The Raspberry Pi RP2350 dual-core Arm/RISC-V has gotten a new version – A4 stepping – addressing bugs and security vulnerabilities, notably the infamous E9 GPIO erratum and glitching bugs in the A2 stepping identified by the 2024 Hacking Challenge.
Both RP2350A and RP2350B variants will benefit from the new stepping and be marked RP2350A0A4 and RP2350B0A4, respectively. The company also announced the availability of the 2MB flash variants, the RP2354A and RP2354B (unveiled in March 2025), that do not require flash on the board.
 Raspberry Pi RP2350A A4 stepping
Raspberry Pi RP2350A A4 stepping
RP2350 A4 stepping highlights:
- Fixes
- Glitching bugs identified in the 2024 Hacking Challenge. Exploits required physical access to the chip.
- The E9 GPIO erratum related to GPIO pull-ups.
- A4 stepping is a drop-in replacement for the earlier A2 stepping.
- 5V-tolerant GPIOs; Note: the chip must remain powered while 5V IOs are used (See updated datasheet for details)
- RP2354A and RP2354B variants with 2MB of stacked-in-package QSPI flash
 E9 GPIO Erratum Fix (A2 vs A4)
E9 GPIO Erratum Fix (A2 vs A4)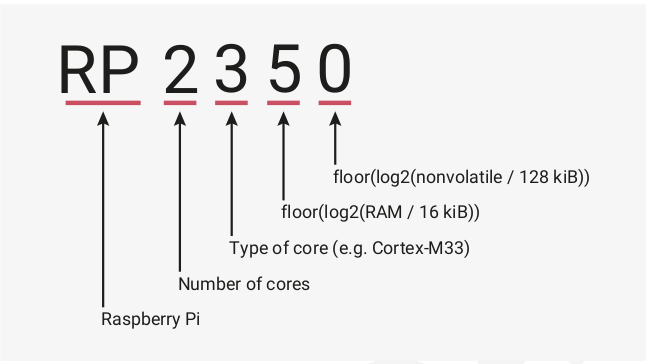 RP2350 naming convention explains why RP2354 has 2MB flash (and not 4MB flash)
RP2350 naming convention explains why RP2354 has 2MB flash (and not 4MB flash)
An important note is that the new A4 stepping of the RP2350 microcontrollers will only work with version 2.1.0 or later of the pico-sdk, so make sure your firmware is updated to support the new versions of the MCU.
While on the subject of software support, Raspberry Pi also introduced version 2.2.0 of pico-sdk, pico-examples, and picotool with:
- Various bug fixes, documentation improvements, and new features.
- Hardened AES decryption code with high resistance against side-channel attacks.
- Support for self-decrypting binaries (AES encryption). The encrypted binary will embed a bootloader that will decrypt your code/data to RAM before running.
- New Raspberry Pi RP2350 examples for encryption, OTA (over-the-air) update, and UART bootloading.
 Raspberry Pi RP2350B A4 stepping
Raspberry Pi RP2350B A4 stepping
Since security is always evolving, the company also announced the RP2350 Hacking Challenge 2. This follows the 2024 RP2350 Hacking Challenge, where several security bugs were found and fixed in the A4 stepping. The British company believes its new hardened AES implementation is resistant to side-channel attacks (SCA), and challenges people to prove them wrong.
The company also released price information for all variants of the RP2040 and RP2350 microcontrollers.
| Single unit7-inch reel13-inch reel | |||
| RP2040 | $1.00 | $0.80 | $0.70 |
| RP2350A | $1.10 | $0.90 | $0.80 |
| RP2350B | $1.20 | $1.00 | $0.90 |
| RP2354A | $1.30 | $1.10 | $1.00 |
| RP2354B | $1.40 | $1.20 | $1.10 |

Jean-Luc started CNX Software in 2010 as a part-time endeavor, before quitting his job as a software engineering manager, and starting to write daily news, and reviews full time later in 2011.
Support CNX Software! Donate via cryptocurrencies, become a Patron on Patreon, or purchase goods on Amazon or Aliexpress. We also use affiliate links in articles to earn commissions if you make a purchase after clicking on those links.
.png)




