As a security engineer and bug bounty hunter, I’ve spent countless hours with Burp Suite. It’s an incredible tool, comprehensive, powerful, and packed with features. But here’s the thing: sometimes it’s just too much.
You know the drill. You’re casually browsing a web app, you spot something interesting, and you think, “Let me just replay that request and tweak a few parameters.” But then you remember: you need to fire up Burp, configure your proxy settings, install CA certificates (if you haven’t already), route your browser traffic through it, and then you can start testing. By the time you’re set up, you’ve lost your flow.
For quick, ad-hoc testing, especially when you’re already in your browser, Burp feels like bringing a sledgehammer to crack a nut.
That’s why I built rep+.
The Problem: Burp Suite is Heavy for Quick Tasks
Don’t get me wrong, I love Burp Suite. For deep penetration testing, complex workflows, and collaborative projects, it’s unbeatable. But for those moments when you just want to:
Replay a single request with modified headers
Test a few payloads against a parameter
Quickly encode/decode some data
Capture and inspect API calls without leaving your browser
...Burp feels like overkill. The overhead of launching the application, configuring proxies, and managing certificates adds friction to what should be a 30-second task.
Enter rep+: Burp’s Repeater, Right in Your Browser
rep+ is a Chrome DevTools extension that brings the core functionality of Burp’s Repeater (and a bit of Intruder) directly into your browser. No proxy setup. No certificates. No heavyweight UI. Just open DevTools, switch to the rep+ tab, and start testing.
Key Features
Zero Setup Required
Unlike Burp Suite, rep+ works directly in Chrome . There’s no need to:
Configure system-wide proxy settings
Install CA certificates
Route browser traffic through an external application
Just install the extension, open DevTools (`F12`), and you’re ready to go.
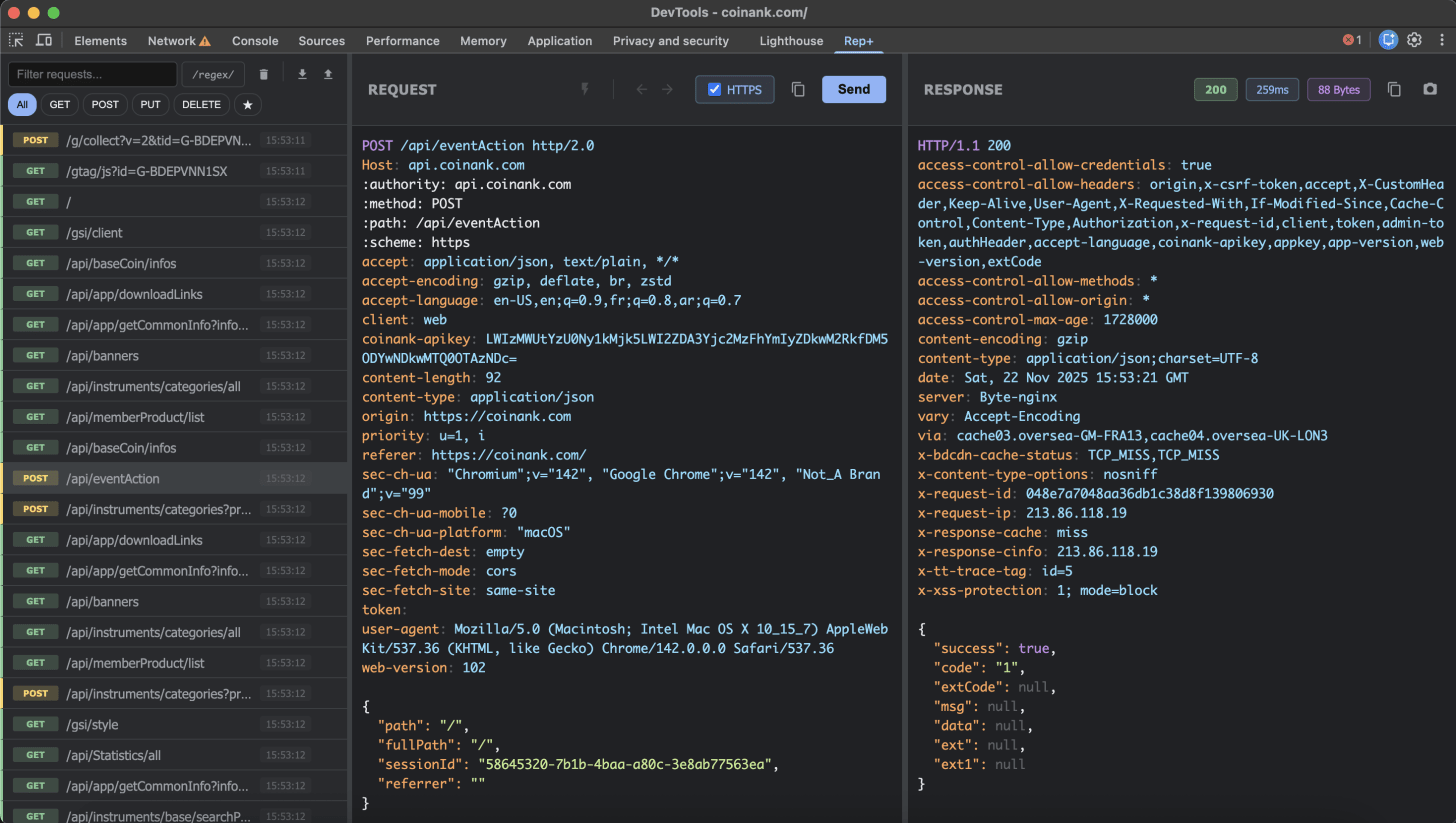
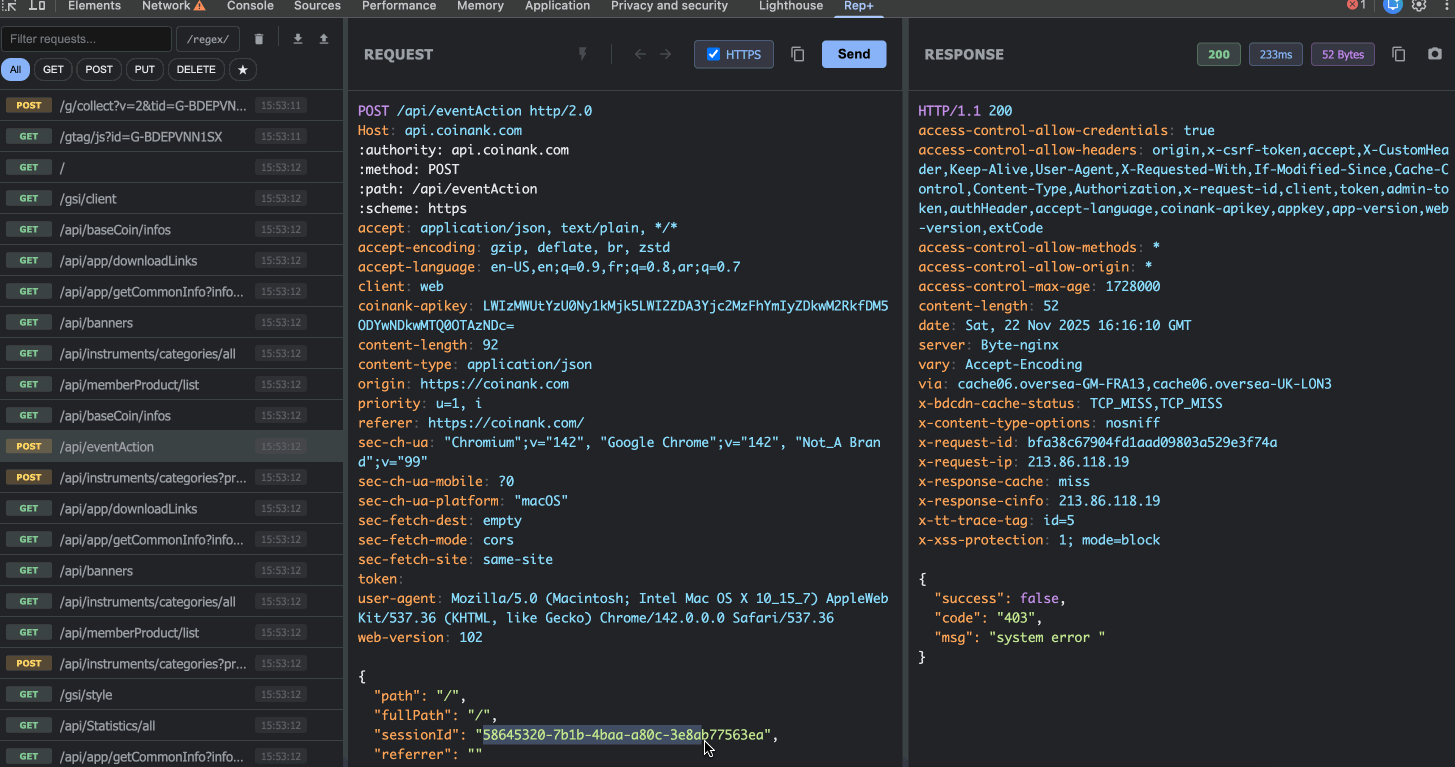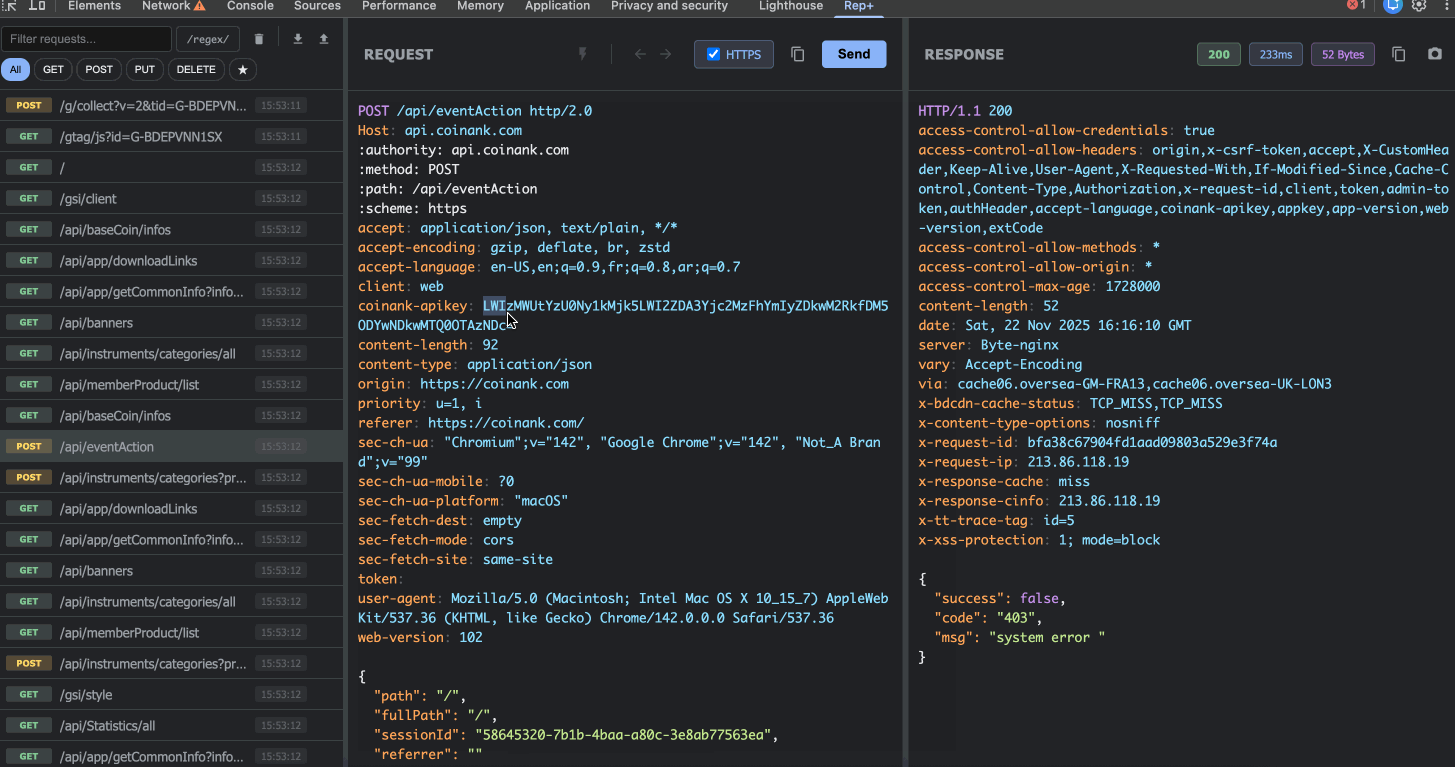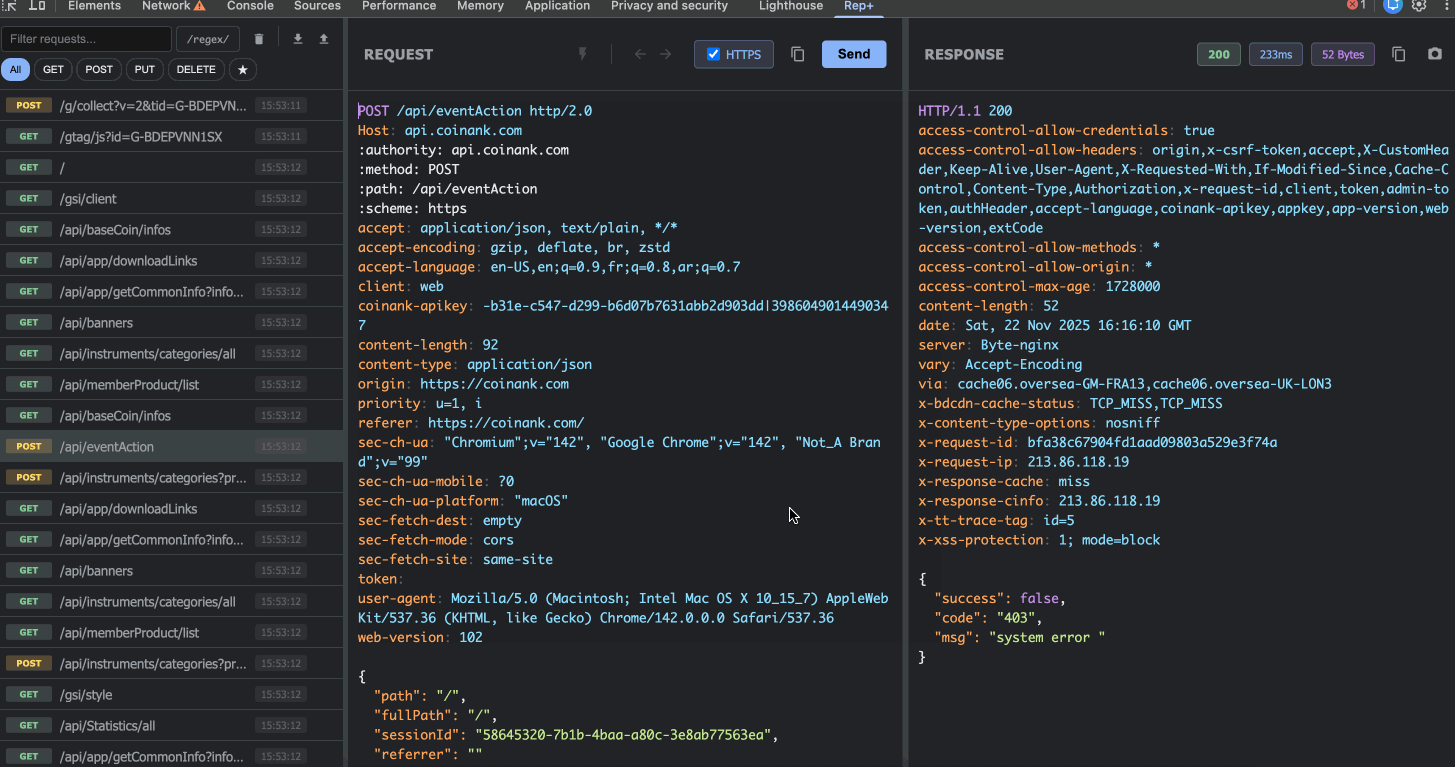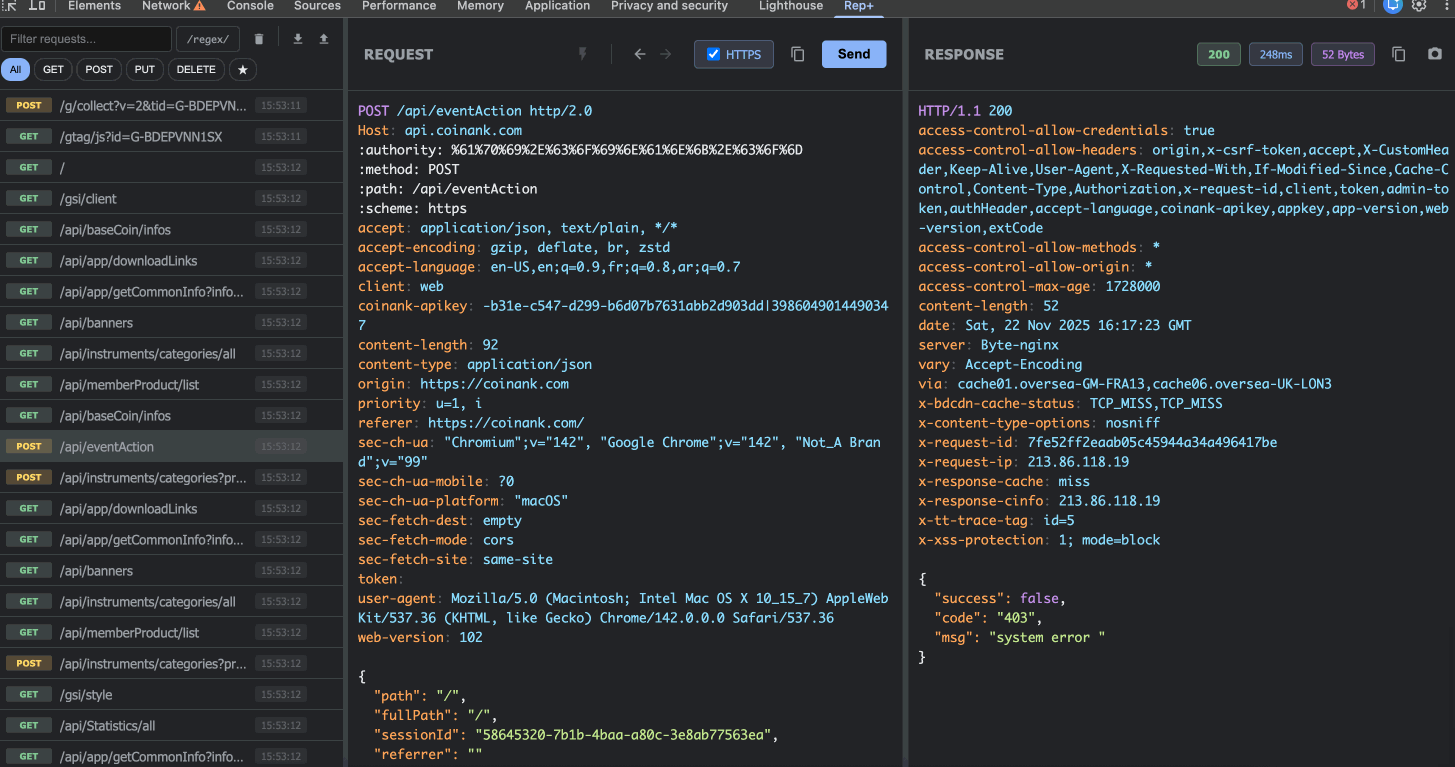
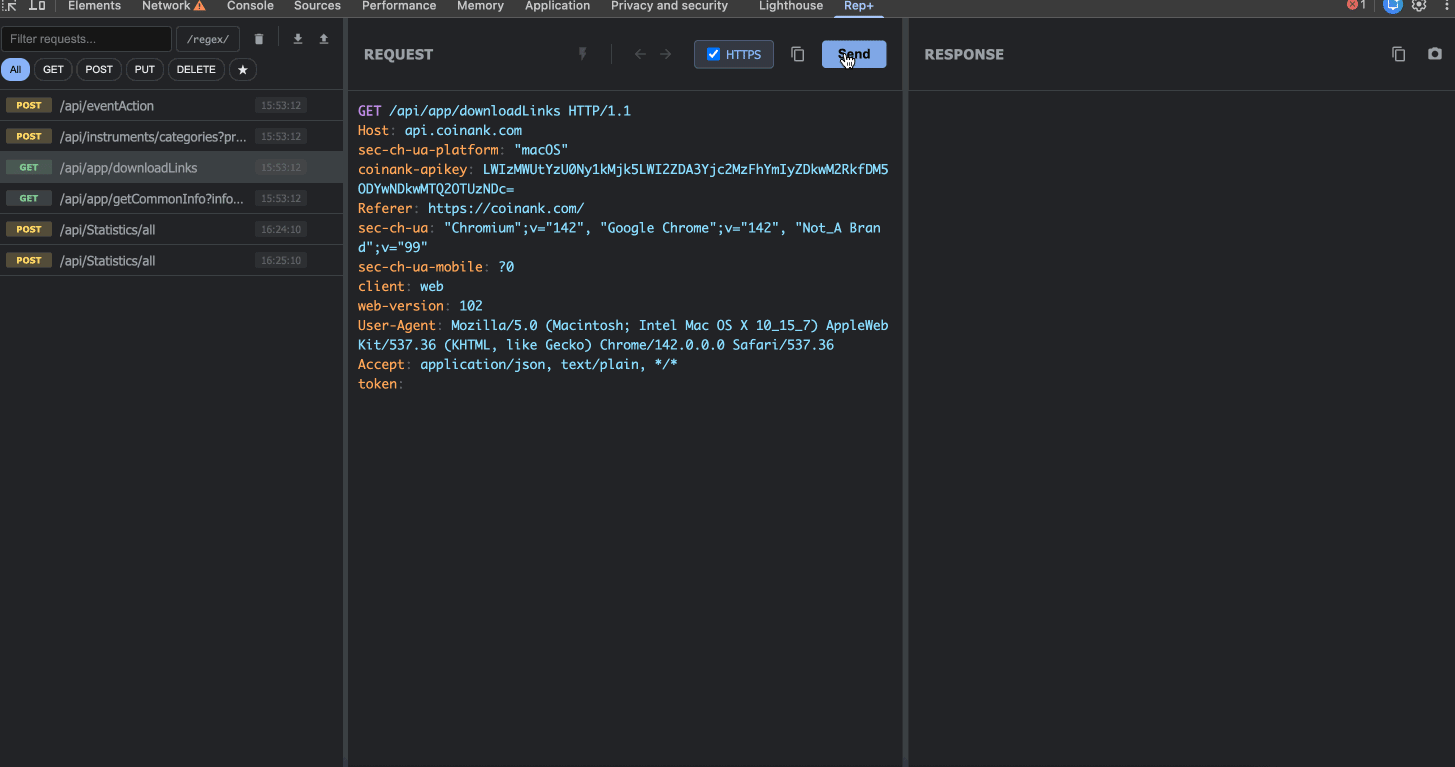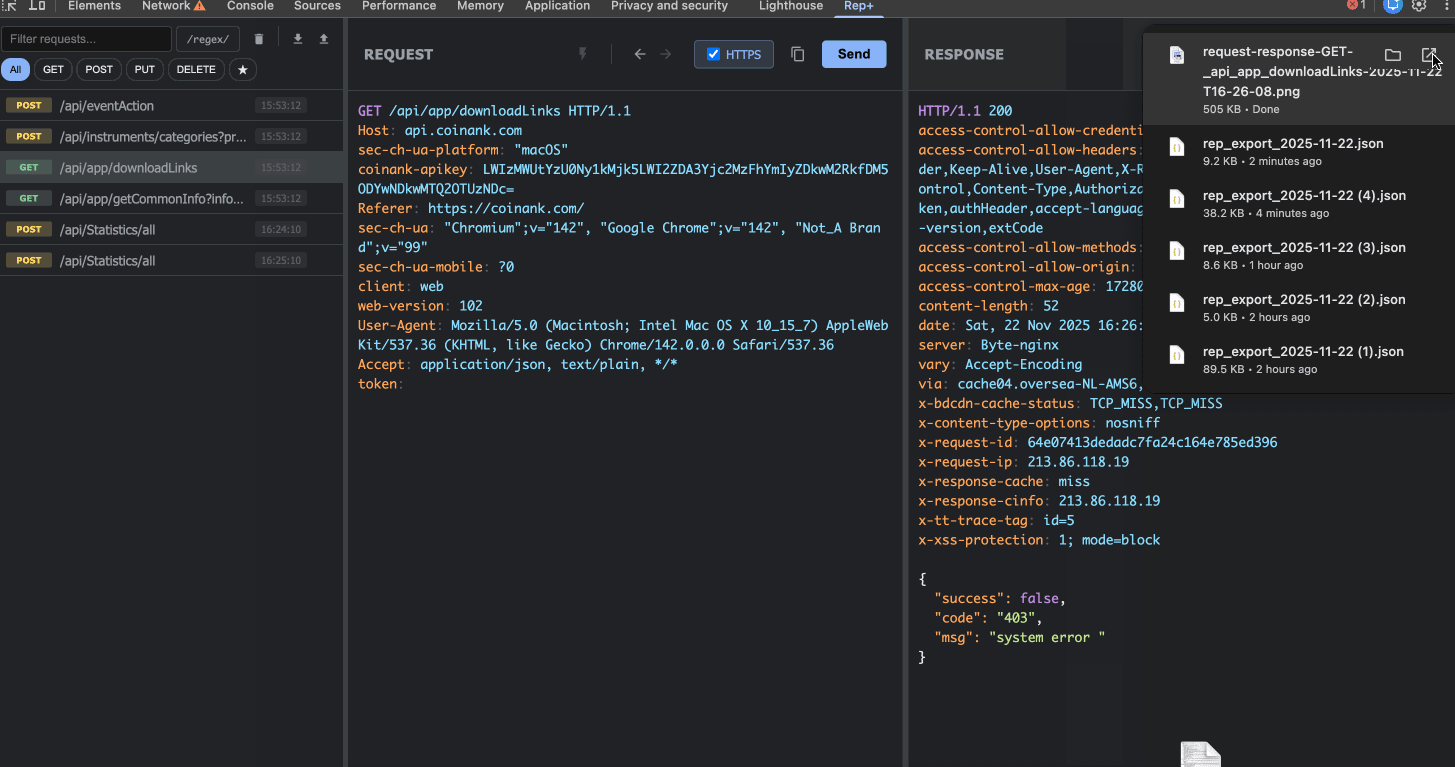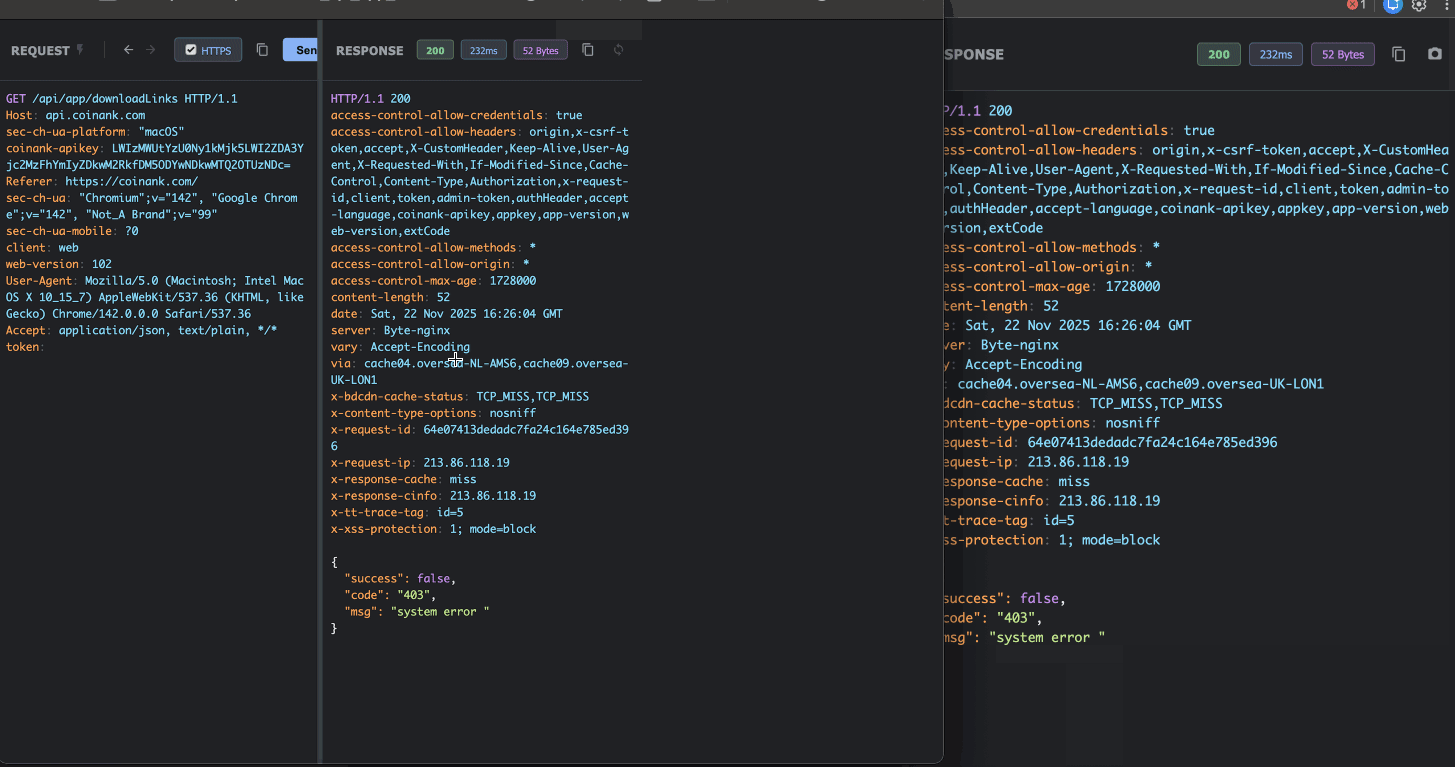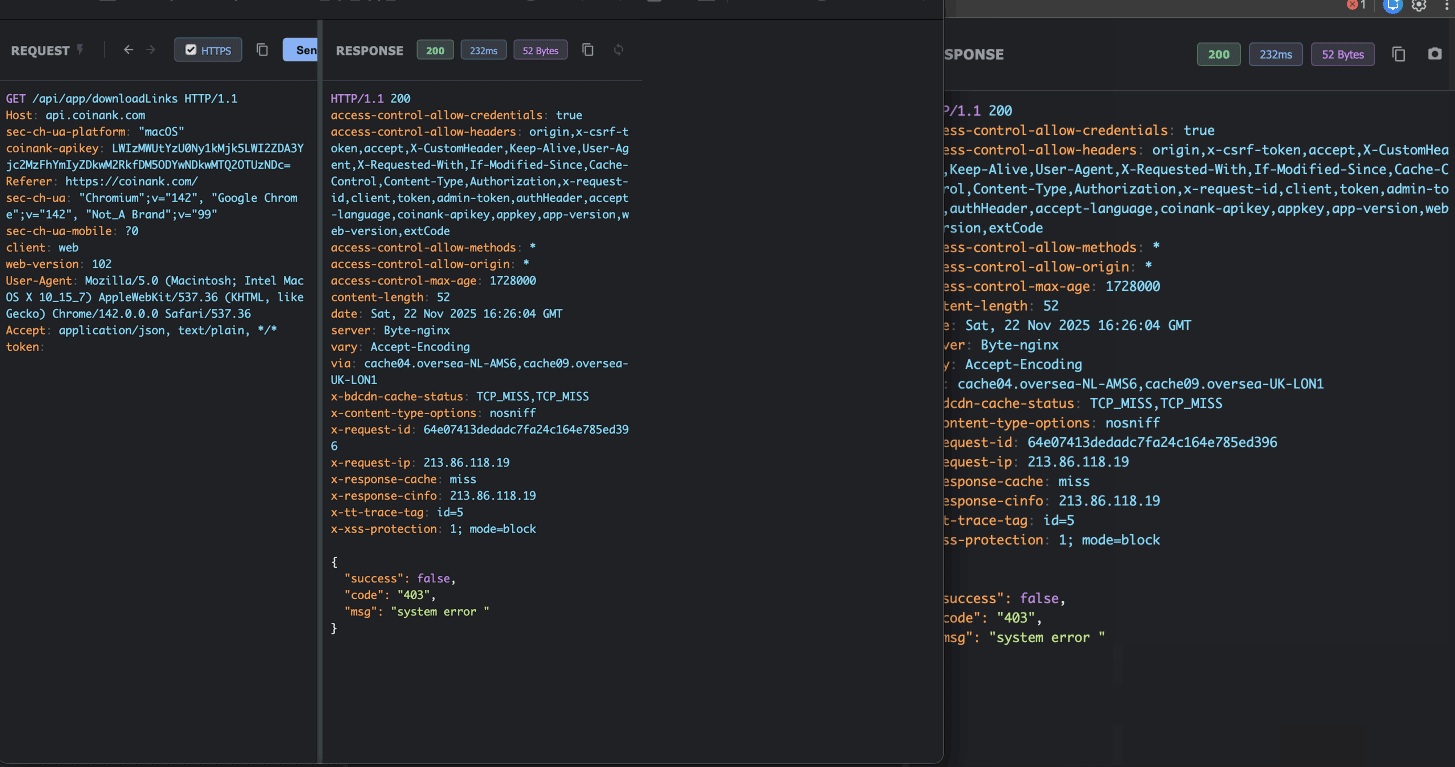
2. Capture & Replay Requests
rep+ automatically captures every HTTP request your browser makes. Click on any request to load it into the editor, where you can:
Modify the method, path, headers, or body
Replay the request with your changes
See the response instantly
This is perfect for testing authentication bypasses, parameter tampering, or API endpoint behavior, etc.
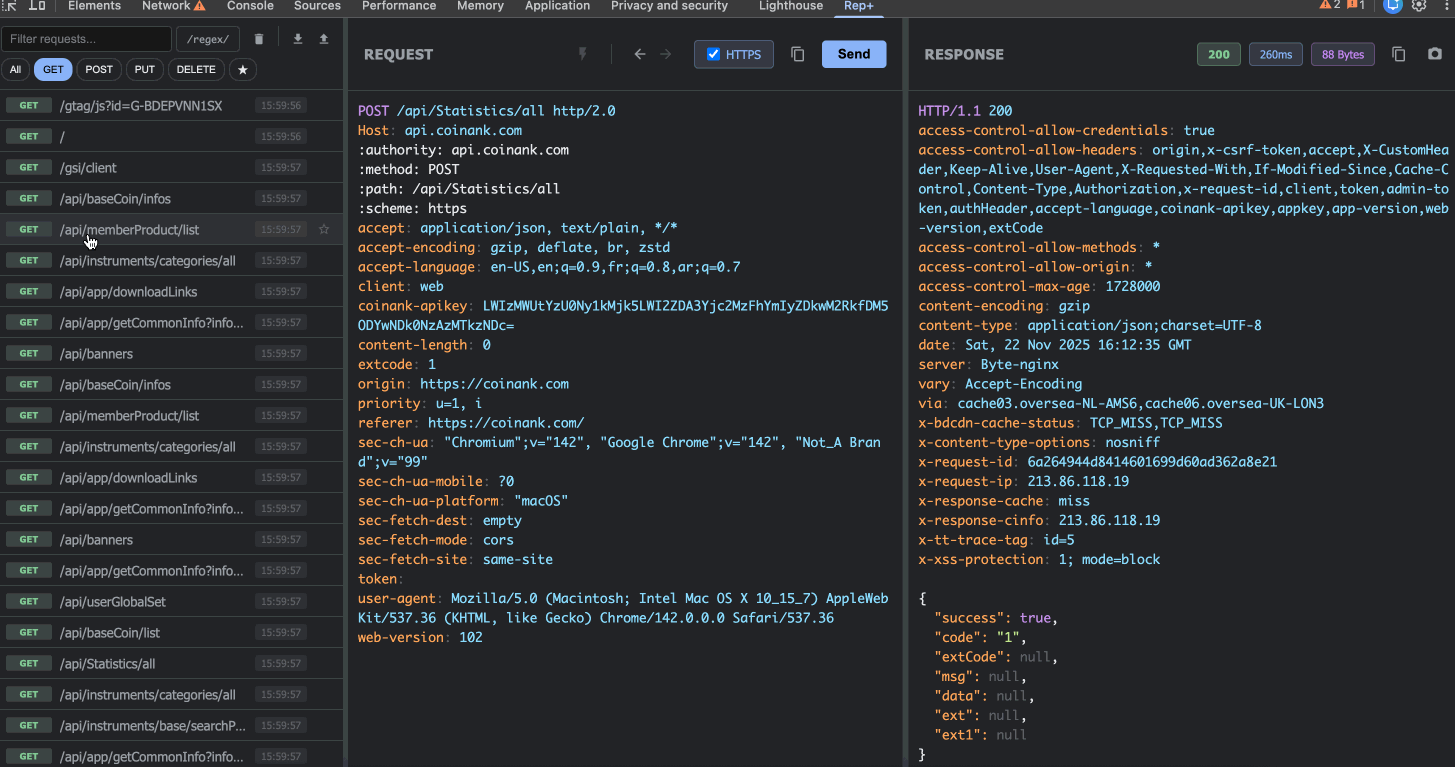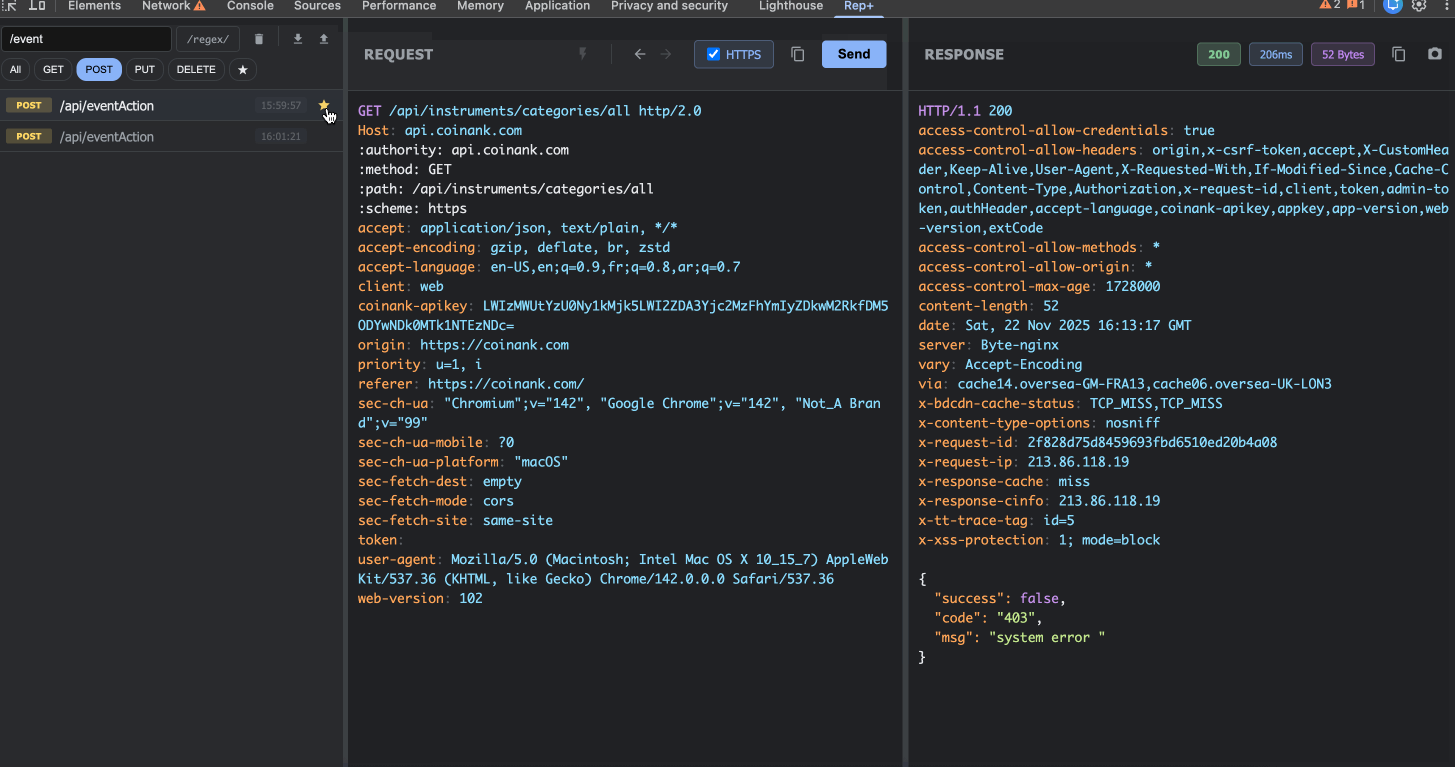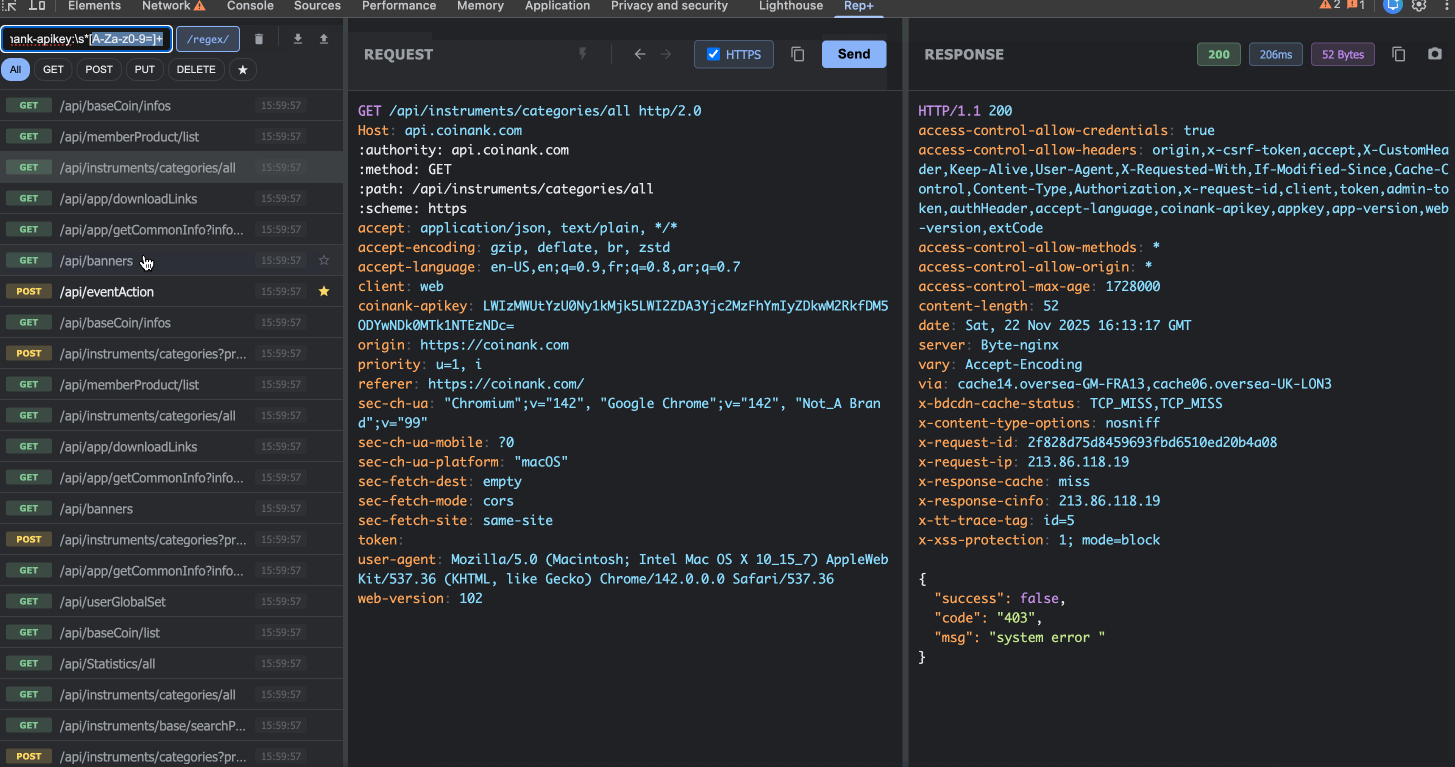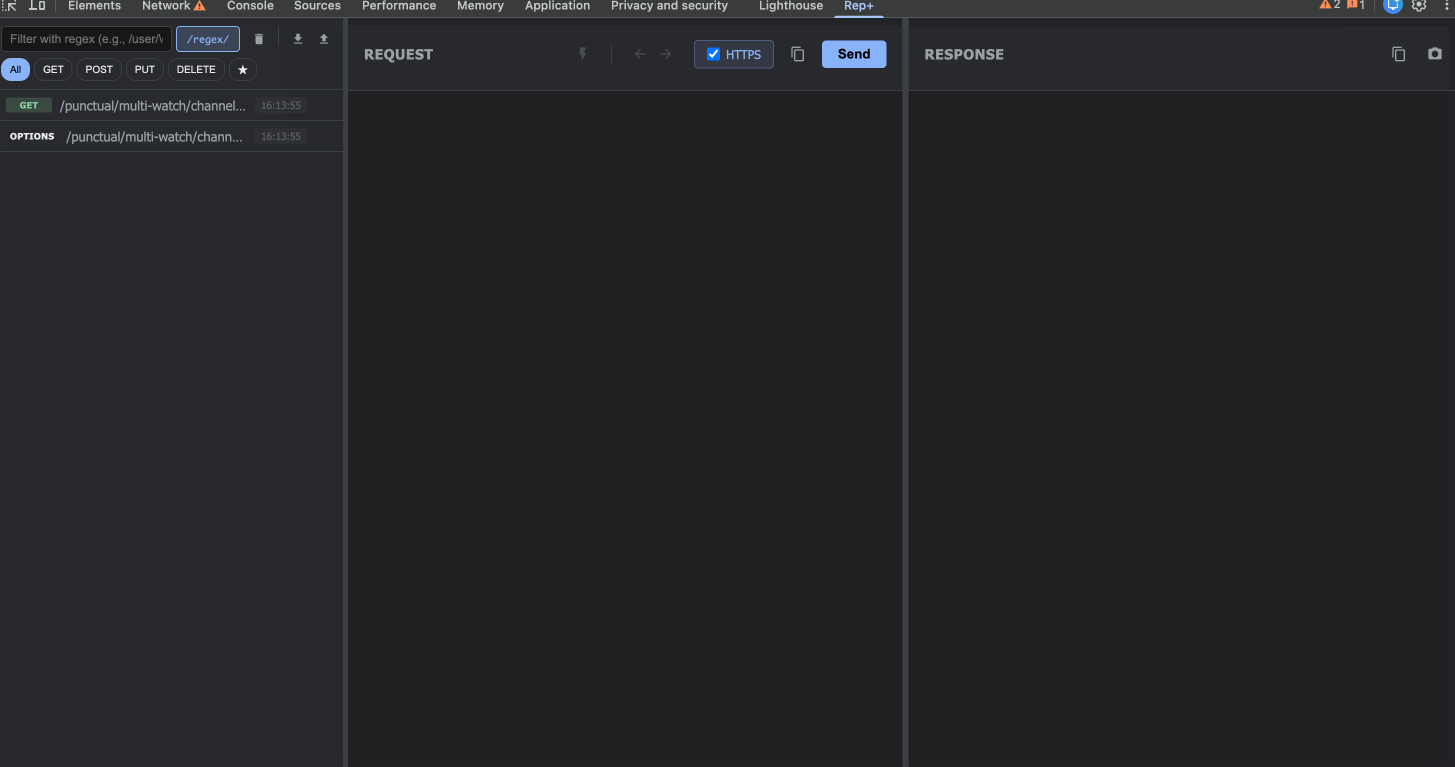
3. Powerful Filtering & Search
When you’re testing a complex web app, you might capture hundreds of requests. rep+ makes it easy to find what you need:
Search across URLs, headers, and body content
Regex Mode for advanced pattern matching (e.g., finding all requests with JWTs)
Method Filters (GET, POST, PUT, DELETE)
Star important requests to keep them at the top
4. Built-in Converters
Right-click on any text in the request editor to access instant encoding/decoding:
Base64 encode/decode
URL encode/decode
JWT decode (view payload without external tools)
Hex ↔ UTF-8 conversion
Will add more in the near future.
No more switching to CyberChef or online converters for simple transformations.
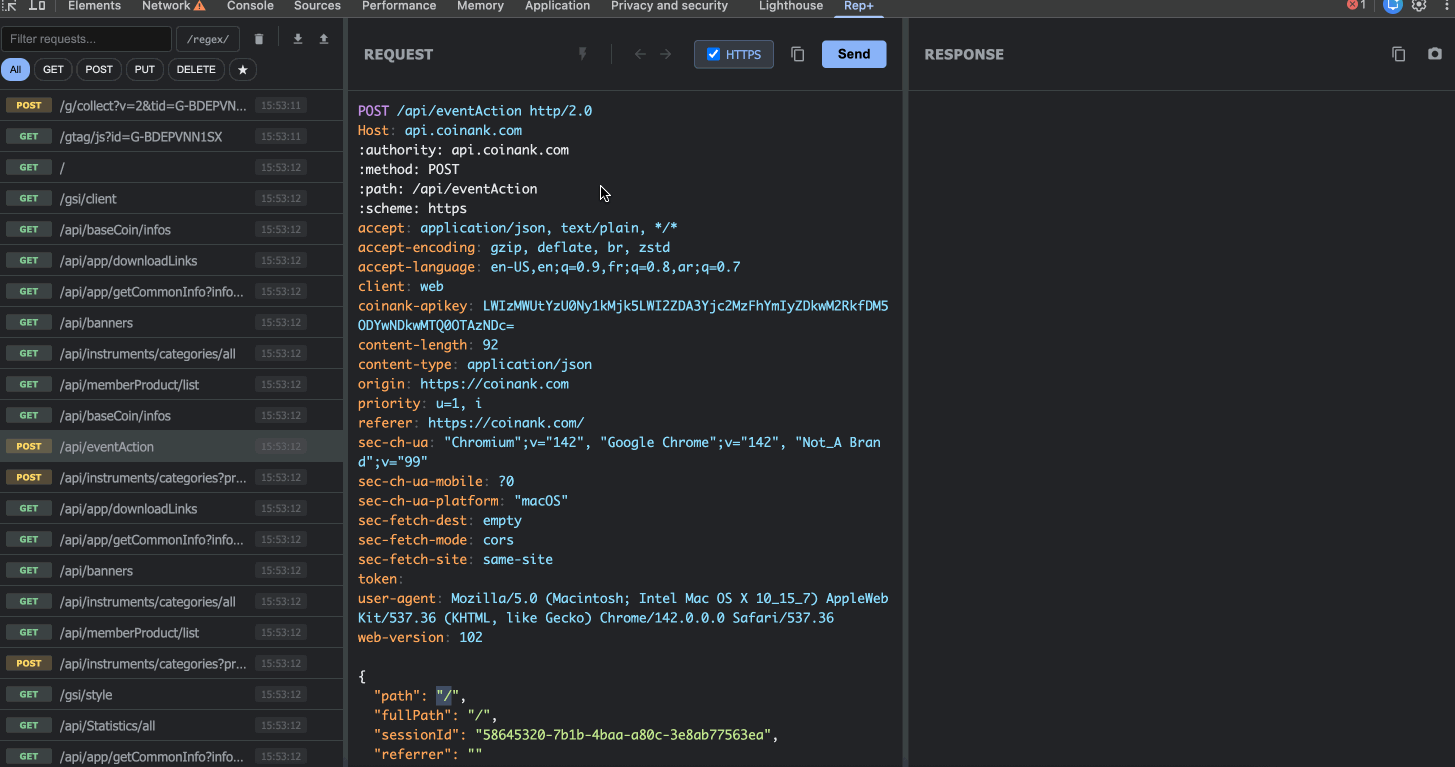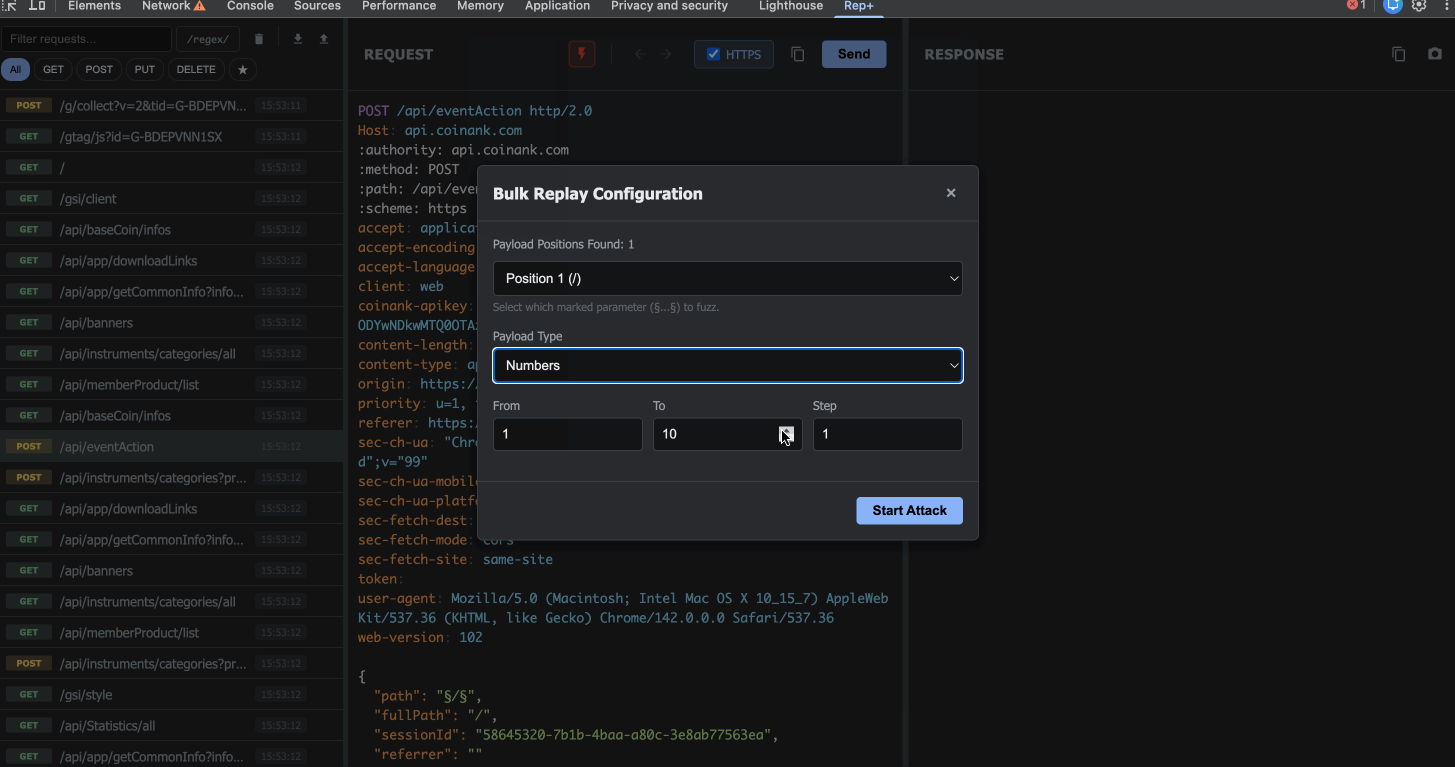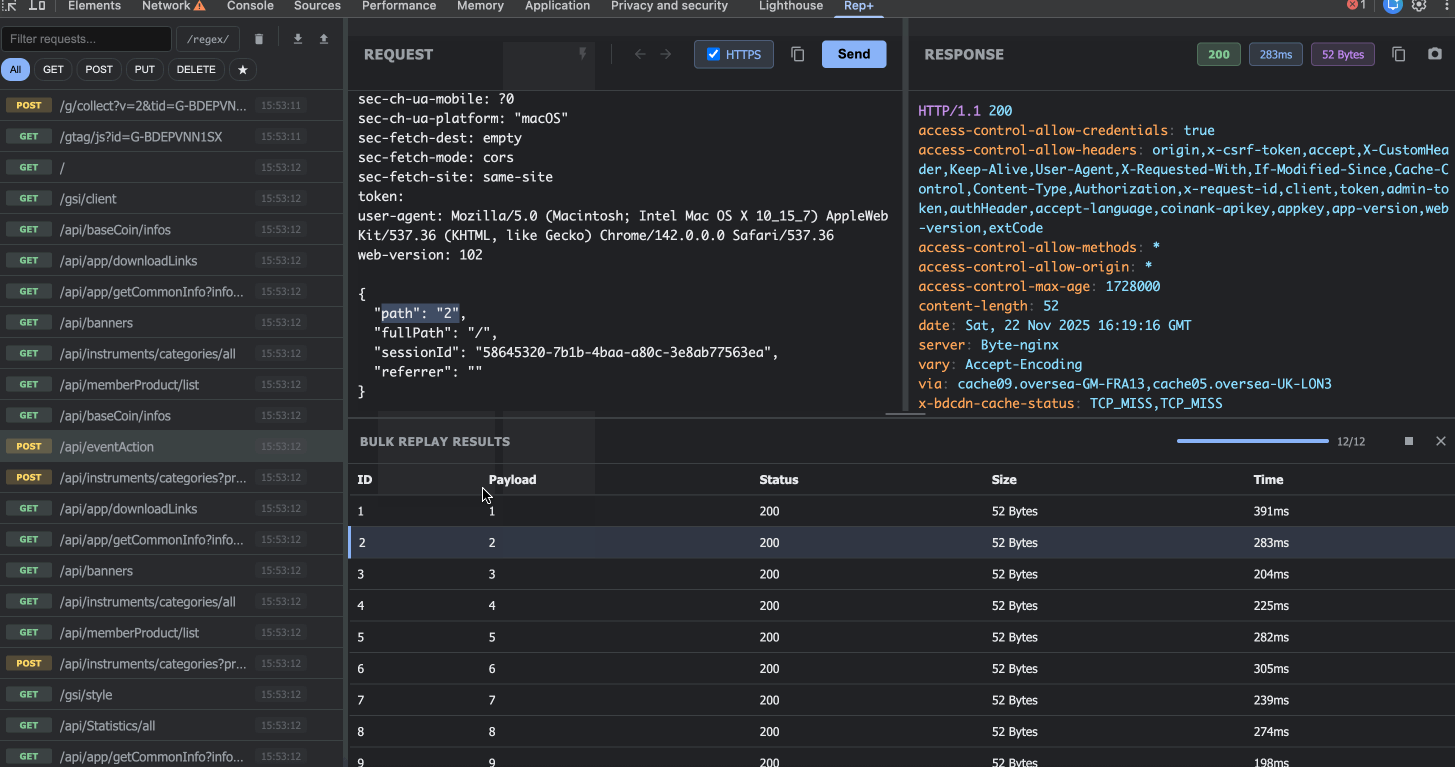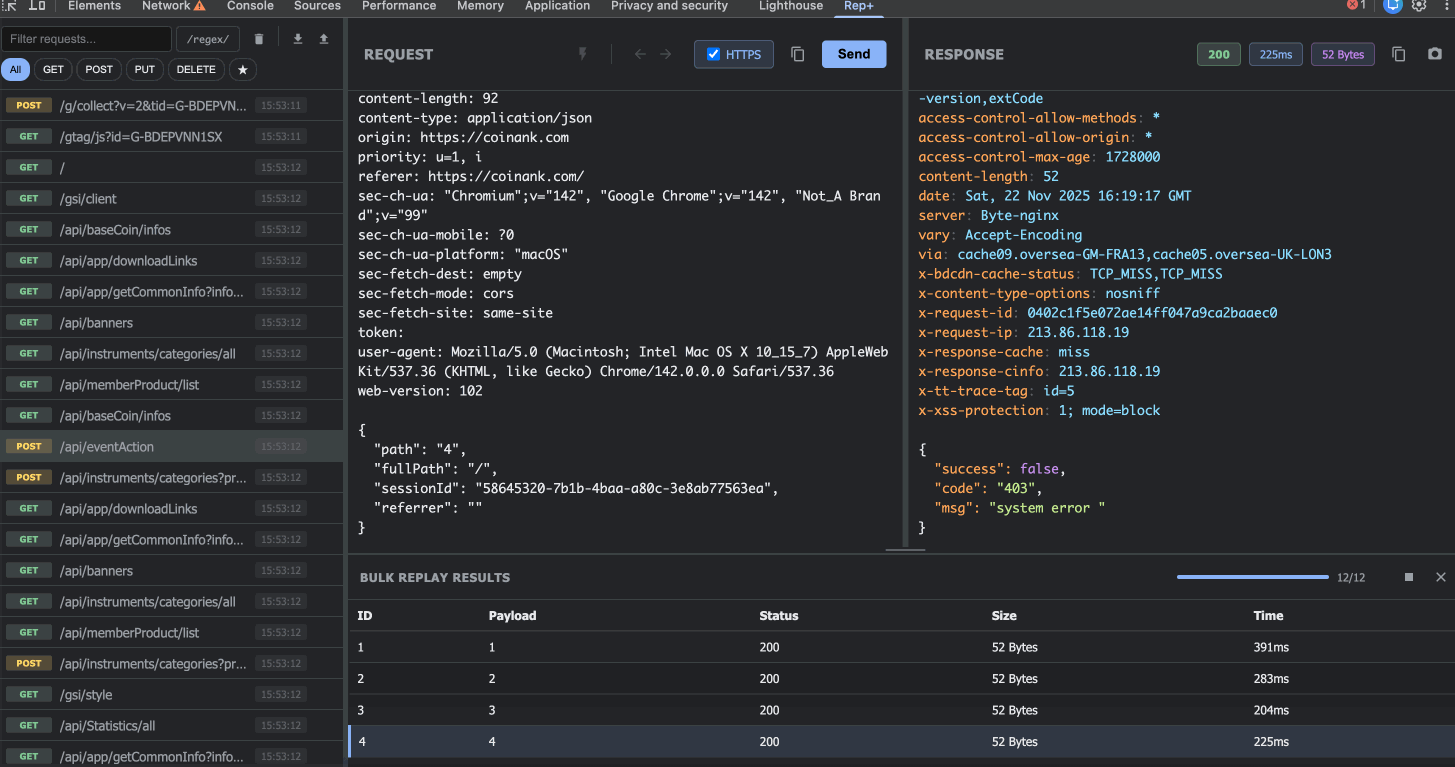
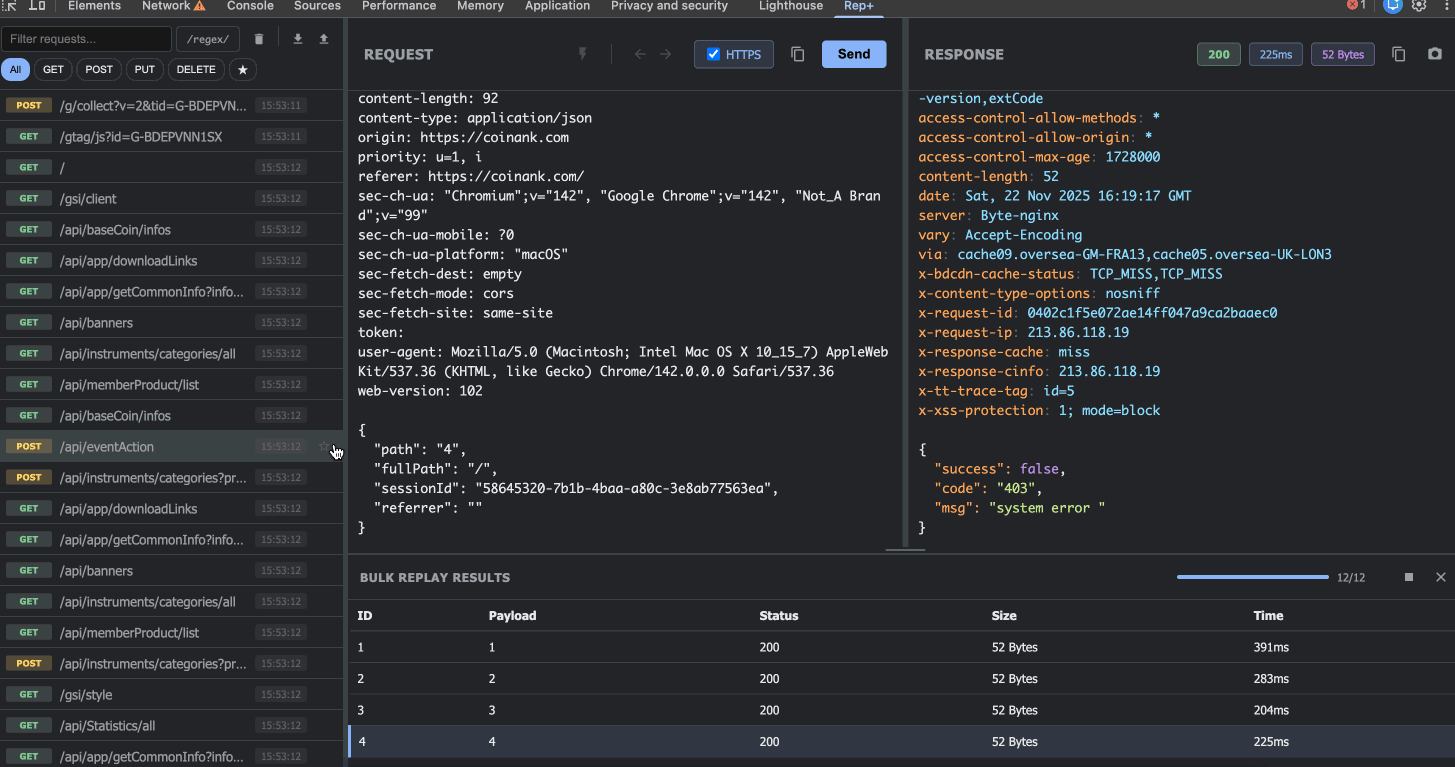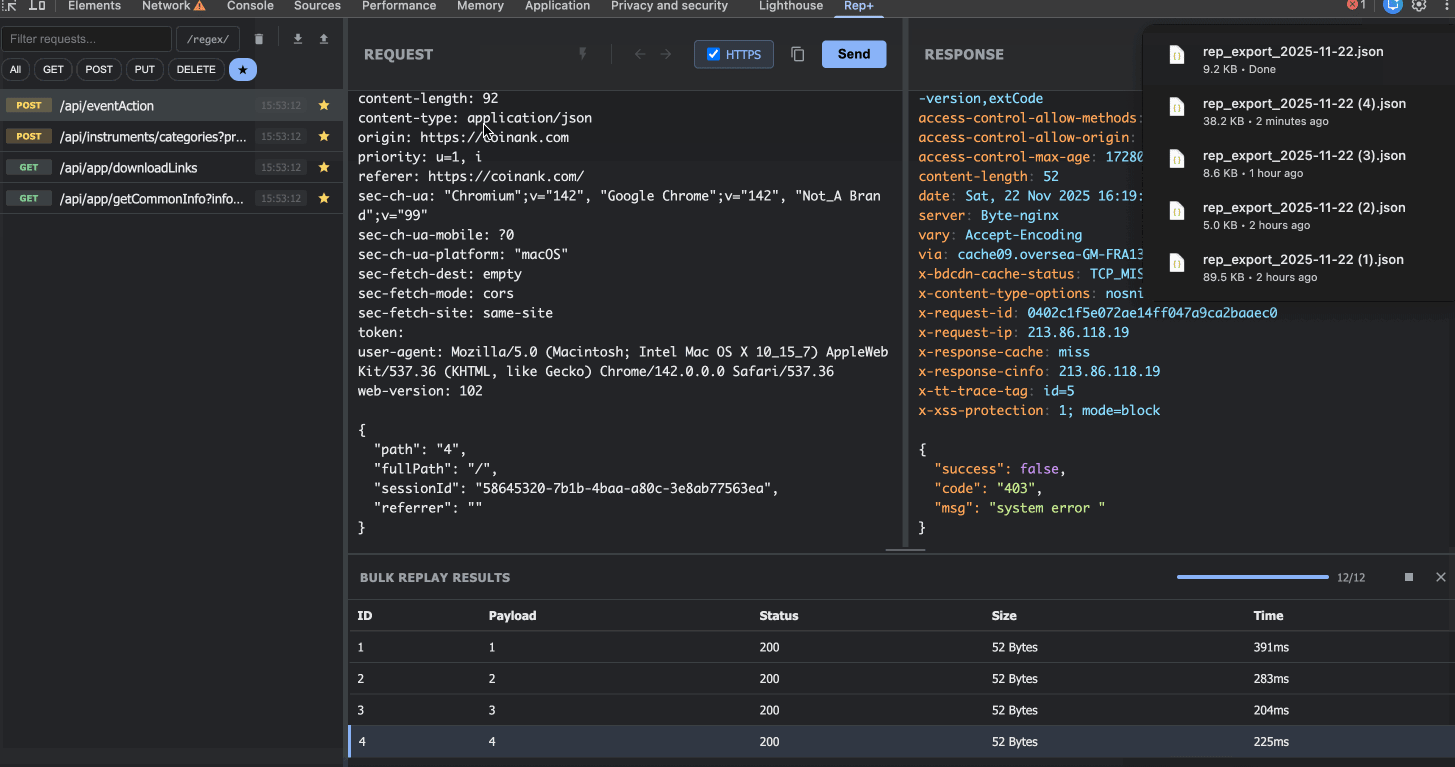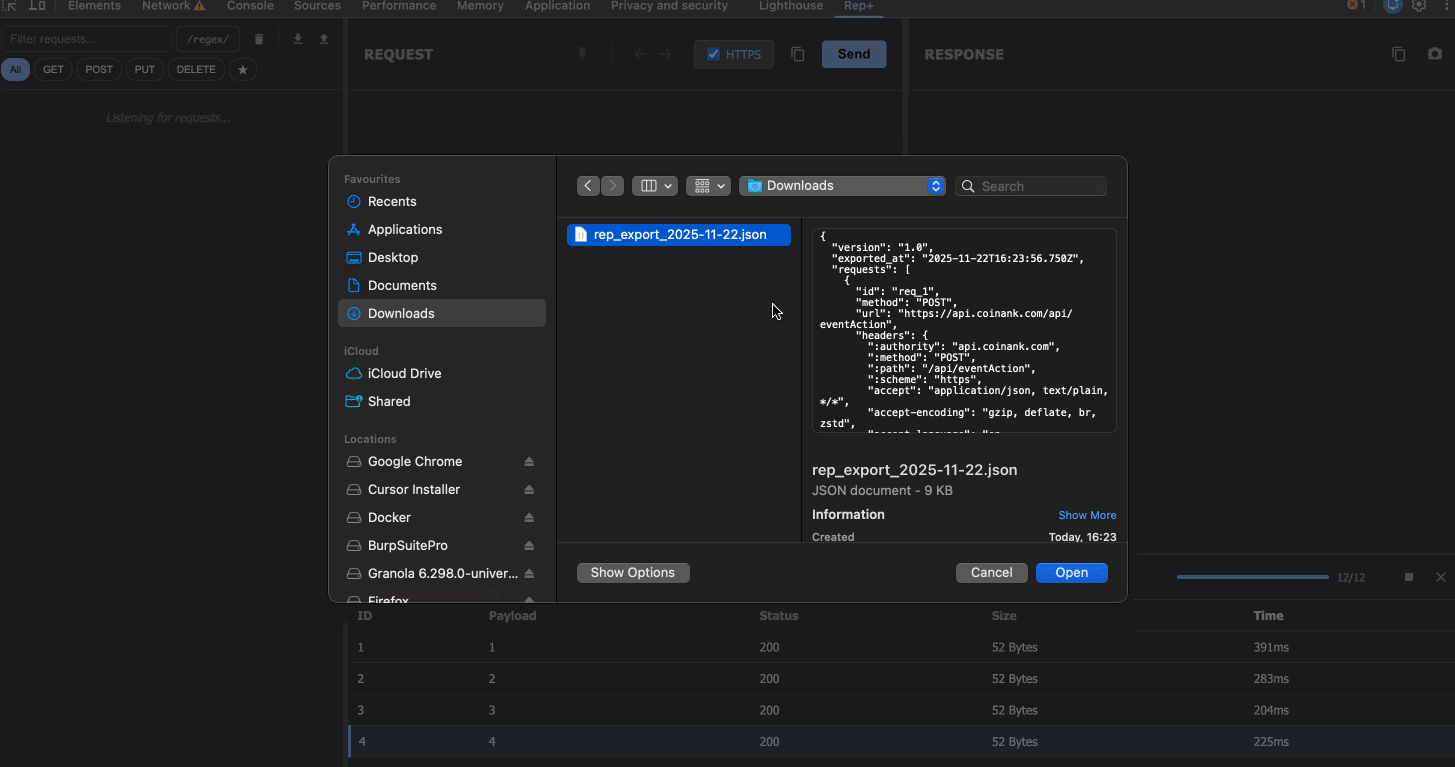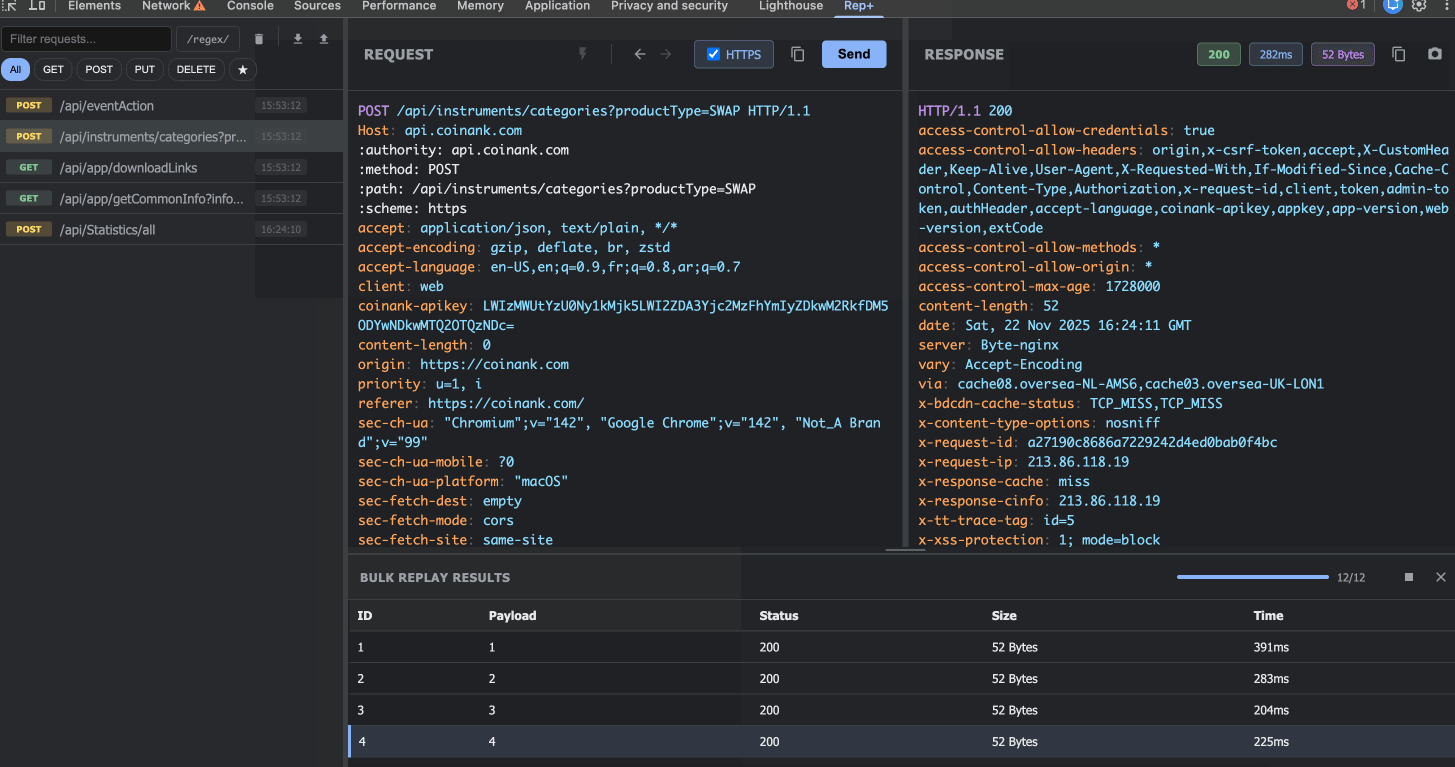
5. Bulk Replay (Intruder Mode)
This is where rep+ really shines. Need to fuzz a parameter? Mark it with `§` symbols (just like Burp Intruder), configure your payloads, and launch the attack.
You can:
Mark multiple parameters in a single request
Configure separate payloads for each position (simple lists or number ranges)
View detailed results for every attempt (status, size, time)
Click on any result to inspect the full request/response
This is incredibly useful for:
Testing for IDOR vulnerabilities (iterate through user IDs)
Brute-forcing parameters
Fuzzing inputs to find edge cases
6. Export & Import
Found something interesting? Export your requests as JSON to share with teammates or save for later. Import them back into rep+ anytime to continue your testing.
This makes collaboration seamless, no need to share Burp project files or screenshots.
7. Screenshots for Bug Reports
Built-in screenshot tool to capture the request/response pair. Perfect for documenting findings in bug bounty reports.
When to Use rep+ vs. Burp Suite
Use rep+ when:
You’re already in your browser and want to test something quickly
You need to replay a few requests with minor modifications
You want to fuzz a parameter without the overhead of Burp
You’re doing lightweight recon or API testing
You want a clean, distraction-free interface
Use Burp Suite when:
You need advanced features like Scanner, Collaborator, or Extensions
You’re doing deep penetration testing with complex workflows
You need to intercept and modify traffic from non-browser applications
You’re working on a collaborative project with shared state
Think of rep+ as your quick-draw tool for browser-based testing, and Burp as your heavy artillery for comprehensive assessments.
Real-World Use Case: Testing an API Endpoint
Let me walk you through a quick example of how I use rep+ in my daily workflow.
I’m testing a web app and I notice an API call to /api/user/profile?id=123. I want to see if I can access other users’ profiles by changing the `id` parameter.
With Burp Suite, I would:
Launch Burp
Configure my browser to use Burp’s proxy
Navigate to the page
Find the request in Burp’s HTTP history
Send it to Repeater
Modify the `id` parameter
Send the request
With rep+, I:
Open DevTools (`F12`)
Switch to the rep+ tab
Click on the `/api/user/profile` request (already captured)
Change `id=123` to `id=124` in the editor
Click Send
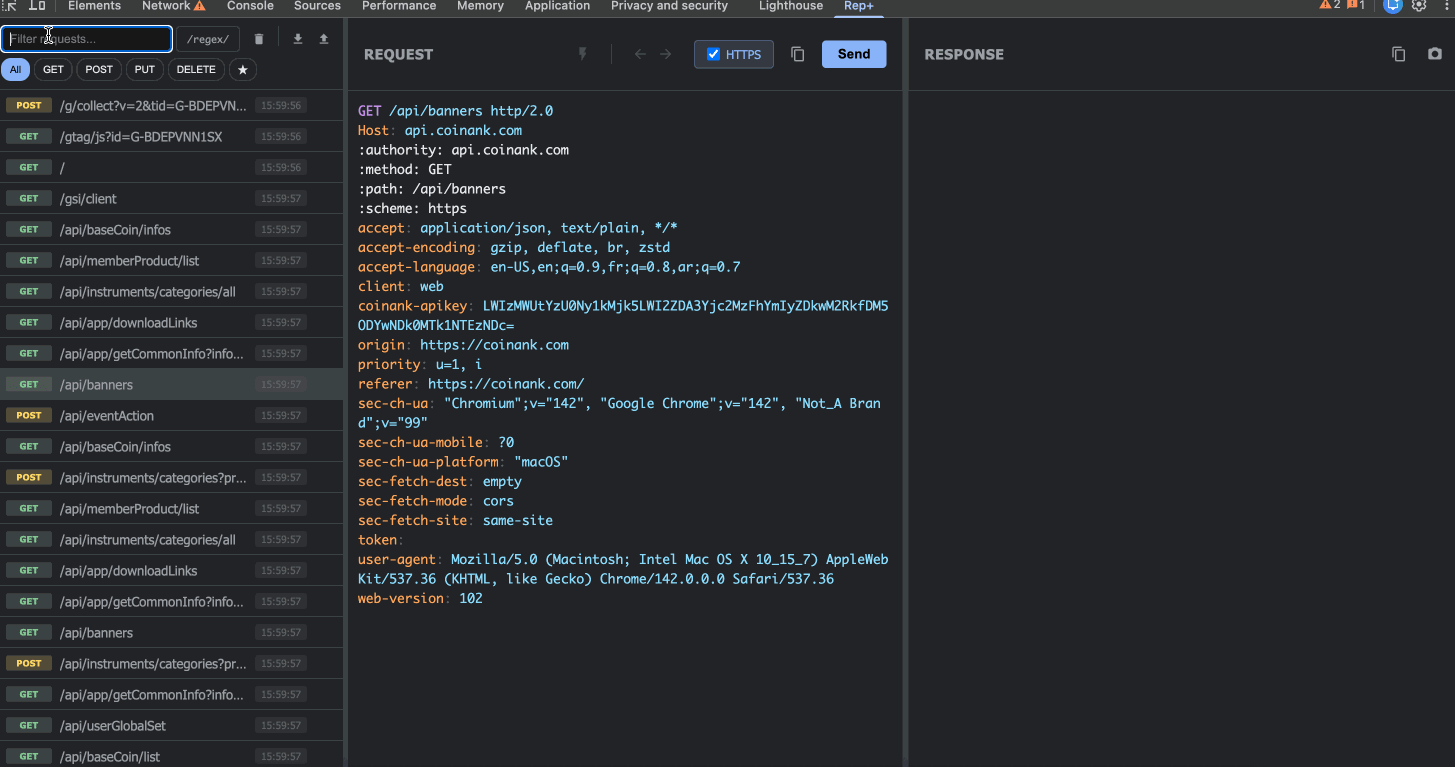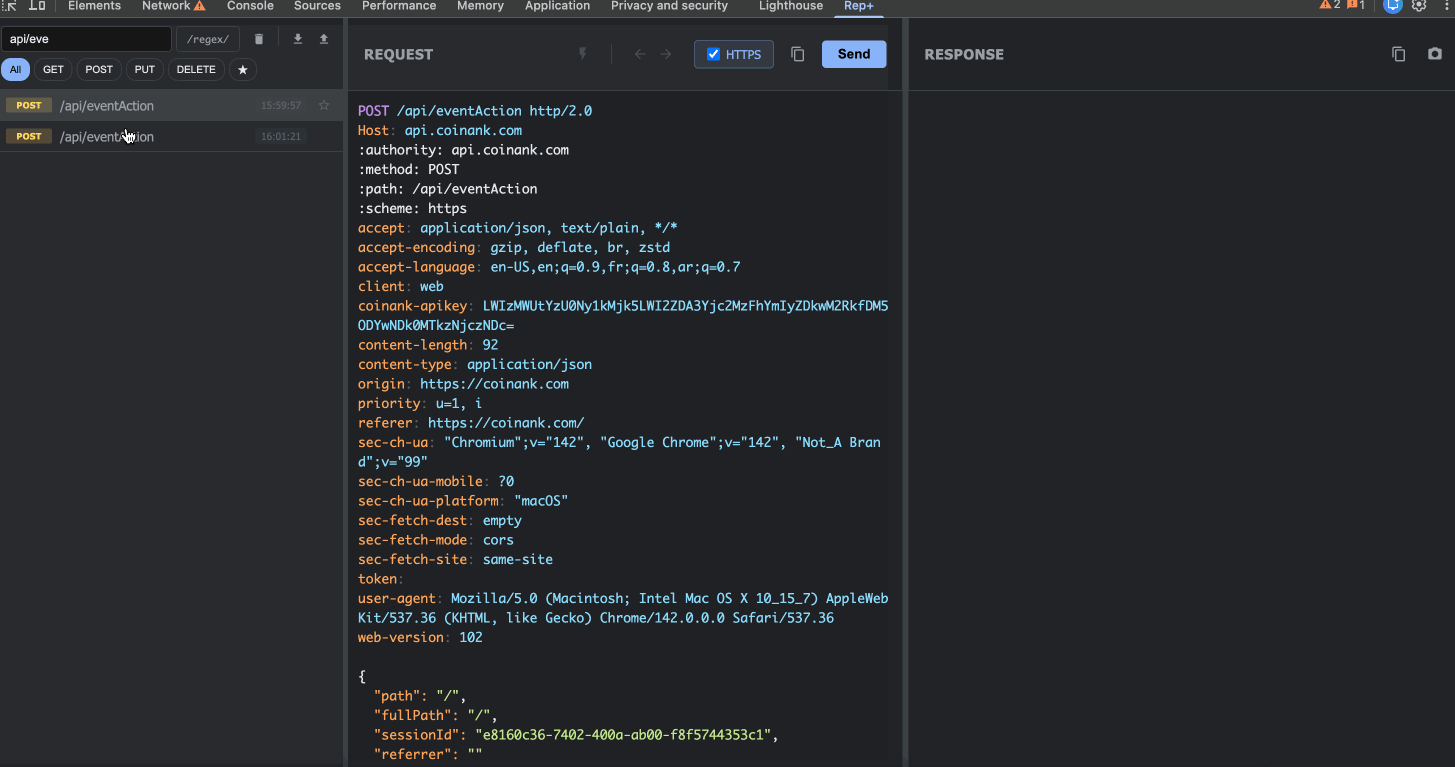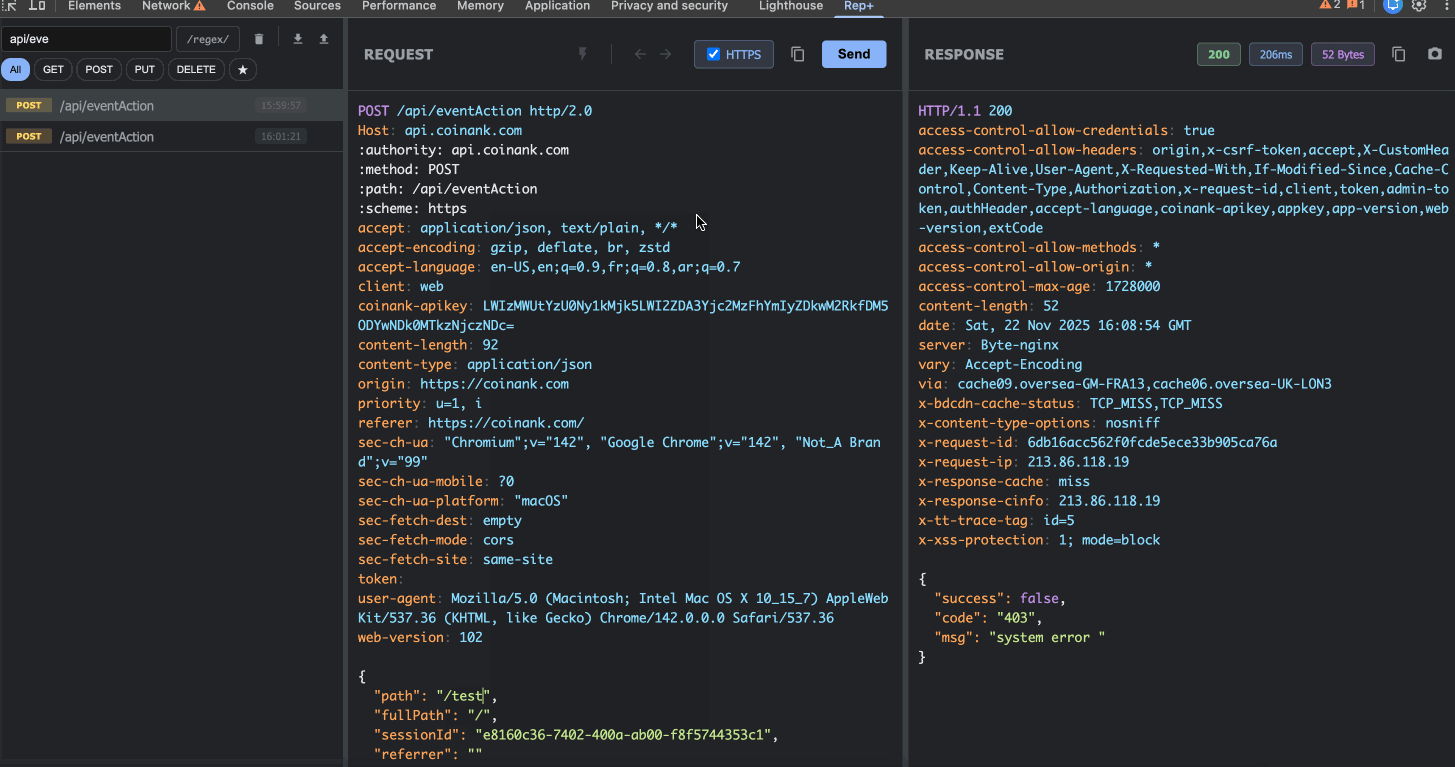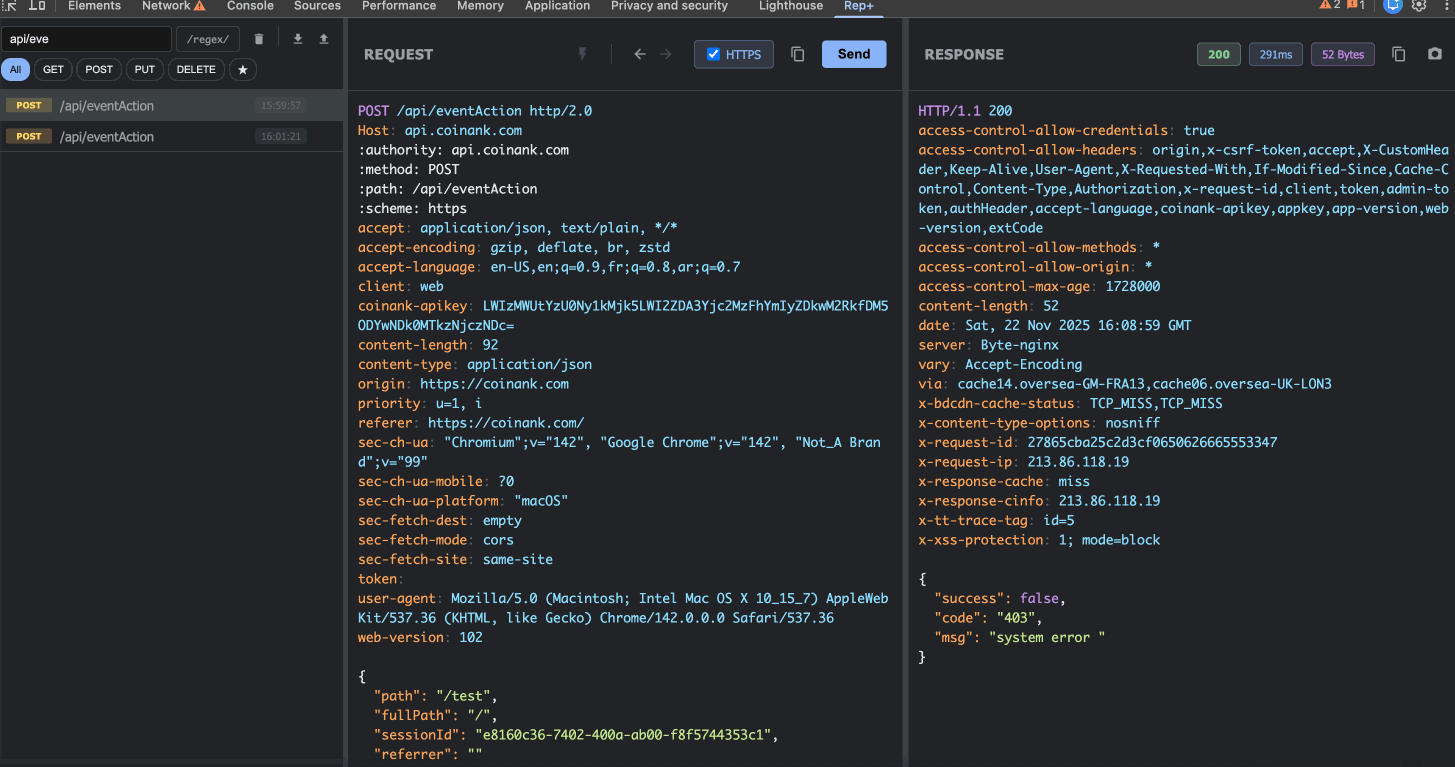
Done. No context switching, no proxy configuration, no friction.
If I want to test 100 different user IDs, I can use Bulk Replay:
1. Mark the ID with `§123§`
2. Click the lightning bolt (Attack) button
3. Configure a number range (1-100)
4. Launch the attack
5. Inspect results to find accessible profiles
Why I Built This
I built rep+ because I was frustrated with the overhead of using Burp Suite for simple tasks. As someone who does a lot of bug bounty hunting, I’m constantly switching between browsing, testing, and documenting. Having to launch a separate application, configure proxies, and manage certificates for every quick test was slowing me down.
I wanted a tool that:
Lives in my browser
Requires zero setup
Focuses on the core workflow: capture, modify, replay
Doesn’t sacrifice power for simplicity
rep+ is that tool. It’s not trying to replace Burp Suite, it’s trying to complement it by handling the 80% of tasks that don’t need Burp’s full feature set.
Open Source & Community
rep+ is open source and available on https://github.com/bscript/rep. I built it with the help of LLMs (Gemini 3), and I’m excited to see how the community uses and improves it.
If you have feature requests, bug reports, or just want to share how you’re using rep+, feel free to open an issue or submit a pull request.
Try It Out
If you’re a security researcher, bug bounty hunter, or developer who frequently tests web apps, give rep+ a try. It might just become your go-to tool for quick browser-based testing.
Happy hacking! 🔒⚡
---
Have you tried rep+? What features would you like to see next? Let me know in the comments or on GitHub, or reach out to me on X: @BourAbdelhadi.
.png)



![Overview of the Nvidia RTX Branch of Unreal Engine 5.6 [video]](https://www.youtube.com/img/desktop/supported_browsers/firefox.png)
