, to Apple’s credit, when users make a purchase through the App Store’s In-App Subscription system, developers never receive any personally identifiable information associated with those purchases. This fits nicely with requirement (3), allowing Psylo users to subscribe without creating an account or revealing their identity to us. It also opens the door for potentially offering alternative payment methods in the future.
Regarding requirement (4), it was essential for us to ensure the proxy network could be maintained and scaled effectively as our user base grows. To achieve this, we built our own monitoring system. However, our primary concern remained preventing abuse of the proxy network. For this initial rollout, we decided to err on the side of caution and set bandwidth limits at 50 GB per month per user. In the coming months as we gain a better understanding of how the system performs in production, we’ll happily consider increasing these bandwidth limits for all our users.
Details, Details, Details#
There are so many further technical details about Psylo and the Mysk Private Proxy Network that we’d love to explore further: such as how we handle proxy authentication, strange and unexpected quirks of WKWebView, challenges with Cloudflare, SwiftUI shenanigans, issues with different cloud providers, the weird and possibly shady world of proxy providers, securing our Swift-based application server, remote app configuration, localization, and much more. We’ve gained a tremendous amount of knowledge during the nine months we spent developing Psylo and plan to share more insights over the coming months.
What’s Next?#
Releasing version 1.0.0 of a new product is always nerve-racking, especially for an app like Psylo, with so many moving parts. So many thoughts cross our minds: How will it be received? Did we miss something so glaringly obvious in our system design? What if the system crashes and doesn’t hold up under load?
We are also very aware of how many features Psylo 1.0.0 still lacks and how much better it can become. However, we’ve reached a point where we believe this initial release is compelling enough to share with the world.
The most frequent request during our beta period was an Android version. While it’s too early to commit, an Android version will surely be on the table if the iOS version proves successful.
We really look forward to your hearing your thoughts and feedback. Psylo is available today for iOS and iPadOS through monthly or annual subscriptions, with a free 3-day trial offering full access to all features. Use the discount code PSYLOPARTY for 30% off your annual subscription.
For any comments, feedback, or support requests, you can reach us via our social media accounts:
First, we would like to extend our heartfelt thanks to all of our followers on X, Mastodon, and Bluesky. Special thanks goes out to our beta testers, whose valuable feedback significantly helped shape Psylo. If you participated in our beta testing and would like a special discount, please contact us through any of our social media channels.
During development, we found BrowserLeaks immensely useful for testing our anti-fingerprinting measures.
.png)





