In late May, two particularly interesting Chinese datasets appeared for sale in posts on DarkForums, an English-language data breach and leak forum that has become popular since BreachForums went dark in mid-April. These two posts, which we’re calling the VenusTech Data Leak and the Salt Typhoon Data Leak, had some interesting similarities. Both posts:
While the samples provided on DarkForums were relatively small in comparison to previous data leaks of a similar nature (including Chinese IT contractor leaks, such as TopSec and iSoon), the latest leaks provide critical pivot points for assessing the state and structure of the Chinese cybersecurity contractor ecosystem.
We wanted to take a moment to analyze these two recent posts, dive into the sample data, and make some connections between this activity and some overall trends we are observing in our research into the Chinese cybercriminal underground.
Analysis of the VenusTech Data Leak
VenusTech is a major IT security vendor in China with a focus on serving government clients. It was founded in 1996 and is traded on the Shenzhen Stock Exchange. They have previously documented ties to the hack-for-hire industry including procuring services from XFocus, who created the original Blaster worm in 2003, as well as providing startup funding to Integrity Tech, the company responsible for the offensive hacking activity associated with Flax Typhoon.
On May 17, a post relating to VenusTech was created by an account called “IronTooth” and titled “Chinese tech company venus leaked documents.” The IronTooth account appears to have been newly created and simply uses the default profile image for DarkForums. The full post text reads:
selling sourced leaked documents dump of chinese tech company. includes papers, products sold to government, accesses, clients and more random shit sold to highest bidder after 48h. crossposted.
Image 1: Screenshot of IronTooth’s post to DarkForums offering data from VenusTech for sale.
IronTooth then included 16 images which appear to be screenshots of various nonpublic VenusTech documents, presentations, spreadsheets, and contracts.
The documents that piqued our interest the most were the three spreadsheets towards the top of the post, which appear to contain details on Chinese government contracts and offensive services. The selected portions of the spreadsheets don’t contain column headers, complicating interpretations of the data, but two of them (Image 2 and Image 3) appear to contain detailed line items of collections targets and already hacked organizations.
Image 2: Screenshot showing a spreadsheet of entities that may correspond to either intelligence targets, access, or exfiltrated data. It appears to list organizations and regions, information about data types, and notes on amounts of hosts and daily active users. Below the original screenshot is an automated translation generated with Google Translate.
Image 3 also contains what look like cadences for data delivery. For example, one of the lines in Image 3 appears to suggest that VenusTech has access to the Korean National Assembly’s email server and is contracted to deliver four updates of data per month from this access to an unnamed customer at the price of 65,000 yuan (equivalent to about $9,000 USD).
Image 3: Screenshot showing what appears to correspond to intelligence targets, delivery schedules, and monthly prices. The first column contains country names, the second contains organization names, the third contains what appear to be service types, and the fourth appears to contain monthly data delivery quotas and additional stipulations. The final column appears to contain monthly prices ranging from 30,000 yuan per month to 85,000 yuan per month. Below the original screenshot is an automated translation generated with Google Translate.
Image 4 appears to contain contract information showing various Chinese government entities who are customers of VenusTech and additional information about their contracts.
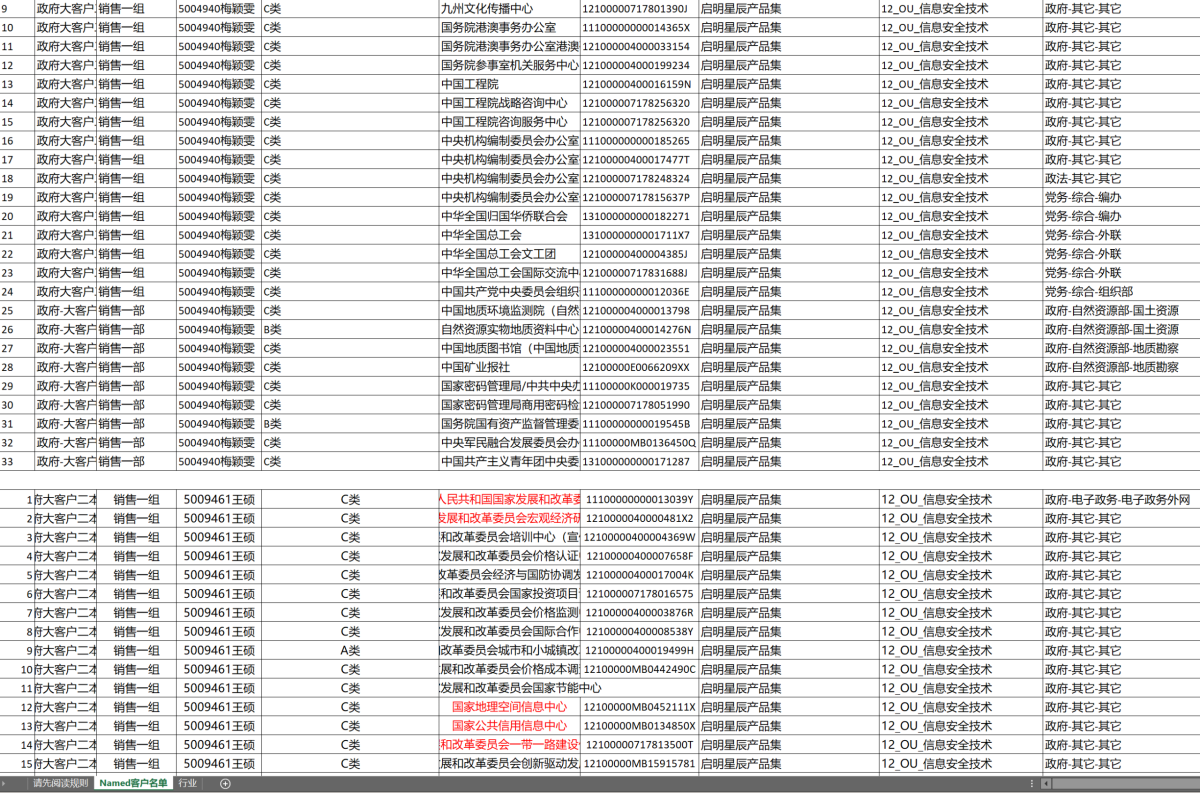
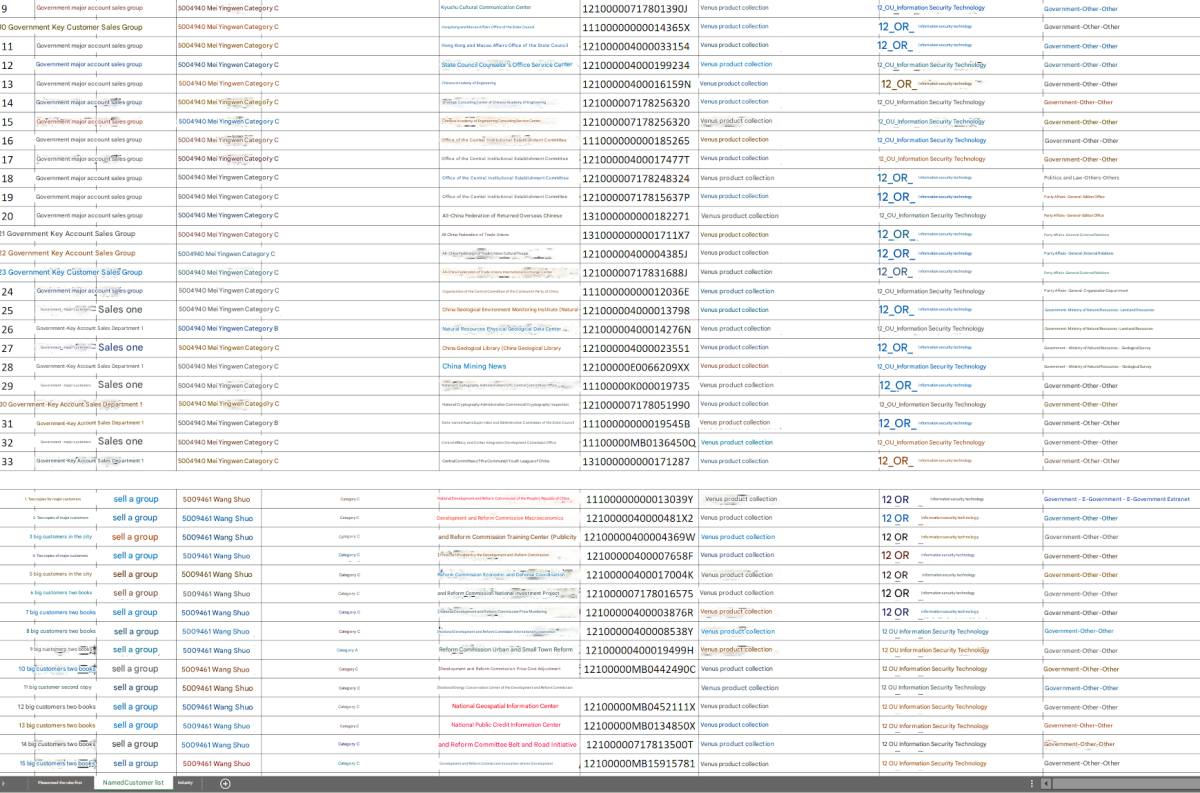
Image 4: Screenshot that appears to show Chinese government clients of VenusTech and additional information about their contracts. The column of alphanumeric strings in the center appear to be Unified Social Credit Codes. Below the original screenshot is an automated translation generated with Google Translate.
All together, these samples appear to provide evidence of specific offensive hacking services that VenusTech is providing to the Chinese government, as well as specific intelligence targets, including organizations in Hong Kong, India, Taiwan, South Korea, Croatia, and Thailand.
Analysis of the Salt Typhoon Data Leak
Salt Typhoon is a Chinese state-sponsored advanced persistent threat (APT) actor that is believed to be controlled by the Ministry of State Security (MSS). They are most notable for a series of intrusions into major US telecommunications companies and internet service providers that were discovered in late 2024. Since then, cybersecurity defenders have continued to discover additional intrusions into global telecommunications systems and universities attributed to Salt Typhoon, including, most recently, Viasat.
On May 18, a post relating to Salt Typhoon was created on DarkForums by user ‘ChinaBob’; their profile picture appears to be the titular character from an early-2000s era Chinese children’s cartoon called the Legend of Nezha. The username ChinaBob is reminiscent of the username ChinaDan, which was used by the account that posted the Shanghai National Police (SHGA) database for sale on BreachForums in 2022. The post is titled “Chinese government hacking group [Salt Typhoon]: Banking Data + Internal Files.”
The body of the post begins:
selling first-hand data from hacking companies working for the central government. Data includes employee data, financial data of companies and banking data, router configurations of hacked routers with passwords and chats of employees and officials being investigated.
Data: CSV, XLSX, TXT, PDF
Region: China
News Article: t[.]me/xhqcankao/17466
Price: $$$$$U (contact for price)
The post goes on to include multiple data samples, both in the original post and in three separate follow-up posts over the course of the next couple of days.
Image 5: Screenshot of ChinaBob’s original post to DarkForums offering Salt Typhoon data for sale.
Salt Typhoon employee data samples
The first sample appears to include names, Chinese national ID numbers, and phone numbers for seven Salt Typhoon employees (see Image 5). ChinaBob also followed up, apparently in response to people asking for additional samples, with data for an additional eight employees (see Image 6).
Image 6: Follow-up comment including additional employee data.
Our team searched for these identifiers in our extensive repository of breached and leaked data, as well as in a few SGKs (repositories of leaked and stolen PII, created by Chinese-language cybercriminal actors which allow for easy queryability of PII on Chinese citizens and users). Based on these searches, the data generally does appear to match with other sources of PII on Chinese individuals – additional sources confirm links between the listed names, national ID numbers, and phone numbers.
Compromised router samples
The next sample advertised by ChinaBob appears to show IP addresses of routers that were allegedly hacked by Salt Typhoon and associated usernames. The post indicates that the full dataset for sale will contain information on 242 hacked routers, including their passwords. ChinaBob also followed up with a fileshare link to a longer file including the full router configuration for one of the hacked routers (see Image 7).
Image 7: Follow-up comment including a link to a file on a filesharing site containing a full hacked router config.
Of the twelve total IP addresses, six appear to have internet-facing Cisco devices behind them, which Salt Typhoon has been known to compromise. Three more appear to have some other high-likelihood indicator of compromise – either based on unusually high fraud scores or being known as tied to residential proxy services.
While these indicators don’t necessarily equate to Salt Typhoon activity, they do indicate that there are unpatched and exploitable internet-facing devices behind these IPs that were very likely compromised by at least one cyber threat actor. Additionally, some of the listed router usernames do line up with some of the listed ISPs (for example, the IP address listed in ChinaBob’s sample with username lavaadmin is administered by the Lava International Limited ISP), making the data appear more credible.
Salt Typhoon transaction activity
The next sample shows transactions between various customers and three “seller” companies, which we hypothesize are associated with the Salt Typhoon threat activity. The spreadsheet (see Image 8) includes transactions between these three companies, transactions in which the three companies appear to be selling services to large, established Chinese cybersecurity vendors such as Qi’anxin (QAX) Legendsec and VenusTech, and transactions in which the three companies appear to be selling services to Chinese government and military units.
Image 8: Spreadsheet containing transaction data between the organizations allegedly behind the Salt Typhoon threat activity and their “government customers.”
The first transaction in this sample lists PLA Unit 61419 as the buyer, which has been affiliated with the ‘Tick’ threat activity group and was discovered in 2021 purchasing foreign antivirus products with the suspected goal of developing exploits for them. Another familiar listed buyer is the Institute of Information Engineering of the Chinese Academy of Sciences, a publicly owned academic institute which established China’s first cyber range, owns a small stake in iSoon, and has significant known ties to the Chinese hack-for-hire industry.
The three listed “seller” organizations in this sample include one which had already been named and sanctioned by the US Government for threat activity associated with Salt Typhoon – Sichuan Juxinhe Network Technology Company – as well as two additional business entities, Beijing Huanyu Tiangiong Information Technology Company Limited and Sichuan Zhixin Ruijie Network Technology Company Limited.
The cybersecurity analysis team Natto Thoughts published a deep-dive into Sichuan Juxinhe Network Technology Company earlier this year, concluding that they had characteristics resembling a front company of the MSS. Based on our initial searches, the two other companies listed as sellers in this spreadsheet also share some of the key characteristics of a front company including a limited digital footprint (including no public-facing website) and having a very small number of listed employees according to business intelligence databases.
Additionally, we see three of the individuals from ChinaBob’s sample employee lists reflected in public business registration records for Sichuan Zhixin Ruijie Network Technology Company Limited: Yu Yang (余洋), Yan Xue (闫雪), and Chen Zihao (陈梓浩). Based just on these three individuals, we can also find connections to public business registration records for four additional small companies not otherwise listed in this breach. Each of these additional four businesses also appear to have very limited digital footprints and few employees.
Using information derived from SpyCloud’s data holdings as well as business registration, we compiled basic business and identity details for each of the three individuals.
Chen Zihao (陈梓浩)
Male | 36 years old | Sichuan Province
National ID Number: 510623198909030310 | DOB: September 3, 1989
Phone Numbers: 18016122200, 15882059538
QQ: 523386132 | Weibo ID: 2608965270
Associated Business Registration Records:
- Sichuan Zhixin Ruijie Network Technology Co., Ltd.
- Sichuan Mubin Information Consulting & Edit Co., Ltd.
- Mubin (Deyang) Business Information & Edit Consulting Services Co., Ltd.
Yan Xue (闫雪)
Female | 35 years old | Liaoning Province
National ID number: 210882199001143029 | DOB: January 14, 1990
Phone Numbers: 13381199872, 17739345534
Weibo ID: 5746370894
Associated Business Registration Records:
- Sichuan Zhixin Ruijie Network Technology Co., Ltd.
- Shanghai Meicheng Network Technology Service Center
- Beijing Bole Human Resources Co., Ltd.
Yu Yang (余洋)
Male | 35 years old | Sichuan Province
National ID Number: 510623199002076710 | DOB: February 7, 1990
Phone Number: 13661368812
QQ: 517011513 | Weibo ID: 2759346040 | Email: [email protected]
Associated Business Registration Records:
- Sichuan Zhixin Ruijie Network Technology Co., Ltd.
Salt Typhoon contract data
ChinaBob also made a follow-up post including a technical service contract between Beijing Huanyu Tiangiong Information Technology Company Limited and Tongfang Co, a publicly traded state-owned enterprise based in Beijing. Tongfang Co, (Tsinghua Tongfang Co. Ltd.) is a high-tech information technology company that is closely associated with Tsinghua University and supplies military equipment to the PLA. In 2019, the China National Nuclear Corporation (CNNC), which oversees both China’s military and civilian nuclear programs, became a controlling stockholder of Tongfang Co.
Image 9: Page one of the final Salt Typhoon sample, of a service contract with a buyer.
Analysis and key takeaways from the latest Chinese data leaks
These two recent posts on DarkForums appear to contain nonpublic data sourced from tech companies within China’s robust hack-for-hire industry. While the public samples associated with these posts are nowhere near as large as the iSoon or TopSec leaks, they can still shed some additional light on the Chinese offensive cybersecurity contractor industry.
The “Salt Typhoon Data Leak” in particular appears to name two additional business entities as part of the threat activity cluster that have not yet been indicted or sanctioned by US authorities: Beijing Huanyu Tiangiong Information Technology Company Limited and Sichuan Zhixin Ruijie Network Technology Company Limited, in addition to the company that had already been named, Sichuan Juxinhe Network Technology Company.
While the origin of these leaks is uncertain, this data appearing for sale on a Western hacking forum fits into a few overarching trends that we have observed from monitoring Chinese cybercriminal communities:
Stay in the loop
Our team at SpyCloud Labs keeps close tabs on the Chinese cybercrime ecosystem. Sign up to stay in the loop with our latest research.
.png)



