CISOs’ Challenges
Ray Security Addresses
Who
Who has access to data, and should they have access?
Where
Where is the sensitive data, and is it even in use?
How
How can we deny access to data from attackers?
Ray Security’s Predictive Platform Reduces Data Risk by Over 90%.
Reduce Risk, Save Time, Simplify Operations.
Shrink Your Attack Surface
Automatically identify unused or low-priority data so resources are not wasted on what no one touches.
Prevent Breaches Before They Happen
Predict which data is likely to be accessed and apply controls before attackers get near it.
Adapt to Real Usage in Real Time
Dynamically adjust access and protection based on how users interact with data, not just static rules.
Cut Operations Complexity
Eliminate unnecessary policies, permissions, and infrastructure tied to inactive data.
Explore Ray Security’s Platform
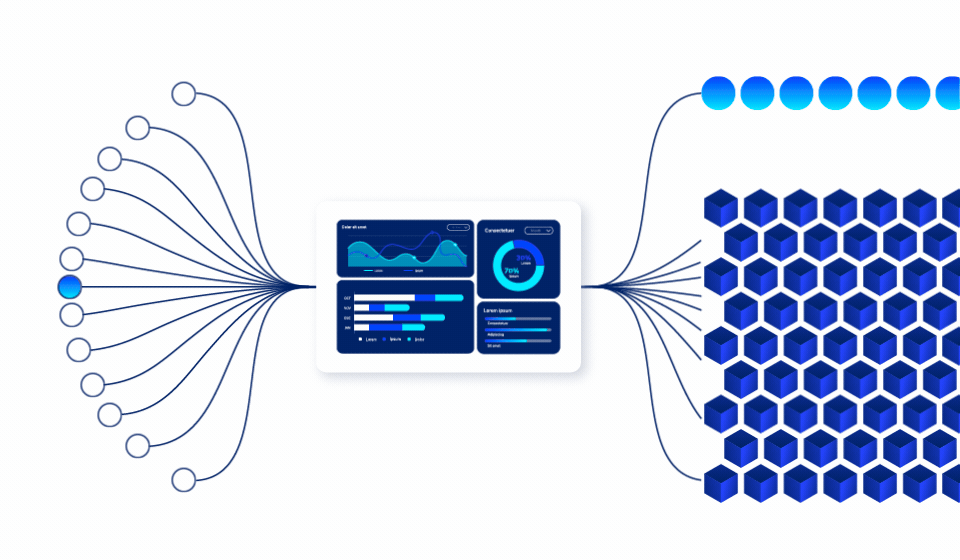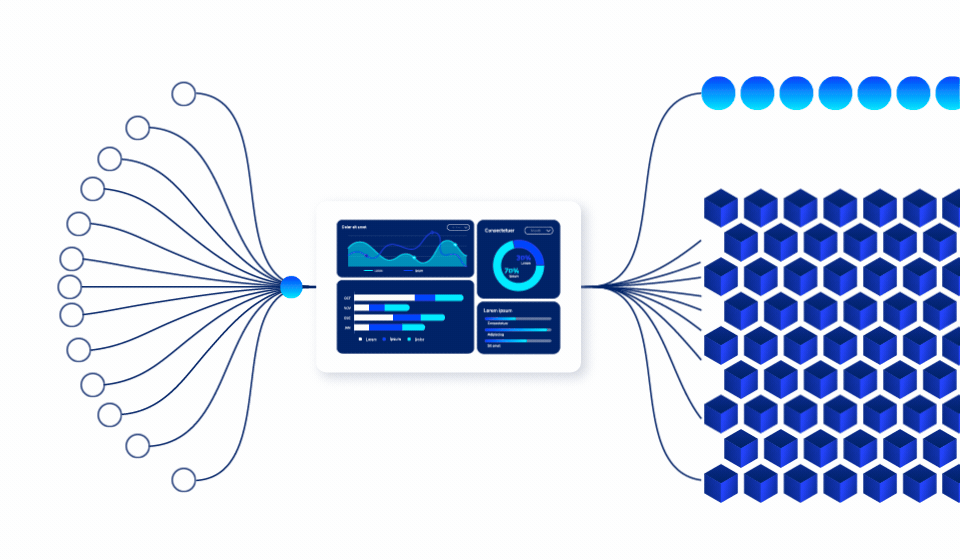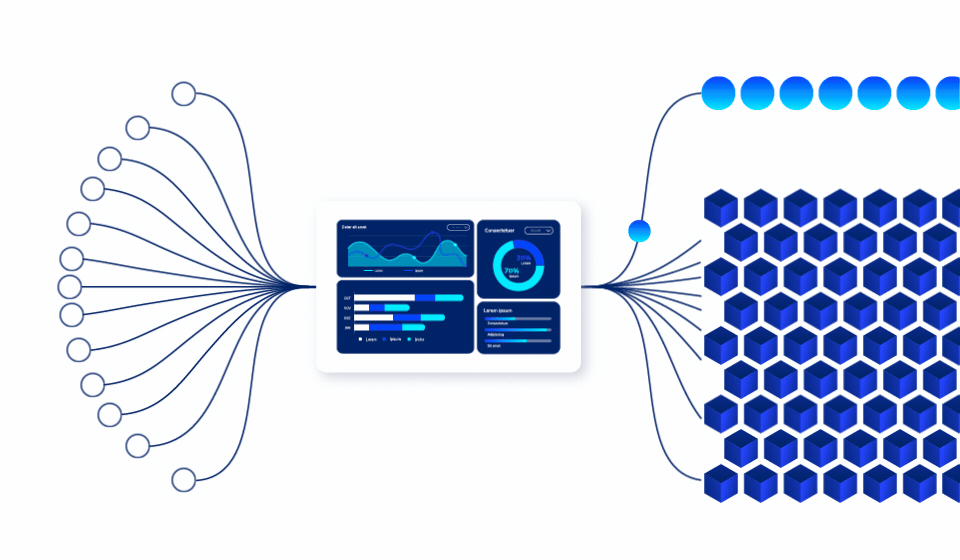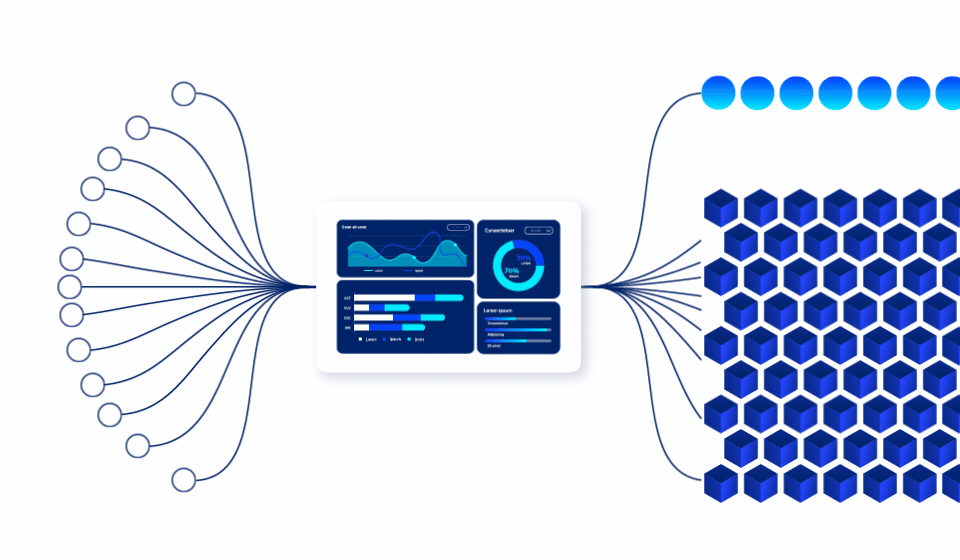
Predictive Data
Usage Engine
See Into Your Data Future
Our proprietary predictive engine continuously analyzes access patterns, data behavior, and business cycles to identify which data will be used.
Dynamic Protection
Implementation
From Prediction to Protection
Automatically implement different protection strategies based on predicted usage patterns. Make unused data immune to attacks, while delivering real-time detection and response for the data in use
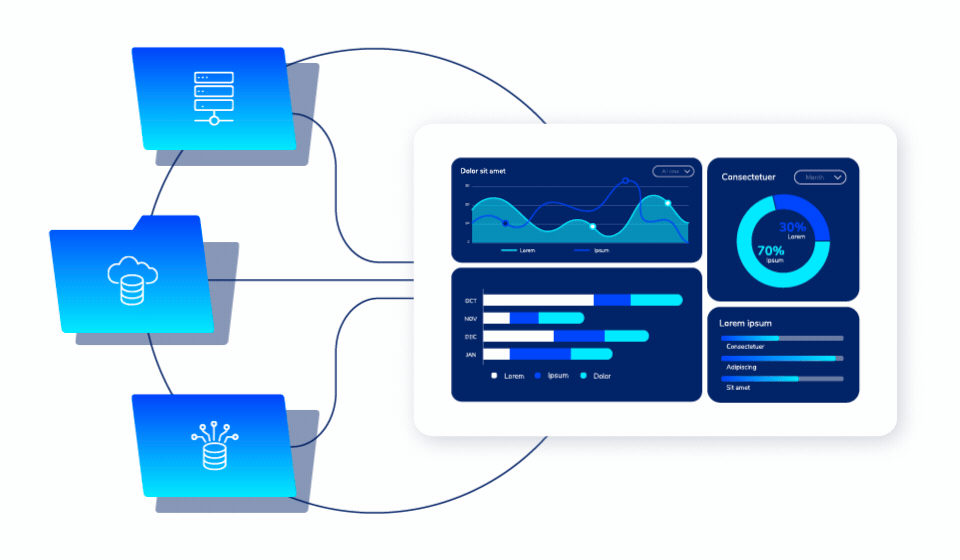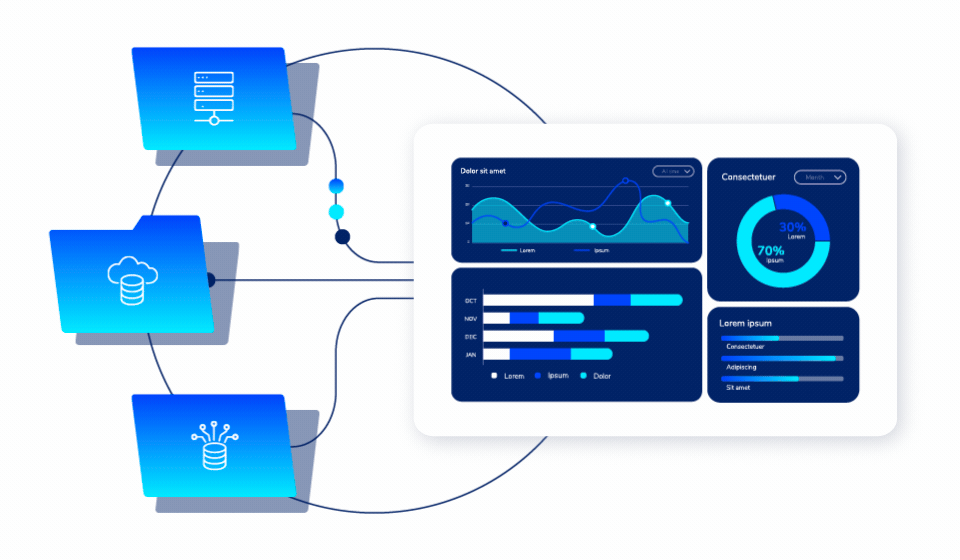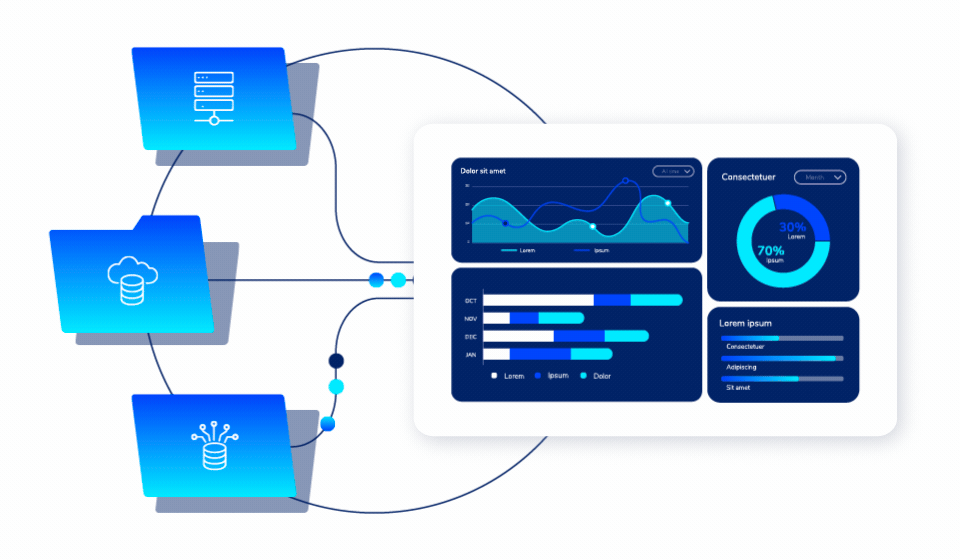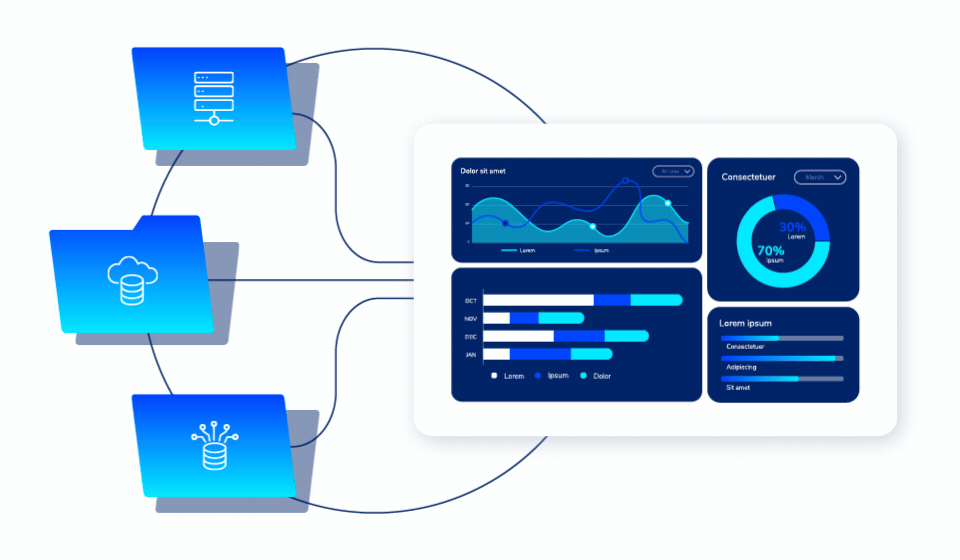
Unified Policy Management
One Platform. All Environments.
Apply security policies across cloud and on-premises environments through a single console. No more managing multiple disconnected tools or inconsistent protection strategies.
Use Cases
Comply with regulation and ensure least privilege access to data. Map who can access data versus who actually does. Remove unused or excessive rights to improve security. Enforce Just Enough Access (JEA).
AI Data Access Governance
Control the data accessed by LLMs like Copilot, ChatGPT Enterprise and Glean. Manage agentic AI access and prevent AI from revealing sensitive information. Maintain data lineage across all AI interactions.
Prioritize and reduce blast radius: cut data exposure by 90% with predictive protection. Focus on critical data for faster, broader, and more precise security (secure-by-default), even for partially unclassified data.
Next-Gen Data Loss Prevention (DLP)
Protect data as it moves with unmatched visibility while extending the timeline to not only the past, but also the future. Ensure access justification, privacy, and confidentiality, and prevent unauthorized, uncontrolled, and unaudited data use.
Comply with regulation and ensure least privilege access to data. Map who can access data versus who actually does. Remove unused or excessive rights to improve security. Enforce Just Enough Access (JEA).
AI Data Access Governance
Control the data accessed by LLMs like Copilot, ChatGPT Enterprise and Glean. Manage agentic AI access and prevent AI from revealing sensitive information. Maintain data lineage across all AI interactions.
Prioritize and reduce blast radius: cut data exposure by 90% with predictive protection. Focus on critical data for faster, broader, and more precise security (secure-by-default), even for partially unclassified data.
Next-Gen Data Loss Prevention (DLP)
Protect data as it moves with unmatched visibility while extending the timeline to not only the past, but also the future. Ensure access justification, privacy, and confidentiality, and prevent unauthorized, uncontrolled, and unaudited data use.
"We required a solution that could seamlessly integrate robust data security with intelligent data management capabilities. Ray Security delivered on both fronts. They quickly understood our challenges and engineered an effective solution for data movement, significantly reducing our storage costs. The integration process was swift, their team’s support was and continues to be exceptional."
Erik Hart
CISO, Cushman & Wakefield
"Ray Security brings a new dimension to enterprise data protection by leveraging artificial intelligence to predict, respond, and adapt to threats before they manifest. Its differentiator is the seamless blend of real-time insight with contextual, risk-based access controls, dramatically reducing the attack surface while empowering organizations to operate with confidence.”
Ashif Samnani
Principal Cybersecurity Lead, MOBIA

"Ray Security addresses a blind spot we’ve seen in every enterprise: the gap between how data is actually used and how it’s protected. Their approach reduces exposure without slowing the business down, which is exactly what our customers need."

"At Compuquip, our job is to turn technology into outcomes. Ray Security is the first platform that actually delivers on the predictive promise and lets us prove risk reduction by focusing on data that will be used, not just stored."
Ricardo Panez
President, Compuquip
"Ray Security looks at data differently. Instead of treating everything the same, it predicts usage patterns so enterprises can secure used and unused data in smarter ways. That distinction has been a game-changer in our conversations with customers."


10 Cool New Data Security Products In 2025
Even in an area of cybersecurity as essential as data protection, the stakes continue to climb higher in 2025. The pressures have mounted both from the intensification of data theft and extortion attacks as well as from the surging adoption of GenAI-powered tools and LLMs, which have drastically heightened the risk of sensitive data being improperly accessed.

Less Is More: The Power of Just Enough Access (JEA)
Less Is More: The Power of Just Enough Access (JEA) When Sarah moved from the finance team to marketing three years ago, no one thought to revoke her access to the company’s financial database. She was a trusted employee and it didn’t feel urgent. Last month, Sarah’s credentials were compromised in a phishing attack. […]

Ray Security Takes an Active Data Security Approach
Evolving technology and advanced attackers have created new data security concerns for enterprises. There’s more data available than ever, particularly thanks to artificial intelligence (AI) and more interconnected devices. And attackers have noticed.
.png)



